 |
市場調查報告書
商品編碼
1849872
雲端加密軟體:市場佔有率分析、產業趨勢、統計數據和成長預測(2025-2030 年)Cloud Encryption Software - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
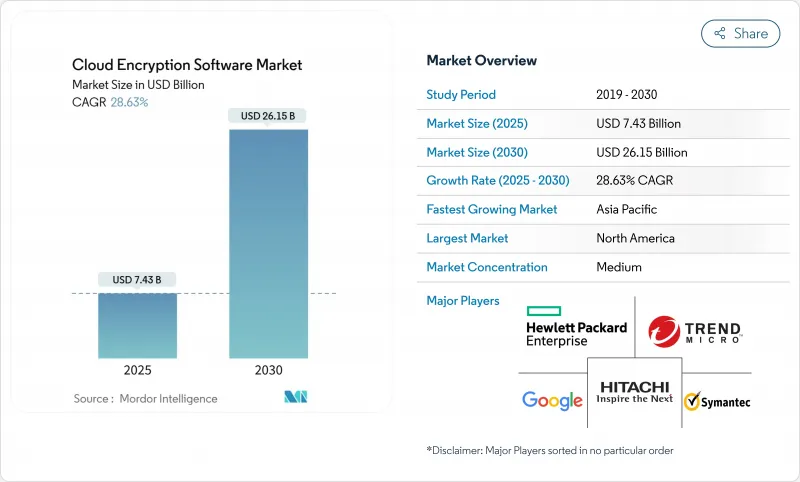
預計到 2025 年雲端加密軟體市場規模將達到 74.3 億美元,到 2030 年將達到 261.5 億美元,複合年成長率為 28.6%。
這種快速成長是由三股強大力量共同推動的:持續不斷的網路攻擊、日益成長的監管壓力以及向多重雲端運算的轉變。美國國家標準與技術研究院 (NIST) 於 2024 年 8 月最終確定了後量子密碼學標準,這加速了企業遷移藍圖的製定,因為董事會認知到「先收穫後解密」的風險已經出現。同時,98% 的金融服務公司在公有雲中運作工作負載,迫切需要跨異質平台的統一金鑰管理。在 FedRAMP 和美國國防部對量子安全演算法的授權的推動下,北美地區在採用方面處於領先地位,而亞太地區則由於主權雲政策而經歷了最快的複合年成長率。效能最佳化的對稱工具、突破性的全同態加密以及用於密封使用中資料的硬體輔助機密運算技術也塑造了密碼學生態系統。
全球雲端加密軟體市場趨勢與洞察
加強資料保護條例
全球法規正在提高安全基準值。 PCI DSS 4.0(2025 年 3 月生效)要求所有擁有者環境每年進行加密審查和多因素身份驗證。歐洲的數位營運彈性法案和 NIS 2 指令要求在 2030 年之前對銀行和關鍵基礎設施進行量子安全加密。在美國,量子計算網路安全準備法案要求聯邦機構過渡到 NIST核准的後量子演算法,為私營部門提供遵循的模板。 FedRAMP 已經要求所有聯邦雲端服務都採用 FIPS 140-2檢驗的模組,使合規性成為事實上的市場准入門票。由於 2002 年的 FERPA 框架沒有預料到學生資料儲存在雲端中,因此大學也在加強控制並要求超過法定最低標準的加密措施。
針對雲端的複雜網路攻擊激增
2024年,雲端工作負載將吸收31%的已記錄網路事件,金融服務領域的勒索軟體成本平均為537萬美元。高級持續性威脅行為者押注未來的量子密碼技術來獲取加密資料集,這推動了即時加密監控以及混合經典和後量子金鑰交換的普及。 44%的公共雲端雲漏洞是由於配置錯誤造成的,這使得能夠加密所有物件且不受管理員技能限制的自動化策略引擎成為必要。攻擊者擴大將目標鎖定在控制平面身份而非端點上,這推動了對以資料為中心的保護的需求,即使在邊界控制失效的情況下,這種保護仍然有效。
效能開銷和延遲
加密資料會增加計算週期和 I/O 延遲。傳統的靜態加密會使大型資料庫的 SQL查詢降低數百毫秒。全同態加密雖然在隱私方面具有突破性進展,但如果不使用硬體加速,則會使處理時間增加 1,000 倍。最近發表在《電腦、材料與連續體》雜誌上的一項基準研究發現,GPU 輔助框架可將此開銷降低約 12%。在邊緣運算場景中,加密延遲會加劇現有的網路延遲,架構師必須在即時回應和機密性之間取得平衡,而這種損失最為明顯。此外,後量子演算法由於金鑰較大,計算量龐大,對低功耗設備的效能預算提出了挑戰。
細分分析
對稱加密方法因其速度快、CPU 開銷低等優勢,將在 2024 年佔據雲端加密軟體市場的 35.6% 佔有率。儘管全同態加密尚處於起步階段,但它是成長最快的技術,預計隨著機密運算用例的擴展,其複合年成長率將達到 29.0%。 FIPS 203、FIPS 204 和 FIPS 205 將於 2024 年 8 月發布,它們為後量子金鑰封裝、數位簽章和基於無狀態雜湊的簽章設定了基準,鼓勵供應商將這些演算法納入其產品藍圖。
企業正在採用混合加密技術(將經典橢圓曲線與後量子格技術結合)來規避演算法故障。格式保留加密技術也正在蓬勃發展,因為它允許舊版應用程式無需重新設計架構即可儲存受保護的資料。隨著 NIST 於 2025 年 3 月將 HQC 選為第五種演算法,並要求提高演算法的多樣性,敏捷加密工具正成為董事會層面的優先事項。因此,對稱工作負載的雲端加密軟體市場規模預計將穩定成長,其中量子安全方案將佔新部署的很大一部分。
靜態資料仍將主導應用堆疊,到2024年將佔據雲端加密軟體市場36.8%的佔有率。然而,隨著可信任執行環境(TEE)消除了長期以來明文處理的障礙,使用中資料加密正以29.7%的複合年成長率飆升。因此,用於敏感工作負載處理的雲端加密軟體市場的成長速度將超過任何其他細分市場。
傳輸層保護對於雲間鏈路仍然至關重要,但性能調優正在轉向後量子握手演算法。 SaaS 協作工具正在廣泛部署用戶端加密,並由組織機構控制加密金鑰。搜尋的對稱加密已在巨量資料環境中出現,在這種環境中,高價值查詢的延遲開銷是可以容忍的。這些轉變正在推動對整個資料生命週期進行無狀態、持久保護的願景。
區域分析
在 FedRAMP 授權、國防部指令以及企業積極向後量子控制遷移的支持下,北美將在 2024 年佔據雲端加密軟體市場的 38.9%。多重雲端採用率很高,供應商正在透過託管金鑰服務和加密敏捷編配來確保收益。大型醫療保健和金融客戶也在大規模測試機密運算框架,加速創新週期。
亞太地區是成長最快的地區,到2030年的複合年成長率將達到29.5%。澳洲、日本、韓國和印度的主權雲端藍圖要求加密金鑰必須保留在國內,這刺激了外部金鑰管理閘道和硬體安全模組的銷售,這些模組可在需要時支援國家演算法。亞洲開發銀行預測,改善的雲端政策預計在2024年至2028年間使該地區的GDP成長高達0.7%,並將加密視為關鍵的推動因素。中國和東南亞的超大規模企業正在與國內晶片製造商合作,提供量子安全網路加密,以跟上西方競爭對手的步伐。
在《一般資料保護規範》(GDPR)和《數位營運韌性法案》的推動下,歐洲持續穩定擴張。金融機構現在必須提交韌性計劃,證明其已向抗量子演算法轉型,這使得歐洲成為跨境金鑰託管互通性的試驗場。隱私保護分析領域對全同態加密的需求日益成長,尤其是在醫療保健和行動領域。南美、中東和非洲等規模較小的市場提供了待開發區機遇,尤其是在5G部署引進需要輕量級、低延遲加密的邊緣雲端架構之際。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3個月的分析師支持
目錄
第1章 引言
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章 市場狀況
- 市場概況
- 市場促進因素
- 加強資料保護條例
- 針對雲端的複雜網路攻擊激增
- 企業多重雲端部署
- 對機密計算的需求
- 量子密碼學的迫切性
- “加密即代碼” DevSecOps 工具
- 市場限制
- 效能開銷和延遲
- 密鑰管理的複雜性
- 可信任執行缺乏互通性
- 邊緣雲端資料主權抑制需求
- 價值鏈分析
- 監管格局
- 技術展望
- 波特五力分析
- 供應商的議價能力
- 買方的議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭對手之間的競爭
- 定價分析
- 投資分析
- 評估宏觀經濟趨勢對市場的影響
第5章市場規模及成長預測
- 按加密類型
- 對稱
- 非對稱/PKI
- 格式儲存
- 完全同態
- 抗量子演算法
- 按用途
- 儲存的資料(儲存、備份)
- 傳輸中的資料(TLS/VPN)
- 使用中的數據/機密計算
- SaaS 檔案和協作加密
- 資料庫/巨量資料加密
- 按組織規模
- 主要企業
- 小型企業
- 按行業
- BFSI
- 醫療保健和生命科學
- 教育
- 零售與電子商務
- 資訊科技和通訊
- 政府和國防
- 其他行業
- 按地區
- 北美洲
- 美國
- 加拿大
- 墨西哥
- 歐洲
- 德國
- 英國
- 法國
- 義大利
- 西班牙
- 其他歐洲地區
- 亞太地區
- 中國
- 日本
- 印度
- 韓國
- 澳洲
- 其他亞太地區
- 南美洲
- 巴西
- 阿根廷
- 南美洲其他地區
- 中東和非洲
- 中東
- 沙烏地阿拉伯
- 阿拉伯聯合大公國
- 土耳其
- 其他中東地區
- 非洲
- 南非
- 埃及
- 奈及利亞
- 其他非洲國家
- 北美洲
第6章 競爭態勢
- 市場集中度
- 策略趨勢
- 市佔率分析
- 公司簡介
- Trend Micro
- CipherCloud/Lookout CASB
- Broadcom(Symantec)
- Hewlett Packard Enterprise
- Google LLC
- Sophos
- Micro Focus(Voltage)
- CyberArk
- Thales(SafeNet)
- Hitachi Vantara
- Boxcryptor
- Microsoft Corporation
- Amazon Web Services
- IBM Corporation
- Check Point Software
- Palo Alto Networks
- Netskope
- Fortanix
- Zscaler
- Akeyless Security
第7章 市場機會與未來展望
The cloud encryption software market size stands at USD 7.43 billion in 2025 and is on course to reach USD 26.15 billion by 2030, registering a 28.6% CAGR.

The surge blends three powerful forces: unrelenting cyber-attacks, mounting regulatory pressure, and the operational shift toward multi-cloud computing. Post-quantum cryptography standards finalized by the National Institute of Standards and Technology (NIST) in August 2024 accelerated enterprise migration road maps as boards realized that harvest-now-decrypt-later risks have already materialized. At the same time, 98% of financial-services firms now operate workloads in public cloud, creating an urgent need for unified key management across heterogeneous platforms. North America leads adoption, propelled by FedRAMP and Department of Defense mandates for quantum-safe algorithms, while sovereign-cloud policies push Asia-Pacific to the fastest regional CAGR. The encryption ecosystem is also shaped by performance-optimized symmetric tools, breakthrough fully homomorphic encryption, and hardware-assisted confidential-computing technologies that seal data during use.
Global Cloud Encryption Software Market Trends and Insights
Tightening Data-Protection Regulations
Worldwide statutes are raising the security baseline. PCI DSS 4.0, effective March 2025, forces annual cryptographic reviews and multi-factor authentication across all card-holder environments. Europe's Digital Operational Resilience Act and NIS 2 directive require quantum-resistant encryption by 2030 for banking and critical infrastructure. In the United States, the Quantum Computing Cybersecurity Preparedness Act compels federal agencies to pivot to NIST-approved post-quantum algorithms, setting a template the private sector is following. FedRAMP has already mandated FIPS 140-2 validated modules for all federal cloud services, turning compliance into a de facto market entry ticket. Even universities are hardening controls because the 2002 FERPA framework never anticipated cloud-stored student data, prompting encryption measures that exceed legal minima.
Surge in Sophisticated Cyber-Attacks on Cloud
Cloud workloads absorbed 31% of recorded cyber incidents in 2024, with ransomware costs in financial services averaging USD 5.37 million. Advanced persistent-threat actors now harvest encrypted troves, betting on future quantum decryption. Real-time encryption monitoring and hybrid classical-plus-post-quantum key exchange are therefore gaining traction. Misconfigurations cause 44% of public-cloud breaches, so automated policy engines that wrap encryption around every object-independent of administrator skill-are becoming mandatory. Attackers increasingly target control-plane identities rather than endpoints, reinforcing the need for data-centric protection that stays effective even when perimeter controls fail.
Performance Overhead and Latency
Encrypting data adds compute cycles and I/O waits. Classical encryption-at-rest slows SQL queries by several hundred milliseconds in high-volume databases. Fully homomorphic encryption, while revolutionary for privacy, can inflate processing time by 1 000X unless hardware acceleration is employed. GPU-assisted frameworks cut that overhead by roughly 12% according to recent benchmark studies published in Computers, Materials and Continua. Edge-computing scenarios feel the penalty most because encryption delay compounds existing network latency, forcing architects to weigh real-time responsiveness against confidentiality. Post-quantum algorithms also raise computational tax because of larger key sizes, challenging performance budgeting in low-power devices.
Other drivers and restraints analyzed in the detailed report include:
- Enterprise Multi-Cloud Adoption
- Confidential-Computing Demand
- Key-Management Complexity
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Symmetric methods dominate the cloud encryption software market with 35.6% share in 2024, favored for their speed and low CPU overhead. Fully homomorphic encryption, despite its infancy, is the fastest-rising technique, forecast to grow at 29.0% CAGR as confidential-computing use cases blossom. The August 2024 release of FIPS 203, FIPS 204, and FIPS 205 set the baseline for post-quantum key encapsulation, digital signatures, and stateless hash-based signatures, prompting vendors to embed these algorithms into product road maps.
Enterprises are deploying hybrid cryptography that blends classical elliptic-curve methods with post-quantum lattices, hedging against algorithmic failure. Format-preserving encryption is also expanding because it lets legacy applications store protected data without schema redesign. With NIST's March 2025 selection of HQC as a fifth algorithm for additional diversity, crypto-agile tooling has become a board-level priority. As a result, the cloud encryption software market size for symmetric workloads is projected to climb steadily, while quantum-safe options capture a larger slice of new deployments.
Data-at-rest still tops the application stack with 36.8% share of the cloud encryption software market in 2024, reflecting mature backup and storage practices. Yet it is data-in-use encryption that makes headlines, surging at a 29.7% CAGR as TEEs remove the longstanding barrier of processing on plaintext. The cloud encryption software market size for confidential-computing workloads will therefore expand faster than any other segment.
Transport-layer protection remains indispensable for inter-cloud links, but performance tuning has shifted toward post-quantum handshake algorithms. SaaS collaboration tools are seeing wider client-side encryption rollouts so organizations retain control over cryptographic keys. Searchable symmetric encryption now appears in big-data environments, where latency overhead can be tolerated for high-value queries. Together these shifts advance the vision of persistent, state-agnostic protection across the entire data life cycle.
The Cloud Encryption Software Market Report is Segmented by Encryption Type (Symmetric, Asymmetric / PKI, and More), Application (Data-At-Rest, Data-In-Transit, and More), Organization Size (Large Enterprises and Small and Medium Enterprises (SMEs)), Industry Vertical (BFSI, Healthcare and Life Sciences, Education, Retail and E-Commerce, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America held 38.9% of the cloud encryption software market in 2024, underpinned by FedRAMP mandates, Department of Defense directives and aggressive enterprise migration to post-quantum controls. Multi-cloud penetration is high, and vendors secure revenue through managed key services and crypto-agile orchestration. Large healthcare and finance clients also test confidential-computing frameworks at scale, accelerating innovation cycles.
Asia-Pacific is the fastest-growing region with a 29.5% CAGR through 2030. Sovereign-cloud blueprints in Australia, Japan, South Korea and India demand that encryption keys remain on domestic soil, spurring sales of external key-management gateways and hardware security modules that support national algorithms where required. The Asian Development Bank estimates improved cloud policy could lift regional GDP by up to 0.7% during 2024-2028, and encryption is cited as a pivotal enabler. Chinese and Southeast Asian hyperscalers are forming in-country alliances with chipmakers to deliver quantum-safe network encryption, keeping pace with Western rivals.
Europe maintains steady expansion driven by GDPR enforcement and the Digital Operational Resilience Act. Financial institutions must file resilience plans outlining migration to quantum-resistant algorithms, a move that is turning Europe into a laboratory for cross-border key-escrow interoperability. Privacy-preserving analytics-especially in health and mobility-stimulate demand for fully homomorphic encryption. Smaller markets in South America and the Middle East and Africa trail but present greenfield opportunities, particularly where 5G rollouts introduce edge-cloud architectures that require lightweight, low-latency encryption.
- Trend Micro
- CipherCloud / Lookout CASB
- Broadcom (Symantec)
- Hewlett Packard Enterprise
- Google LLC
- Sophos
- Micro Focus (Voltage)
- CyberArk
- Thales (SafeNet)
- Hitachi Vantara
- Boxcryptor
- Microsoft Corporation
- Amazon Web Services
- IBM Corporation
- Check Point Software
- Palo Alto Networks
- Netskope
- Fortanix
- Zscaler
- Akeyless Security
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Tightening data-protection regulations
- 4.2.2 Surge in sophisticated cyber-attacks on cloud
- 4.2.3 Enterprise multi-cloud adoption
- 4.2.4 Confidential-computing demand
- 4.2.5 Post-quantum encryption urgency
- 4.2.6 "Encryption-as-code" DevSecOps tools
- 4.3 Market Restraints
- 4.3.1 Performance overhead and latency
- 4.3.2 Key-management complexity
- 4.3.3 Lack of interoperability in trusted-execution
- 4.3.4 Edge-cloud data-sovereignty dampening demand
- 4.4 Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Pricing Analysis
- 4.9 Investment Analysis
- 4.10 Assessment of the Impact of Macroeconomic Trends on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Encryption Type
- 5.1.1 Symmetric
- 5.1.2 Asymmetric / PKI
- 5.1.3 Format-Preserving
- 5.1.4 Fully Homomorphic
- 5.1.5 Quantum-resistant Algorithms
- 5.2 By Application
- 5.2.1 Data-at-Rest (storage, backup)
- 5.2.2 Data-in-Transit (TLS/VPN)
- 5.2.3 Data-in-Use / Confidential Computing
- 5.2.4 SaaS File and Collaboration Encryption
- 5.2.5 Database / Big-data Encryption
- 5.3 By Organization Size
- 5.3.1 Large Enterprises
- 5.3.2 Small and Medium Enterprises (SMEs)
- 5.4 By Industry Vertical
- 5.4.1 BFSI
- 5.4.2 Healthcare and Life Sciences
- 5.4.3 Education
- 5.4.4 Retail and e-Commerce
- 5.4.5 IT and Telecom
- 5.4.6 Government and Defense
- 5.4.7 Other Industry Verticals
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 Europe
- 5.5.2.1 Germany
- 5.5.2.2 United Kingdom
- 5.5.2.3 France
- 5.5.2.4 Italy
- 5.5.2.5 Spain
- 5.5.2.6 Rest of Europe
- 5.5.3 Asia-Pacific
- 5.5.3.1 China
- 5.5.3.2 Japan
- 5.5.3.3 India
- 5.5.3.4 South Korea
- 5.5.3.5 Australia
- 5.5.3.6 Rest of Asia-Pacific
- 5.5.4 South America
- 5.5.4.1 Brazil
- 5.5.4.2 Argentina
- 5.5.4.3 Rest of South America
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 Saudi Arabia
- 5.5.5.1.2 United Arab Emirates
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Egypt
- 5.5.5.2.3 Nigeria
- 5.5.5.2.4 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Trend Micro
- 6.4.2 CipherCloud / Lookout CASB
- 6.4.3 Broadcom (Symantec)
- 6.4.4 Hewlett Packard Enterprise
- 6.4.5 Google LLC
- 6.4.6 Sophos
- 6.4.7 Micro Focus (Voltage)
- 6.4.8 CyberArk
- 6.4.9 Thales (SafeNet)
- 6.4.10 Hitachi Vantara
- 6.4.11 Boxcryptor
- 6.4.12 Microsoft Corporation
- 6.4.13 Amazon Web Services
- 6.4.14 IBM Corporation
- 6.4.15 Check Point Software
- 6.4.16 Palo Alto Networks
- 6.4.17 Netskope
- 6.4.18 Fortanix
- 6.4.19 Zscaler
- 6.4.20 Akeyless Security
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment










