 |
市場調查報告書
商品編碼
1906242
政府和公共部門網路安全:市場佔有率分析、行業趨勢和統計數據、成長預測(2026-2031 年)Government And Public Sector Cybersecurity - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2026 - 2031) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
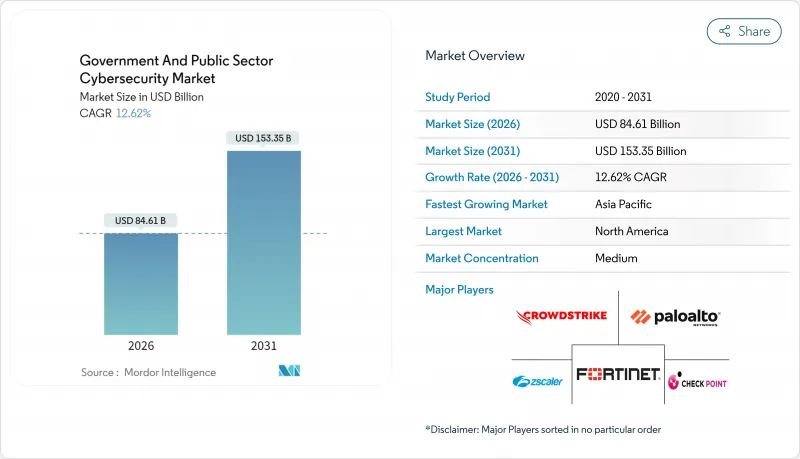
預計到 2025 年,政府和公共部門網路安全市場價值將達到 751.4 億美元,到 2026 年將成長至 846.1 億美元,到 2031 年將成長至 1533.5 億美元,在預測期(2026-2031 年)內複合成長率2%。
國家支持的網路攻擊日益增多、零信任政策加速推行以及抗量子密碼技術計劃正在重塑各級政府的採購重點。北約承諾將國內生產毛額的1.5%用於網路韌性建設,促使國防資源轉向新型威脅情報平台。同時,美國、歐盟和亞太主要經濟體的聯邦預算正在累計為端到端資安管理服務提供多年預算。支出正從被動的邊界防禦轉向利用人工智慧進行主動檢測,並透過外包來彌補人才短缺。因此,政府和公共部門的網路安全市場正經歷著供應商整合加劇、公私合營更加深入以及基於績效的服務等級協議長期合約盛行的趨勢。
全球政府與公共部門網路安全市場趨勢與洞察
國家支持的針對關鍵公共基礎設施的網路攻擊日益加劇
「鹽颱風」攻擊和其他國家級入侵聯邦網路和通訊基礎設施的案例,揭示了攻擊者如何利用供應鏈漏洞,持續訪問多個政府領域。安全團隊現在優先考慮持續監控、威脅搜尋和取證準備,而不是週期性的「時間點」掃描。 2024 年的供水事業停水事件凸顯了操作技術環境如何被武器化,從而導致實際的停水事故,促使各機構採用跨域安全架構。因此,預算分配越來越重視威脅情報、終端偵測和全天候事件回應服務。這導致聯邦、州和地方各級對能夠縮短從檢測到遏制週期的整合解決方案的需求持續成長。
政府零信任資金籌措指示及合規期限
美國國防資訊系統局 (DISA) 正在推行零信任框架,該框架要求對國防部網路上的所有交易進行身份驗證、設備安全維護和微隔離。如果未能按時完成,預算可能被沒收,因此各機構正在加快實施多因素身份驗證和持續診斷系統。州和地方政府也正在透過遵守聯邦標準來尋求配套資金,其中加州尤其設立了 2,260 萬美元的津貼基金,用於優先實施零信任架構。提供身分、終端和雲端工作負載整合平台的供應商在競標中獲得了優勢。同時,整合商正透過參考架構來凸顯自身優勢,這些架構將傳統資產對應到零信任成熟度模型。由於截止日期臨近 2026 年,採購管道正迅速被多年期、基於績效的合約填滿。
舊有系統整合和技術債務
數十年的漸進式升級導致政府機構擁有各自獨立的大型主機、專有通訊協定和缺乏文件的介面,這使得現代化計劃變得異常複雜。在這些分散的環境中實施零信任通常需要耗資龐大的資料遷移和並行操作,導致預算超出最初預期。在密西根州,勒索軟體攻擊者利用市政伺服器上過時的身份驗證控制,癱瘓了關鍵業務——這一案例表明了技術債務與營運風險之間的直接聯繫。一項聯邦審核發現,維修單一舊有系統的成本可能超過1億美元,迫使各機構採取漸進式實施,並依賴增加複雜性的補償性控制措施。這些限制減緩了先進安全框架的採用,並削弱了其對威脅緩解指標的即時影響。
細分市場分析
到2025年,網路安全領域的市場規模將達到212.7億美元,在政府和公共部門網路安全市場中保持28.31%的佔有率。這主要歸功於對現有邊界防火牆和入侵防禦系統的持續依賴,而這些系統仍然是採購標準。預算項目的延續反映了審核要求仍然優先考慮邊界可見性,儘管橫向移動有已知限制。同時,雲端安全市場規模將保持在133.4億美元,但預計到2031年將以13.05%的複合年成長率快速成長,因為政府機構正在將面向公民的服務遷移到FedRAMP和ENISA認證的託管服務上。身分和存取管理也持續擴展,零信任查核點點將安全重點重新轉向使用者檢驗和持續身分驗證。除了為支援安全遠程辦公策略而增加的終端投資外,由於大規模數位服務現代化,應用層測試的需求也在不斷成長。
預計到2031年,雲端安全將佔據政府和公共部門網路安全市場的重要佔有率,這表明混合架構正在推動對以資料為中心的控制以及靈活策略編配的需求。隨著後量子遷移時代的臨近,加密和資料安全升級正在加速,並影響採購規範,要求採用NIST認證的演算法。供應商正在提供整合金鑰管理服務和分析功能的解決方案,以簡化多重雲端環境中的部署。同時,應用程式安全閘道正在整合API姿態管理功能,以監控與第三方承包商的互動以及軟體供應鏈依賴關係。這些變化凸顯了安全解決方案正從基於點的產品轉向多層、可互通的安全套件,以適應不斷演進的架構藍圖。
截至2025年,本地部署系統將維持391.8億美元的收入,佔政府和公共部門網路安全市場佔有率的52.15%。國防指揮控制和公民身份儲存庫等敏感工作負載仍然依賴機構管理的資料中心,但隨著基於風險的分類模型使得非關鍵資料能夠遷移到雲端處理,這種情況正在改變。雲端採用市場規模將達到196.8億美元,年複合成長率(CAGR)為12.78%,這主要得益於付費使用制在緊急情況下滿足彈性服務需求的營運柔軟性。混合策略兼顧合規性與效率:各機構正在逐步淘汰單體系統,同時採用容器化微服務來開發新應用。
隨著對雲端運算的依賴日益加深,預計到2031年,混合架構將為政府和公共部門網路安全市場帶來161億美元的額外成長,這需要一個涵蓋身分、資料和網路控制的統一策略引擎。安全存取服務邊際(SASE)解決方案正逐漸成為連線的基礎,無論託管位置為何,都能透過檢查節點路由流量。供應商透過提供預先包裝的參考設計來脫穎而出,這些設計可以加速FedRAMP中等授權和NIS2合規性認證流程。同時,資金籌措框架現在專門為編配平台分配現代化津貼,這些平台可以標準化混合環境中的合規性報告,這表明在整個預測期內,混合環境將在新契約佔據主導地位。
區域分析
到2025年,北美將佔據政府和公共部門網路安全市場286.4億美元(38.12%)的佔有率,這主要得益於強力的聯邦指令、持續的津貼項目以及積極的公私資訊共用。財政部200億美元的PROTECTS框架體現了其對規模化合約的承諾以及對基於平台的解決方案的偏好。加拿大透過成立BOREALIS研究所,進一步鞏固了其在區域內的領先地位,該研究所致力於推進量子技術和人工智慧安全的發展。各州層級的法規,例如加州的物聯網網路信任標誌(IoT Cyber Trust Mark),建立了統一的標準,簡化了供應商認證流程。
到2025年,歐洲網路安全支出將達到202億美元,這主要得益於「數位歐洲」計畫中3.9億歐元的網路安全預算以及NIS2指令的實施。歐盟與美國聯邦風險與風險管理計畫(FedRAMP)在歐盟範圍內進行的互認工作,正在協調認證系統並加速跨境供應商整合。包括德國和法國在內的成員國正在分配主權雲端津貼,以確保資料本地化,同時受益於超大規模雲端的效率優勢。這些措施正在加速整合安全套件的轉型,這些套件包含合規性報告和零信任藍圖。
預計到2031年,亞太地區網路安全市場規模將達到155.7億美元,年複合成長率高達12.94%,將對政府和公共部門的網路安全市場產生重大影響。日本的《主動網路防禦法案》授權進行主動威脅搜尋,而韓國則致力於推廣人工智慧賦能的關鍵基礎設施偵測。澳洲的網路安全戰略強調區域合作,並拓展資訊共用平台。同時,東南亞新興經濟體正在建立國家級電腦安全事件應變小組(CSIRT),並利用捐助者和國內資金投資核心監控能力。中東和非洲地區雖然目前規模較小,但隨著其擺脫對石油的依賴,轉向保障智慧城市和能源計劃的安全,其網路安全預算正在迅速成長。這預示著即將迎來一波對操作技術(OT)分段和加密閘道器的競標浪潮。
其他福利:
- Excel格式的市場預測(ME)表
- 3個月的分析師支持
目錄
第1章 引言
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章 市場情勢
- 市場概覽
- 市場促進因素
- 國家主導的針對關鍵公共基礎設施的網路攻擊日益加劇
- 政府「零信任」資金籌措授權和合規期限
- 快速將市民服務遷移到雲端
- 擴大人工智慧驅動的公民服務會擴大攻擊面。
- 北約承諾將國內生產毛額的1.5%用於網路安全和關鍵基礎設施保護
- 透過NIS2/FedRAMP核准系統加速供應商整合
- 市場限制
- 舊有系統整合和技術債務
- 網路人才短缺與公共部門薪資差距
- 多重雲端下的資料主權之爭
- 分散採購和延長銷售週期
- 價值鏈分析
- 監管環境
- 技術展望
- 波特五力分析
- 新進入者的威脅
- 供應商的議價能力
- 買方的議價能力
- 替代品的威脅
- 競爭對手之間的競爭
- 宏觀經濟因素如何影響市場
第5章 市場規模與成長預測
- 按解決方案類型
- 網路安全
- 端點安全
- 雲端安全
- 應用程式安全
- 身分和存取管理 (IAM)
- 資料安全與加密
- 按部署模式
- 本地部署
- 雲
- 混合
- 按政府層級
- 國家/聯邦機構
- 國防與情報
- 州和政府部門
- 地方政府/城市、城鎮和鄉村
- 關鍵基礎設施管理署
- 依保全服務類型
- 諮詢顧問
- 資安管理服務(MSS)
- 事件回應和取證
- 培訓及宣傳活動
- 按地區
- 北美洲
- 美國
- 加拿大
- 墨西哥
- 南美洲
- 巴西
- 阿根廷
- 智利
- 其他南美洲
- 歐洲
- 德國
- 英國
- 法國
- 義大利
- 西班牙
- 其他歐洲地區
- 亞太地區
- 中國
- 日本
- 印度
- 韓國
- 澳洲
- 新加坡
- 馬來西亞
- 亞太其他地區
- 中東和非洲
- 中東
- 沙烏地阿拉伯
- 阿拉伯聯合大公國
- 土耳其
- 其他中東地區
- 非洲
- 南非
- 奈及利亞
- 其他非洲地區
- 中東
- 北美洲
第6章 競爭情勢
- 市場集中度
- 策略趨勢
- 市佔率分析
- 公司簡介
- Palo Alto Networks, Inc.
- CrowdStrike Holdings, Inc.
- Fortinet, Inc.
- Check Point Software Technologies Ltd.
- Zscaler, Inc.
- Okta, Inc.
- Splunk Inc.
- Tenable Holdings, Inc.
- CyberArk Software Ltd.
- Rapid7, Inc.
- Darktrace plc
- Mandiant LLC(Google Cloud)
- Trellix Corporation
- Booz Allen Hamilton Holding Corporation
- BAE Systems plc
- Thales SA
- Elastic NV
- Proofpoint, Inc.
- Ivanti, Inc.
- Cohesity, Inc.
第7章 市場機會與未來展望
The Government And Public Sector Cybersecurity Market was valued at USD 75.14 billion in 2025 and estimated to grow from USD 84.61 billion in 2026 to reach USD 153.35 billion by 2031, at a CAGR of 12.62% during the forecast period (2026-2031).

Escalating state-sponsored attacks, fast-tracking of zero-trust mandates, and quantum-resistant encryption projects are reshaping procurement priorities across every tier of government. NATO's pledge to spend 1.5% of GDP on cyber resilience is diverting defence resources toward new threat-intelligence platforms, while federal budgets in the United States, the European Union, and key Asia-Pacific economies are earmarking multi-year allocations that favour end-to-end managed security services. Spending is shifting from reactive perimeter protection to proactive detection powered by artificial intelligence, augmented by workforce outsourcing to offset talent shortages. As a result, the government and public sector cybersecurity market is experiencing broader vendor consolidation, deeper public-private partnerships, and longer contract tenures anchored in performance-based service-level agreements.
Global Government And Public Sector Cybersecurity Market Trends and Insights
Escalating State-Sponsored Cyber-Attacks on Critical Public Infrastructure
State-linked groups such as Salt Typhoon have breached federal networks and telecom infrastructure, demonstrating how adversaries leverage supply-chain compromises to gain persistent access to multiple government domains. Security teams now prioritise continuous monitoring, threat hunting, and forensic readiness, replacing periodic "point-in-time" scans. High-profile water-utility disruptions in 2024 revealed that operational technology environments can be weaponised to cause real-world service outages, prompting agencies to adopt cross-domain security architectures. Budget allocations, therefore, increasingly favour threat-intelligence feeds, endpoint detection, and 24 X 7 incident-response retainers. The cumulative effect is sustained demand for integrated solutions that shorten detection-to-containment cycles across federal, state, and local layers.
Government Zero-Trust Funding Mandates and Compliance Deadlines
The United States Defense Information Systems Agency is rolling out a zero-trust framework that requires identity verification, device hygiene, and micro-segmentation for every transaction across Department of Defense networks. Failure to meet timeline targets risks budget forfeiture, so agencies accelerate multi-factor authentication and continuous diagnostics deployments. State and local bodies align with federal standards to unlock matching funds, evident in California's USD 22.6 million grant pool that prioritises zero-trust implementations. Vendors offering consolidated platforms spanning identity, endpoint, and cloud workloads gain a competitive advantage in crowded tenders, while integrators differentiate through reference architectures that map legacy assets to zero-trust maturity models. As deadlines converge in 2026, procurement pipelines are filling rapidly with multi-year, performance-based contracts.
Legacy System Integration and Technical Debt
Decades of incremental upgrades have left agencies with siloed mainframes, proprietary protocols, and undocumented interfaces that complicate modernisation projects. Implementing zero-trust across such heterogeneous environments often demands costly data migrations and parallel operations, inflating budgets beyond initial estimates. In Michigan, ransomware actors exploited outdated authentication controls in municipal servers, paralysing essential operations and illustrating the direct link between technical debt and operational risk. Federal audits estimate individual legacy-system overhauls can cost more than USD 100 million, forcing agencies to stage rollouts and rely on compensating controls that add further complexity. These constraints slow the adoption of advanced security frameworks and dilute the immediate impact on threat-mitigation metrics.
Other drivers and restraints analyzed in the detailed report include:
- Rapid Cloud Migration of Citizen-Facing Services
- AI-Augmented Citizen Services Expanding Attack Surface
- Cyber-Talent Shortage and Public-Sector Pay Gap
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Network Security recorded USD 21.27 billion in 2025 and defended a 28.31% government and public sector cybersecurity market share on the strength of entrenched perimeter firewalls and intrusion-prevention systems that remain baseline procurement line items. Budget line continuity reflects audit mandates that still prioritise perimeter visibility despite known limitations against lateral movement. Yet Cloud Security generated only USD 13.34 billion but is forecast to grow faster at a 13.05% CAGR through 2031 as agencies transition citizen services into FedRAMP and ENISA-certified hosting. Identity and Access Management is also scaling as zero-trust checkpoints redistribute security emphasis toward user verification and continuous authentication. Rising endpoint investments underpin secure telework policies, while application-layer testing enjoys uplift from large-scale digital-service overhauls.
By 2031, Cloud Security is projected to claim a material share of the government and public sector cybersecurity market size, illustrating how hybrid architectures elevate demand for data-centric controls alongside flexible policy orchestration. Encryption and data-security upgrades accelerate as post-quantum migration deadlines approach, influencing procurement specifications to demand NIST-validated algorithms. Vendors are bundling key management as-a-service with analytics to simplify deployment across multi-cloud environments. In parallel, application-security gateways incorporate API posture management to police interactions with third-party contractors and software supply-chain dependencies. Combined, these shifts underscore a transition from single-point products to layered, interoperable security suites that map neatly to evolving architecture roadmaps.
On-premises systems retained USD 39.18 billion in revenue and 52.15% government and public sector cybersecurity market share during 2025. Sensitive workloads such as defence command-and-control and citizen identity repositories remain anchored in agency-controlled data centres, but the narrative is changing as risk-based classification models free less critical data for cloud processing. Cloud deployments, valued at USD 19.68 billion, are advancing at a 12.78% CAGR, fuelled by consumption-based pricing and the operational flexibility needed for elastic service demand during emergencies. Hybrid strategies bridge compliance with efficiency: agencies adopt containerised micro-services for new applications while gradually retiring monoliths.
As cloud confidence builds, hybrid architectures are forecast to add USD 16.1 billion to the government and public sector cybersecurity market size by 2031, requiring unified policy engines that span identity, data, and network controls. Secure access service edge solutions emerge as the connective tissue, routing traffic through inspection nodes regardless of hosting location. Vendors differentiate by offering pre-packaged reference designs that accelerate accreditation under FedRAMP Moderate and NIS2 compliance tracks. Meanwhile, funding frameworks now earmark modernisation grants specifically for orchestration platforms that normalise compliance reporting across mixed environments, signalling that hybrid will dominate new awards through the forecast window.
Government and Public Sector Cybersecurity Market Report is Segmented by Solution Type (Network Security, Endpoint Security, and More), Deployment Model (On-Premises, Cloud, and Hybrid), Government Level (National/Federal Agencies, Defense and Intelligence, and More), Security Service Type (Consulting and Advisory, Managed Security Services, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America contributed USD 28.64 billion and retained 38.12% of the government and public sector cybersecurity market in 2025 on the back of robust federal directives, sustained grant programmes, and active public-private information sharing. Treasury Department's USD 20 billion PROTECTS framework illustrates contract scale and an inclination for platform-based solutions. Canada is setting up the BOREALIS agency to advance quantum and AI security, further solidifying regional leadership. State-level regulation, such as California's IoT Cyber Trust Mark, creates harmonised baselines that streamline vendor certification pipelines.
Europe stood at USD 20.2 billion in 2025, propelled by the Digital Europe Programme's EUR 390 million cybersecurity budget and the forthcoming enforcement of NIS2 directives. EU-wide reciprocity efforts with U.S. FedRAMP align certification schemes, accelerating cross-border vendor consolidation. Individual member states, notably Germany and France, are allocating sovereign-cloud grants to ensure data localisation while benefitting from hyperscale efficiencies. These initiatives push the region toward integrated security suites that embed compliance reporting and zero-trust blueprints.
Asia-Pacific clocked USD 15.57 billion and is projected to record the highest 12.94% CAGR, adding significant heft to the government and public sector cybersecurity market by 2031. Japan's Active Cyber Defense bill authorises proactive threat hunting, while South Korea targets AI-enabled detection for critical infrastructure. Australia's Cyber Security Strategy emphasises regional partnerships, expanding opportunities for shared intelligence platforms. Simultaneously, emerging economies in Southeast Asia are setting up national CSIRTs, funnelling donor and domestic funds into core monitoring capabilities. Middle East and Africa, though smaller today, are quickly scaling post-oil diversification budgets to protect smart-city and energy projects, signalling an upcoming wave of tenders for operational-technology segmentation and encryption gateways.
- Palo Alto Networks, Inc.
- CrowdStrike Holdings, Inc.
- Fortinet, Inc.
- Check Point Software Technologies Ltd.
- Zscaler, Inc.
- Okta, Inc.
- Splunk Inc.
- Tenable Holdings, Inc.
- CyberArk Software Ltd.
- Rapid7, Inc.
- Darktrace plc
- Mandiant LLC (Google Cloud)
- Trellix Corporation
- Booz Allen Hamilton Holding Corporation
- BAE Systems plc
- Thales S.A.
- Elastic N.V.
- Proofpoint, Inc.
- Ivanti, Inc.
- Cohesity, Inc.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Escalating state-sponsored cyber-attacks on critical public infrastructure
- 4.2.2 Government "zero-trust" funding mandates and compliance deadlines
- 4.2.3 Rapid cloud migration of citizen-facing services
- 4.2.4 AI-augmented citizen services expanding attack surface
- 4.2.5 NATO pledge of 1.5 % GDP on cyber and critical-infra protection
- 4.2.6 NIS2 / FedRAMP reciprocity accelerating vendor consolidation
- 4.3 Market Restraints
- 4.3.1 Legacy system integration and technical debt
- 4.3.2 Cyber-talent shortage and public-sector pay gap
- 4.3.3 Multi-cloud data-sovereignty conflicts
- 4.3.4 Fragmented procurement and elongated sales cycles
- 4.4 Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Suppliers
- 4.7.3 Bargaining Power of Buyers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Impact of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Solution Type
- 5.1.1 Network Security
- 5.1.2 Endpoint Security
- 5.1.3 Cloud Security
- 5.1.4 Application Security
- 5.1.5 Identity and Access Management (IAM)
- 5.1.6 Data Security and Encryption
- 5.2 By Deployment Model
- 5.2.1 On-premises
- 5.2.2 Cloud
- 5.2.3 Hybrid
- 5.3 By Government Level
- 5.3.1 National/Federal Agencies
- 5.3.2 Defense and Intelligence
- 5.3.3 State/Provincial Departments
- 5.3.4 Local/Municipal Bodies
- 5.3.5 Critical Infrastructure Authorities
- 5.4 By Security Service Type
- 5.4.1 Consulting and Advisory
- 5.4.2 Managed Security Services (MSS)
- 5.4.3 Incident Response and Forensics
- 5.4.4 Training and Awareness
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 South America
- 5.5.2.1 Brazil
- 5.5.2.2 Argentina
- 5.5.2.3 Chile
- 5.5.2.4 Rest of South America
- 5.5.3 Europe
- 5.5.3.1 Germany
- 5.5.3.2 United Kingdom
- 5.5.3.3 France
- 5.5.3.4 Italy
- 5.5.3.5 Spain
- 5.5.3.6 Rest of Europe
- 5.5.4 Asia-Pacific
- 5.5.4.1 China
- 5.5.4.2 Japan
- 5.5.4.3 India
- 5.5.4.4 South Korea
- 5.5.4.5 Australia
- 5.5.4.6 Singapore
- 5.5.4.7 Malaysia
- 5.5.4.8 Rest of Asia-Pacific
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 Saudi Arabia
- 5.5.5.1.2 United Arab Emirates
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Nigeria
- 5.5.5.2.3 Rest of Africa
- 5.5.5.1 Middle East
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Palo Alto Networks, Inc.
- 6.4.2 CrowdStrike Holdings, Inc.
- 6.4.3 Fortinet, Inc.
- 6.4.4 Check Point Software Technologies Ltd.
- 6.4.5 Zscaler, Inc.
- 6.4.6 Okta, Inc.
- 6.4.7 Splunk Inc.
- 6.4.8 Tenable Holdings, Inc.
- 6.4.9 CyberArk Software Ltd.
- 6.4.10 Rapid7, Inc.
- 6.4.11 Darktrace plc
- 6.4.12 Mandiant LLC (Google Cloud)
- 6.4.13 Trellix Corporation
- 6.4.14 Booz Allen Hamilton Holding Corporation
- 6.4.15 BAE Systems plc
- 6.4.16 Thales S.A.
- 6.4.17 Elastic N.V.
- 6.4.18 Proofpoint, Inc.
- 6.4.19 Ivanti, Inc.
- 6.4.20 Cohesity, Inc.
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment












