 |
市場調查報告書
商品編碼
1849871
安全和漏洞管理:市場佔有率分析、行業趨勢、統計數據和成長預測(2025-2030 年)Security And Vulnerability Management - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
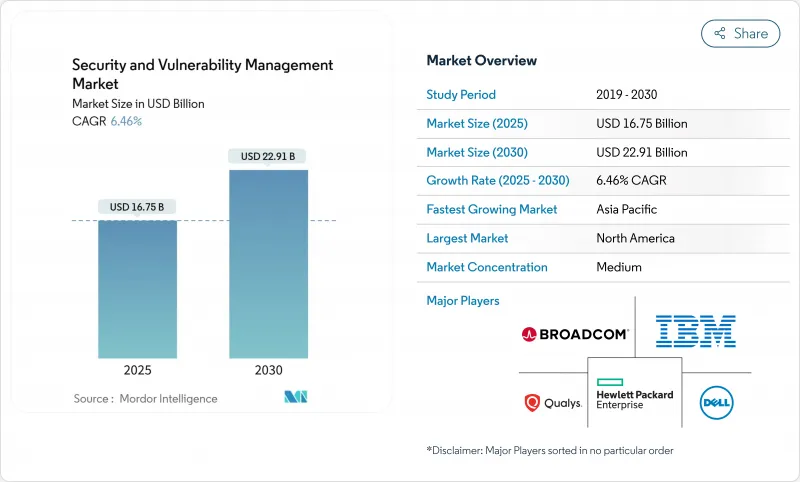
預計2025年安全和漏洞管理市場規模將達到167.5億美元,到2030年將擴大到229.1億美元,在此期間的複合年成長率為6.5%。
安全和漏洞管理市場持續受益於強制性網路風險法規、董事會意識的提升以及向統一風險管理平台(旨在抑制工具氾濫)的策略轉變。儘管面臨宏觀經濟壓力,快速數位化、人工智慧攻擊和零信任的採用仍維持了預算成長,顯示安全和漏洞管理市場是企業韌性的核心支柱。供應商整合仍然是決定性力量,四分之三的公司正在尋求減少供應商數量,而平台公司正在推動從掃描到自動修復的轉變。基於風險的分析如今已超越嚴重性計數,這反映出安全和漏洞管理市場正與保險公司對承保決策持續可見性的需求保持一致。
全球安全和漏洞管理市場趨勢和見解
網路攻擊增多且更加複雜
IBM 記錄到,透過網路釣魚竊取資訊的數量年增了 84%,ChatGPT-4 在提供識別碼的情況下利用了 87% 的單日 CVE。製造業仍然是最受攻擊的行業,因為操作技術的差距容易招致勒索者的攻擊。 2024 年,亞太地區的事件數量增加了 13%,進一步提升了其在安全和漏洞管理市場的優先順序。以身分為中心的入侵目前佔漏洞攻擊的 30%,而竊取的憑證是主要的存取媒介。因此,安全和漏洞管理市場正在將重點轉向優先考慮可用性,而不是一刀切的修補。
雲和 DevOps 的快速採用擴大了攻擊面
微軟進行的一項多重雲端風險調查發現,38% 的組織運行著公開暴露、高權限工作負載,且這些工作負載存在嚴重漏洞。 Palo Alto Networks 發現,80% 的暴露存在於容器化環境中,這凸顯了 DevOps 帶來的複雜性。雖然 68% 的小型企業聲稱已實施 DevSecOps,但只有 12% 的企業會掃描每一次提交,這為安全和漏洞管理市場提供了提供內建掃描功能的機會。無代理程式覆蓋(例如 Google Cloud 的安全指揮中心)消除了部署阻力,並加速了安全性和漏洞管理市場的採用。
中小型企業的整體擁有成本較高
儘管93%的中小企業主管意識到網路風險,但只有36%的人投資新工具。一項歐洲研究顯示,60%遭受網路攻擊的中小企業在六個月內關閉,這給預算帶來了巨大壓力。紐約一家醫院估計,小型機構每年的合規遵循成本為5萬美元,大型網路每年的合規成本為200萬美元。安全性和漏洞管理市場正採用訂閱模式來應對這項挑戰,該模式將掃描、風險評分和儀表板分析功能捆綁到一個雲端許可證中。
細分分析
安全和漏洞管理市場將在2024年實現56億美元的漏洞評估和彙報,佔總收入的33.5%。 RBVM(漏洞管理與漏洞管理)的複合年成長率為7.1%,因為買家瞄準的是3%真正構成風險的缺陷,Tenable收購Vulcan Cyber檢驗了這項策略。容器和雲端工作負載掃描將隨著Kubernetes的採用而成長,應用程式安全測試將整合到涵蓋程式碼、管道和運行時工件的態勢管理平台中。
RBVM 產品現在能夠收集威脅情報來源、資產關鍵性評分並利用可用性來產生按排名排序的待辦事項列表,而非靜態列表。因此,安全和漏洞管理市場正在從檢測轉向決策支援。修補程式和配置模組對於受監管的垂直產業仍然至關重要,而物聯網/營運技術 (IoT/OT) 掃描器則能夠解析專有通訊協定以發現韌體漏洞。這種模組的多樣性預示著支撐企業更新周期的單一管理平台願景。
由於銀行、國防企業和公共產業在實體邊界內保護敏感數據,本地部署將在2024年佔據安全和漏洞管理市場的68.9%。儘管如此,到2030年,雲端採用率仍將以8.1%的複合年成長率飆升。 Google Cloud的無代理程式漏洞掃描功能增強了SaaS交付的吸引力,因為它消除了軟體部署的需要,並加快了概念驗證工作。
混合模式正在主導大型企業的藍圖,將內部網路的低延遲掃描與彈性雲分析結合。安全性和漏洞管理市場正由此演變成由本地收集器、私有雲端節點和超大規模分析組成的網路。策略聯合使客戶能夠充分利用雲端的優勢,同時滿足 NIS2 和 CMMC 的要求,並且任何部署模式都可以滿足所有控制框架的要求。
區域分析
到2024年,北美將佔據安全和漏洞管理市場的37.4%。 CMMC 2.0和第14144號行政命令等聯邦法規正在將持續漏洞管治納入採購規則。加拿大和墨西哥已針對跨境關鍵基礎設施計劃採取了類似的基準,以確保支出的連續性。高昂的違規成本、龐大的技術供應商群體以及活躍的網路保險市場將使其保持領先。
亞太地區未來複合年成長率最高,達7.5%。普華永道預測,2027年亞太地區網路安全支出將達520億美元,用於因應全球31%的網路事件。澳洲的《2024年網路安全法案》強制執行智慧設備基準,並要求披露勒索軟體支付資訊,而紐西蘭的《國家網路安全中心》(NCSC)則負責實施公共部門管控。中國、日本、印度和韓國將推動製造業主導的需求,將安全和漏洞管理市場推向工廠車間和雲端。
在歐洲,NIS2 已在 27 個成員國實施,對能源、交通、金融和醫療保健營運商處以最高 1,000 萬歐元(1,160 萬美元)的罰款。德國、法國、義大利、西班牙和英國已修改其國家法律以符合該指令,並正在建立穩定的計劃儲備。隨著數位服務的成長創造了新的攻擊面,以及各國正在製定受歐盟和美國框架啟發的策略,南美、中東和非洲地區正呈現新的發展動能。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3個月的分析師支持
目錄
第1章 引言
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章 市場狀況
- 市場概況
- 市場促進因素
- 網路攻擊增多且複雜
- 雲和 DevOps 的快速採用擴大了攻擊面
- 監理合規和資料主權義務
- 關鍵基礎設施中物聯網/營運技術資產的激增
- 網路保險承保需要持續的漏洞可見性
- 整個供應鏈中的材料清單(SBOM) 義務
- 市場限制
- 中小型企業的整體擁有成本較高
- 網路安全人才短缺
- 漏洞資料過載導致警報疲勞
- 對供應商整合和平台鎖定的擔憂
- 價值鏈分析
- 監管格局
- 技術展望
- 波特五力分析
- 供應商的議價能力
- 買方的議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭對手之間的競爭
- 評估宏觀經濟趨勢對市場的影響
第5章市場規模及成長預測
- 按類型
- 漏洞評估和報告
- 補丁和配置管理
- 基於風險的漏洞管理(RBVM)
- 容器和雲端工作負載掃描
- 應用程式安全測試
- IoT/OT 漏洞管理
- 依部署方式
- 本地部署
- 雲
- 按組織規模
- 主要企業
- 小型企業
- 按最終用戶
- BFSI
- 醫療保健和生命科學
- 政府和國防
- 資訊科技和通訊
- 製造業和工業
- 零售與電子商務
- 能源和公共產業
- 其他
- 按地區
- 北美洲
- 美國
- 加拿大
- 墨西哥
- 歐洲
- 德國
- 英國
- 法國
- 義大利
- 西班牙
- 其他歐洲地區
- 亞太地區
- 中國
- 日本
- 印度
- 韓國
- 澳洲
- 其他亞太地區
- 南美洲
- 巴西
- 阿根廷
- 南美洲其他地區
- 中東和非洲
- 中東
- 沙烏地阿拉伯
- 阿拉伯聯合大公國
- 土耳其
- 其他中東地區
- 非洲
- 南非
- 埃及
- 奈及利亞
- 其他非洲國家
- 北美洲
第6章 競爭態勢
- 市場集中度
- 策略趨勢
- 市佔率分析
- 公司簡介
- Tenable Holdings Inc.
- Qualys Inc.
- Rapid7 Inc.
- IBM Corporation
- Cisco Systems Inc.
- Microsoft Corporation
- Broadcom Inc.(Symantec)
- Hewlett Packard Enterprise Company
- Dell Technologies Inc.
- Trend Micro Inc.
- Palo Alto Networks Inc.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings Inc.
- Fortinet Inc.
- McAfee Corp.
- Tripwire Inc.(Belden)
- Ivanti
- ServiceNow Inc.
- ATandT Cybersecurity(AlienVault)
- Skybox Security Inc.
- F-Secure Corporation
- Flexera Software LLC(Secunia Research)
- Netskope Inc.
第7章 市場機會與未來展望
The Security and Vulnerability Management market size reached USD 16.75 billion in 2025 and is forecast to climb to USD 22.91 billion by 2030, delivering a 6.5% CAGR over the period.

The Security and Vulnerability Management market continues to benefit from mandatory cyber-risk regulations, heightened board awareness, and a strategic shift toward unified exposure-management platforms that limit tool sprawl. Rapid digitization, AI-enabled attacks, and zero-trust adoption sustain budget growth despite macroeconomic pressure, showing the Security and Vulnerability Management market as a core pillar of enterprise resilience. Vendor consolidation remains a defining force because three-quarters of organizations want fewer suppliers, urging platform players to stretch from scanning to automated remediation. Risk-based analytics now outrank raw severity counts, reflecting how the Security and Vulnerability Management market aligns with insurers that demand continuous visibility for underwriting decisions.
Global Security And Vulnerability Management Market Trends and Insights
Rising Volume and Sophistication of Cyber-Attacks
IBM recorded an 84% year-on-year rise in infostealers delivered through phishing, while ChatGPT-4 exploited 87% of one-day CVEs when presented with identifiers, signalling a critical shift in adversarial capabilities. Manufacturing remains the most targeted industry as operational-technology gaps tempt extortionists. The Asia-Pacific region saw a 13% incident increase in 2024, reinforcing its priority within the Security and Vulnerability Management market. Identity-centric intrusions now make up 30% of breaches, turning credential theft into the main access vector. The Security and Vulnerability Management market therefore pivots toward exploitability-led prioritisation rather than blanket patching.
Rapid Cloud and DevOps Adoption Enlarging Attack Surface
Microsoft's multicloud risk study found that 38% of organisations run publicly exposed, highly privileged workloads with critical vulnerabilities. Palo Alto Networks discovered that 80% of exposures sit in containerised environments, underscoring the complexity DevOps introduces. Although 68% of small firms claim DevSecOps practices, only 12% scan at each commit, creating opportunity for the Security and Vulnerability Management market to deliver embedded scanning. Agentless coverage, exemplified by Google Cloud's Security Command Center, removes deployment friction and accelerates adoption across the Security and Vulnerability Management market.
High Total Cost of Ownership for SMEs
Ninety-three percent of SME executives recognise cyber risk, yet only 36% invest in new tools because two-thirds cite cost hurdles. European studies reveal that 60% of breached SMEs shut within six months, illustrating budget tension. Hospitals in New York estimate yearly compliance bills that range from USD 50,000 for small facilities to USD 2 million for large networks. The Security and Vulnerability Management market answers with subscription models that bundle scanning, risk scoring, and dashboard analytics into a single cloud licence.
Other drivers and restraints analyzed in the detailed report include:
- Regulatory Compliance and Data Sovereignty Mandates
- Proliferation of IoT/OT Assets in Critical Infrastructure
- Shortage of Skilled Cybersecurity Talent
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
The Security and Vulnerability Management market size attributed to Vulnerability Assessment and Reporting stood at USD 5.6 billion in 2024, equivalent to 33.5% of total revenue. RBVM is expanding at 7.1% CAGR because buyers target the 3% of flaws that raise real risk, a strategy validated by Tenable's Vulcan Cyber acquisition. Container and cloud workload scanning rise in tandem with Kubernetes adoption, while Application Security Testing integrates into posture-management platforms that cover code, pipeline, and runtime artefacts.
RBVM products now ingest threat-intelligence feeds, asset criticality scores, and exploit availability, generating ranked backlogs rather than static lists. The Security and Vulnerability Management market therefore migrates from detection to decision support. Patch-and-configuration modules remain crucial for regulated verticals, and IoT/OT scanners parse proprietary protocols to uncover firmware weaknesses. This diversity of modules foreshadows a single-pane-of-glass vision that anchors enterprise renewal cycles.
On-premise deployments controlled 68.9% of the Security and Vulnerability Management market in 2024 as banks, defence primes, and utilities protect sensitive data inside physical boundaries. Nonetheless, cloud deployment is surging at an 8.1% CAGR through 2030. Google Cloud's agentless vulnerability scanning eliminates software rollouts and speeds proof-of-concept efforts, raising the attractiveness of SaaS delivery.
Hybrid models dominate large-enterprise roadmaps because they combine low-latency scanning of internal networks with elastic cloud analytics. The Security and Vulnerability Management market thus evolves into a mesh of on-premise collectors, private-cloud nodes, and hyperscale analytics. Policy federations allow customers to meet NIS2 or CMMC obligations while capitalising on cloud benefits, ensuring that no deployment model alone will satisfy every control framework.
The Security and Vulnerability Management Market Report is Segmented by Type (Vulnerability Assessment and Reporting, Patch and Configuration Management, and More), Deployment Mode (On-Premise and Cloud), Organization Size (Large Enterprises and Small and Medium Enterprises (SMEs)), End-User Vertical (BFSI, Healthcare and Life Sciences, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America dominated the Security and Vulnerability Management market with a 37.4% share in 2024. Federal mandates such as CMMC 2.0 and Executive Order 14144 embed continuous vulnerability governance into procurement rules. Canada and Mexico adopt similar baselines for cross-border critical-infrastructure projects, ensuring spending continuity. High breach costs, a large technology vendor base, and active cyber-insurance markets sustain leadership.
Asia-Pacific registers the highest future CAGR at 7.5%. PwC projects regional cybersecurity outlays of USD 52 billion in 2027 as boards react to a 31% slice of global cyber incidents. Australia's Cyber Security Act 2024 enforces baselines for smart devices and requires ransomware payment disclosure, while New Zealand's NCSC implements public-sector controls. China, Japan, India, and South Korea drive manufacturing-led demand, pushing the Security and Vulnerability Management market into factory floors and cloud stacks alike.
Europe follows a firm path as NIS2 takes effect across 27 member states, subjecting energy, transport, finance, and healthcare operators to penalty levels that reach EUR 10 million (USD 11.60 million). Germany, France, Italy, Spain, and the United Kingdom have adapted domestic legislation to align with the directive, creating steady project pipelines. South America and the Middle East and Africa record emerging momentum because digital services growth exposes fresh attack surfaces, prompting nations to draft strategies that reference EU and U.S. frameworks.
- Tenable Holdings Inc.
- Qualys Inc.
- Rapid7 Inc.
- IBM Corporation
- Cisco Systems Inc.
- Microsoft Corporation
- Broadcom Inc. (Symantec)
- Hewlett Packard Enterprise Company
- Dell Technologies Inc.
- Trend Micro Inc.
- Palo Alto Networks Inc.
- Check Point Software Technologies Ltd.
- CrowdStrike Holdings Inc.
- Fortinet Inc.
- McAfee Corp.
- Tripwire Inc. (Belden)
- Ivanti
- ServiceNow Inc.
- ATandT Cybersecurity (AlienVault)
- Skybox Security Inc.
- F-Secure Corporation
- Flexera Software LLC (Secunia Research)
- Netskope Inc.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Rising volume and sophistication of cyber-attacks
- 4.2.2 Rapid cloud and DevOps adoption enlarging attack surface
- 4.2.3 Regulatory compliance and data sovereignty mandates
- 4.2.4 Proliferation of IoT/OT assets in critical infrastructure
- 4.2.5 Cyber-insurance underwriting now requires continuous vulnerability visibility
- 4.2.6 Software Bill of Materials (SBOM) mandates across supply-chains
- 4.3 Market Restraints
- 4.3.1 High total cost of ownership for SMEs
- 4.3.2 Shortage of skilled cybersecurity talent
- 4.3.3 Alert-fatigue from vulnerability data overload
- 4.3.4 Vendor consolidation and platform lock-in concerns
- 4.4 Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Porter's Five Forces Analysis
- 4.7.1 Bargaining Power of Suppliers
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Threat of New Entrants
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Assessment of the Impact of Macroeconomic Trends on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Type
- 5.1.1 Vulnerability Assessment and Reporting
- 5.1.2 Patch and Configuration Management
- 5.1.3 Risk-Based Vulnerability Management (RBVM)
- 5.1.4 Container and Cloud Workload Scanning
- 5.1.5 Application Security Testing
- 5.1.6 IoT / OT Vulnerability Management
- 5.2 By Deployment Mode
- 5.2.1 On-premise
- 5.2.2 Cloud
- 5.3 By Organization Size
- 5.3.1 Large Enterprises
- 5.3.2 Small and Medium Enterprises (SMEs)
- 5.4 By End-User Vertical
- 5.4.1 BFSI
- 5.4.2 Healthcare and Life Sciences
- 5.4.3 Government and Defense
- 5.4.4 IT and Telecom
- 5.4.5 Manufacturing and Industrial
- 5.4.6 Retail and E-Commerce
- 5.4.7 Energy and Utilities
- 5.4.8 Others
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 Europe
- 5.5.2.1 Germany
- 5.5.2.2 United Kingdom
- 5.5.2.3 France
- 5.5.2.4 Italy
- 5.5.2.5 Spain
- 5.5.2.6 Rest of Europe
- 5.5.3 Asia-Pacific
- 5.5.3.1 China
- 5.5.3.2 Japan
- 5.5.3.3 India
- 5.5.3.4 South Korea
- 5.5.3.5 Australia
- 5.5.3.6 Rest of Asia-Pacific
- 5.5.4 South America
- 5.5.4.1 Brazil
- 5.5.4.2 Argentina
- 5.5.4.3 Rest of South America
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 Saudi Arabia
- 5.5.5.1.2 United Arab Emirates
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Egypt
- 5.5.5.2.3 Nigeria
- 5.5.5.2.4 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 Tenable Holdings Inc.
- 6.4.2 Qualys Inc.
- 6.4.3 Rapid7 Inc.
- 6.4.4 IBM Corporation
- 6.4.5 Cisco Systems Inc.
- 6.4.6 Microsoft Corporation
- 6.4.7 Broadcom Inc. (Symantec)
- 6.4.8 Hewlett Packard Enterprise Company
- 6.4.9 Dell Technologies Inc.
- 6.4.10 Trend Micro Inc.
- 6.4.11 Palo Alto Networks Inc.
- 6.4.12 Check Point Software Technologies Ltd.
- 6.4.13 CrowdStrike Holdings Inc.
- 6.4.14 Fortinet Inc.
- 6.4.15 McAfee Corp.
- 6.4.16 Tripwire Inc. (Belden)
- 6.4.17 Ivanti
- 6.4.18 ServiceNow Inc.
- 6.4.19 ATandT Cybersecurity (AlienVault)
- 6.4.20 Skybox Security Inc.
- 6.4.21 F-Secure Corporation
- 6.4.22 Flexera Software LLC (Secunia Research)
- 6.4.23 Netskope Inc.
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-Need Assessment









