 |
市場調查報告書
商品編碼
1851659
應用安全:市場佔有率分析、行業趨勢、統計數據和成長預測(2025-2030 年)Application Security - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
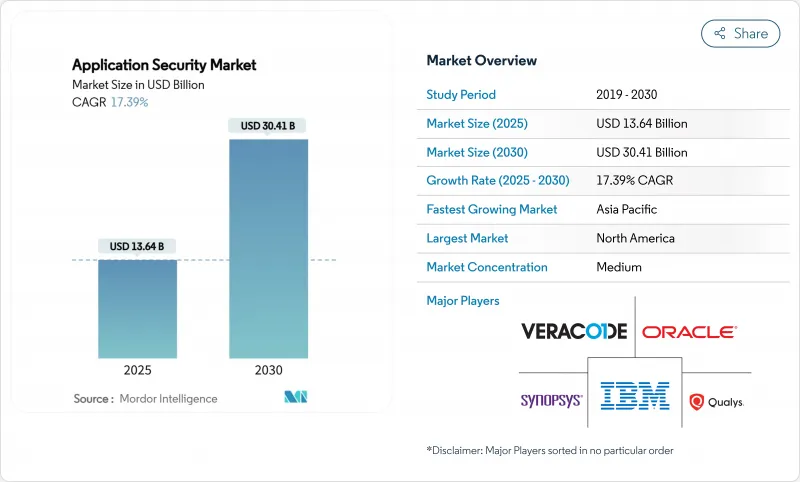
應用安全市場預計將從 2025 年的 136.4 億美元成長到 2030 年的 304.1 億美元,複合年成長率為 17.39%。
朝向雲端運算、以 API 為中心的軟體設計以及不斷擴展的監管法規的轉變,正在加速各大產業的採用。 API 流量的激增、人工智慧產生程式碼的普及以及日益嚴格的事件揭露規則,都推動了這一成長,迫使企業在開發生命週期的早期階段加強測試。雖然大型企業仍然是整體支出的主要驅動力,但中小企業 (SME) 的託管平台正在為供應商開闢新的市場。技術融合正在重塑競爭格局,平台供應商正在整合靜態、動態和運行時保護,以減少工具的臃腫並提高開發人員的效率。
全球應用安全市場趨勢與洞察
基於網路、行動裝置和 API 的攻擊日益增多且手段日益複雜
到2024年,亞太地區的Web應用程式攻擊事件將激增73%,達到510億起。每年開發超過1000個API的零售商面臨著不斷擴大的攻擊面,這些攻擊能夠繞過邊界控制。 2021年至2023年間,供應鏈入侵事件將增加431%,顯示攻擊手段正從直接代碼注入轉向依賴項濫用。企業正在將運行時應用程式自我保護與行為分析相結合,以應對異常流量模式,而不是依賴靜態特徵。在製造業,API事件發生率高達79%,證實了攻擊者的行動速度遠超過大多數操作技術安全計畫。
快速採用DevSecOps工具鏈
隨著團隊將測試更早融入持續整合流程,DevSecOps 的採用率將從 2020 年的 27% 上升到 2024 年的 36%。像 ArmorCode 這樣的平台能夠處理數十億個漏洞發現,並應用機器學習技術來關聯漏洞,從而大規模地確定修復優先順序。儘管取得了這些進展,但仍有 78% 的公司表示存在“左移疲勞”,而冗餘工具會向開發人員發送大量警報,加劇了這種疲勞。最有效的方案能夠簡化整合開發環境中的安全任務,將策略視為版本化的工件,並在提交時自動執行。此外,AI 助理還能在程式碼編輯器中提案修復建議,從而減少在開發和安全入口網站之間切換的時間,進一步增強了這種模型的效果。
總擁有成本高,且工具複雜
到2024年,SaaS價格通膨率將達到11.3%,部分供應商的漲幅甚至高達25%。 42%的中小企業仍然缺乏結構化的事件回應計劃,這表明預算限制了企業級管理能力的提升。重複部署的掃描器、代理商和策略引擎導致整合技能不足,89%的企業預測,儘管員工人數保持不變,但仍需要招募更多員工。 Contrast One™等託管平台現在將專家服務和工具捆綁在一起,從而降低了管理成本。基於使用量的定價模式也正在興起,使中小企業能夠根據實際測試頻率調整支出。
細分市場分析
到2024年,解決方案將佔據78.5%的市場佔有率,這反映出企業對整合套件的偏好。市場領導正在將SAST、DAST、IAST和RASP整合到單一授權中,從而限制工具的分散。統一的儀表板減少了上下文切換,加快了決策速度。服務領域雖然規模較小,但其複合年成長率(CAGR)高達17.9%,超過了更廣泛的應用安全市場,並將繼續受益於技能缺口。
中小企業由於無力負擔專職專家的費用,對託管安全服務的需求正在加速成長。服務提供者透過可預測的訂閱定價和基於結果的服務等級協定 (SLA) 來吸引注重成本的客戶。對於大型企業,專業服務專注於策略映射、管道整合和紅隊模擬,以在運行時檢驗防禦措施。供應商還推出了按使用量分級的服務,讓客戶購買掃描積分而非永久席位,從而提高了漏洞管理預算的透明度。
預計到 2024 年,雲端部署將佔應用安全市場 65.9% 的佔有率,複合年成長率 (CAGR) 為 19.3%。 DORA 及相關法規要求在四小時內報告事件,如果沒有集中式日誌記錄和可擴展的分析功能,很難實現這一目標。雲端原生解決方案能夠快速部署策略更新,並可輕鬆與容器編配系統整合。
對於需要資料駐留的國防和公共部門工作負載而言,本地部署解決方案仍然很受歡迎。我們看到混合模式正在興起,例如金融公司將敏感工作負載部署在私人基礎架構上,並在開發過程中使用雲端掃描器。雲端供應商正在投資硬體支援的身份驗證和機密運算,以解決長期存在的安全主權問題。目前爭論的焦點在於如何確保雲端安全態勢管理能力的一致性,從而能夠識別基礎設施層和應用層中的配置錯誤。
應用程式安全市場按應用程式類型(Web應用安全、其他)、元件(解決方案、服務)、部署模式(雲端、本地部署)、組織規模(中小企業、大型企業)、安全測試類型(靜態應用安全測試 (SAST)、動態應用安全測試 (DAST)、其他)、最終用戶行業(銀行、金融服務和保險 (BFSI)、動態應用安全測試 (DAST)、其他)、最終用戶行業(銀行、金融服務和保險 (BFSI)、區域電子商務、其他地區醫療保健、零售、其他銀行、金融服務和保險 (BFSI)、地區醫療保健、零售、其他地區(銀行、金融服務和保險 (BFSI)、地區醫療保健、零售、其他銀行、金融服務和保險 (BFSI)、地區醫療保健、零售、其他市場預測以美元計價。
區域分析
到2024年,北美將以28.9%的市場佔有率引領應用安全市場,這主要得益於強力的監管壓力以及財富500強企業平均每年超過2000萬美元的安全預算。企業正在整合零信任架構,統一身分、網路和應用程式控制,以支援遠端和混合辦公模式。隨著供應商試行基於人工智慧的漏洞關聯工作負載,以縮短平均修復時間,技術中心也積極推進相關工作。
亞太地區預計將在2030年前實現17.5%的複合年成長率,成為成長最快的地區,這主要得益於數位化政府項目、金融科技的日益普及以及網路應用攻擊激增73%(預計2024年攻擊事件將達到510億次)。新加坡和印度政府已發佈網路安全策略,概述了關鍵基礎設施的最低管理標準。儘管該地區製造業的數位化成熟度較低,但其API安全事件發生率最高,迫使供應商對威脅情報和特定語言的修復資源進行在地化。
歐洲的勢頭得益於《資料保護法》(DORA)、《網路韌性法》和《一般資料保護規範》(GDPR)等一系列全面的立法。自2025年1月起,金融機構必須實施資訊通訊技術風險管理框架,並在四小時內報告資料外洩事件。企業將約9%的IT預算用於資訊安全,但89%的企業預計將增加人手以履行這些義務。資料主權條款鼓勵企業在本地處理敏感工作負載,同時允許對較不重要的資料進行雲端基礎分析,從而推動了混合部署模式的普及。
其他福利:
- Excel格式的市場預測(ME)表
- 3個月的分析師支持
目錄
第1章 引言
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章 市場情勢
- 市場概覽
- 市場促進因素
- 基於網路、行動裝置和 API 的攻擊日益增多,且手段也越來越複雜。
- 快速採用DevSecOps工具鏈
- 加強監管的趨勢(PCI-DSS 4.0、GDPR、DORA 等)
- 第三方/SaaS整合成長
- 根據美國第14028號行政命令,強制揭露SBOM
- 人工智慧產生的程式碼會放大未知漏洞
- 市場限制
- 總擁有成本高,且工具複雜。
- 全球安全編碼人才短缺
- 過多的誤報正在削弱開發者的信任。
- 「左移疲勞」和工具蔓延
- 供應鏈分析
- 監管環境
- 技術展望
- 波特五力模型
- 新進入者的威脅
- 買方的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭對手之間的競爭
- 評估市場的宏觀經濟因素
第5章 市場規模與成長預測
- 按組件
- 解決方案
- 服務
- 透過部署模式
- 雲
- 本地部署
- 按組織規模
- 小型企業
- 主要企業
- 按安全檢查類型
- 靜態應用程式安全掃瞄(SAST)
- 動態應用程式安全測試 (DAST)
- 互動式應用程式安全測試 (IAST)
- 運行時應用程式自我保護 (RASP)
- 軟體配置分析(SCA)
- 按最終用戶行業分類
- BFSI
- 衛生保健
- 零售與電子商務
- 政府/國防
- 資訊科技和電訊
- 教育
- 其他
- 按地區
- 北美洲
- 美國
- 加拿大
- 墨西哥
- 南美洲
- 巴西
- 阿根廷
- 其他南美洲
- 歐洲
- 德國
- 英國
- 法國
- 荷蘭
- 其他歐洲地區
- 亞太地區
- 中國
- 日本
- 印度
- 韓國
- 亞太其他地區
- 中東和非洲
- 中東
- 阿拉伯聯合大公國
- 沙烏地阿拉伯
- 土耳其
- 其他中東地區
- 非洲
- 埃及
- 南非
- 奈及利亞
- 其他非洲地區
- 北美洲
第6章 競爭情勢
- 市場集中度
- 策略趨勢
- 市佔率分析
- 公司簡介
- IBM
- Synopsys Inc.
- Checkmarx
- Veracode(Thoma Bravo)
- Micro Focus
- Oracle Corporation
- Rapid7
- Qualys
- Palo Alto Networks
- Fortinet
- Trend Micro
- GitLab
- GitHub
- Snyk
- CrowdStrike
- Contrast Security
- WhiteHat Security(NTT)
- Positive Technologies
- SiteLock
- Mend(WhiteSource)
- ArmorCode
- Fasoo
- HCL Software(AppScan)
第7章 市場機會與未來展望
The application security market was valued at USD 13.64 billion in 2025 and is expected to reach USD 30.41 billion by 2030, advancing at a 17.39% CAGR.

Cloud migration, API-centric software design and expanding regulatory mandates are accelerating adoption across every major industry vertical. Growth is reinforced by a sharp increase in API traffic, the widespread use of AI-generated code and heightened incident disclosure rules that force organizations to strengthen testing earlier in the development life cycle. Large enterprises continue to anchor overall spending, yet managed platforms aimed at small and medium enterprises (SMEs) are opening a sizeable new addressable base for vendors. Technology convergence is reshaping competitive dynamics, with platform providers integrating static, dynamic and runtime protection to curb tool sprawl and improve developer productivity.
Global Application Security Market Trends and Insights
Rising Volume and Sophistication of Web, Mobile and API-Based Attacks
Web application attacks in the Asia-Pacific region surged 73% to 51 billion events in 2024, underscoring how attackers now exploit APIs at scale. Retailers developing more than 1,000 APIs yearly confront an enlarged attack surface that bypasses perimeter controls. Supply-chain breaches climbed 431% between 2021 and 2023, demonstrating a pivot toward dependency exploitation rather than direct code injection. Enterprises are integrating runtime application self-protection with behavioral analytics to act on anomalous traffic patterns rather than static signatures. Manufacturing recorded a 79% API incident rate, confirming that adversaries move faster than most operational technology security programs.
Rapid Adoption of DevSecOps Toolchains
DevSecOps penetration rose from 27% in 2020 to 36% in 2024 as teams embed testing earlier in continuous integration pipelines. Platforms processing billions of findings, such as ArmorCode, apply machine learning to correlate vulnerabilities and prioritize remediation at scale. Despite progress, 78% of enterprises report "shift-left fatigue," aggravated by redundant tools that overwhelm developers with alerts. The most effective programs streamline security tasks inside integrated development environments, treating policies as version-controlled artifacts automatically enforced at commit. This model is extending through AI assistants that suggest fixes inside code editors, thereby reducing context-switch time between development and security portals.
High Total Cost of Ownership and Tool Complexity
Software-as-a-service inflation reached 11.3% in 2024, with some vendors lifting prices by 25%.Forty-two percent of SMEs still lack a structured incident response plan, revealing budget constraints that limit enterprise-grade controls. Organizations deploy overlapping scanners, agents and policy engines that demand scarce integration skills, leading 89% of firms to foresee additional staffing needs despite flat headcounts. Managed platforms such as Contrast One(TM) now bundle expert services with tooling to cut administrative overhead. Consumption-based pricing models are also emerging, enabling smaller businesses to align spending with actual test frequency.
Other drivers and restraints analyzed in the detailed report include:
- Expanding Regulatory Mandates
- Growth in Third-Party SaaS Integrations
- Global Shortage of Secure-Coding Talent
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Solutions retained a 78.5% share in 2024, reflecting enterprise preference for integrated suites. Market leaders combine SAST, DAST, IAST and RASP under one license to limit tool sprawl. Consolidated dashboards reduce context switching and speed decision-making, fixing a common pain point cited by development teams. The service segment, though smaller, outran the broader application security market with a 17.9% CAGR and will continue to benefit from skills gaps.
Demand for managed security accelerates within SMEs that cannot afford full-time specialists. Providers use predictable subscription pricing and outcome-based service-level agreements to attract cost-conscious buyers. For large enterprises, professional services focus on policy mapping, pipeline integration and red-team simulations that validate runtime defenses. Vendors also introduce consumption-tiered offerings, letting customers buy scanning credits rather than perpetual seats, bringing transparency to budgeting for vulnerability management.
Cloud deployment controlled 65.9% of the application security market in 2024 and is forecast to advance at a 19.3% CAGR. DORA and related regulations specify four-hour incident reporting, a timeline difficult to meet without centralized logging and scalable analytics. Cloud-native solutions enable rapid rollout of policy updates and integrate easily with container orchestration systems.
On-premises solutions remain prevalent in defense and public-sector workloads that require data residency. Hybrid patterns are growing as financial firms keep sensitive workloads on private infrastructure while using cloud scanners during development. Cloud vendors invest in hardware-backed attestation and confidential computing to address lingering sovereignty concerns. Competition now centers on alignment with cloud security posture management functions that map misconfigurations across both infrastructure and application layers.
Application Security Market is Segmented by Application Type (Web Application Security, and More), Component (Solutions, Services), Deployment Mode (Cloud, On-Premises), Organization Size (SMEs, Large Enterprises), Security Testing Type (SAST, DAST, and More), End-User Industry (BFSI, Healthcare, Retail and E-Commerce, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America led the application security market with a 28.9% revenue share in 2024, underpinned by strong regulatory pressure and average Fortune 500 security budgets exceeding USD 20 million annually. Enterprises integrate zero-trust architectures that merge identity, network and application controls to support remote and hybrid work. Advancements originate in technology hubs where vendors pilot AI-driven vulnerability correlation workloads, delivering faster mean time to remediation.
Asia-Pacific records the fastest projected 17.5% CAGR through 2030, fueled by digital government programs, rising fintech adoption and a 73% spike in web application attacks that hit 51 billion events in 2024. Governments in Singapore and India release refreshed cyber strategies that map minimum control baselines for critical infrastructure. The region's manufacturing sector, despite lower digital maturity, faces the highest share of API incidents, pushing vendors to localize threat intelligence and language-specific remediation resources.
Europe's momentum hinges on comprehensive statutes such as DORA, the Cyber Resilience Act and GDPR. Financial entities must implement ICT risk management frameworks and deliver four-hour breach notifications from January 2025. Organizations allocate around 9% of IT budgets to information security, yet 89% still anticipate hiring increases to meet these mandates. Hybrid deployment preferences persist because data-sovereignty clauses encourage on-premise processing of sensitive workloads while permitting cloud-based analytics for less critical data.
- IBM
- Synopsys Inc.
- Checkmarx
- Veracode (Thoma Bravo)
- Micro Focus
- Oracle Corporation
- Rapid7
- Qualys
- Palo Alto Networks
- Fortinet
- Trend Micro
- GitLab
- GitHub
- Snyk
- CrowdStrike
- Contrast Security
- WhiteHat Security (NTT)
- Positive Technologies
- SiteLock
- Mend (WhiteSource)
- ArmorCode
- Fasoo
- HCL Software (AppScan)
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rising volume and sophistication of web-, mobile- and API-based attacks
- 4.2.2 Rapid adoption of DevSecOps toolchains
- 4.2.3 Expanding regulatory mandates (PCI-DSS 4.0, GDPR, DORA, etc.)
- 4.2.4 Growth in third-party/SaaS integrations
- 4.2.5 Mandatory SBOM disclosure post-US Executive Order 14028
- 4.2.6 AI-generated code inflating unknown vulnerabilities
- 4.3 Market Restraints
- 4.3.1 High total cost of ownership and tool complexity
- 4.3.2 Global shortage of secure-coding talent
- 4.3.3 False-positive overload eroding developer trust
- 4.3.4 "Shift-left fatigue" and tool sprawl
- 4.4 Supply-Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Competitive Rivalry
- 4.8 Assesment of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 By Deployment Mode
- 5.2.1 Cloud
- 5.2.2 On-premise
- 5.3 By Organization Size
- 5.3.1 Small and Medium Enterprises
- 5.3.2 Large Enterprises
- 5.4 By Security Testing Type
- 5.4.1 Static Application Security Testing (SAST)
- 5.4.2 Dynamic Application Security Testing (DAST)
- 5.4.3 Interactive Application Security Testing (IAST)
- 5.4.4 Run-time Application Self-Protection (RASP)
- 5.4.5 Software Composition Analysis (SCA)
- 5.5 By End-user Industry
- 5.5.1 BFSI
- 5.5.2 Healthcare
- 5.5.3 Retail and E-commerce
- 5.5.4 Government and Defense
- 5.5.5 IT and Telecom
- 5.5.6 Education
- 5.5.7 Others
- 5.6 By Region
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 South America
- 5.6.2.1 Brazil
- 5.6.2.2 Argentina
- 5.6.2.3 Rest of South America
- 5.6.3 Europe
- 5.6.3.1 Germany
- 5.6.3.2 United Kingdom
- 5.6.3.3 France
- 5.6.3.4 Netherlands
- 5.6.3.5 Rest of Europe
- 5.6.4 Asia_Pacific
- 5.6.4.1 China
- 5.6.4.2 Japan
- 5.6.4.3 India
- 5.6.4.4 South Korea
- 5.6.4.5 Rest of Asia-Pacific
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 United Arab Emirates
- 5.6.5.1.2 Saudi Arabia
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 Egypt
- 5.6.5.2.2 South Africa
- 5.6.5.2.3 Nigeria
- 5.6.5.2.4 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 IBM
- 6.4.2 Synopsys Inc.
- 6.4.3 Checkmarx
- 6.4.4 Veracode (Thoma Bravo)
- 6.4.5 Micro Focus
- 6.4.6 Oracle Corporation
- 6.4.7 Rapid7
- 6.4.8 Qualys
- 6.4.9 Palo Alto Networks
- 6.4.10 Fortinet
- 6.4.11 Trend Micro
- 6.4.12 GitLab
- 6.4.13 GitHub
- 6.4.14 Snyk
- 6.4.15 CrowdStrike
- 6.4.16 Contrast Security
- 6.4.17 WhiteHat Security (NTT)
- 6.4.18 Positive Technologies
- 6.4.19 SiteLock
- 6.4.20 Mend (WhiteSource)
- 6.4.21 ArmorCode
- 6.4.22 Fasoo
- 6.4.23 HCL Software (AppScan)
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment








