 |
市場調查報告書
商品編碼
1836678
網路取證:市場佔有率分析、產業趨勢、統計數據和成長預測(2025-2030 年)Network Forensics - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
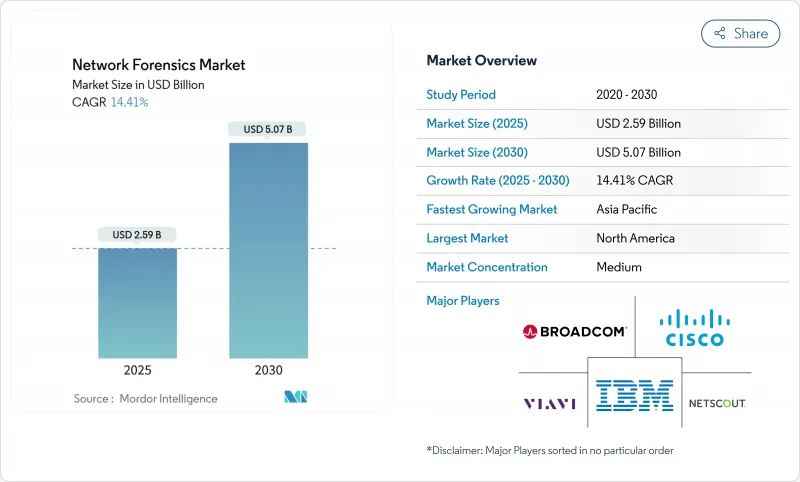
預計到 2025 年網路取證市場規模將達到 25.9 億美元,到 2030 年將達到 50.7 億美元,複合年成長率為 14.41%。
由於資料包級視覺性對於快速漏洞診斷、監管報告和網路保險合規至關重要,因此採用曲線非常陡峭。在混合雲流量、5G 部署和加密的東西向流量暴露出傳統邊界工具無法發現的盲點的領域,支出勢頭尤為強勁。因此,供應商正在將取證功能整合到其網路偵測和回應 (NDR) 平台中,以減少工具的蔓延並縮短平均回應時間。由於保險公司要求提供資料包證據以檢驗索賠,並且美國證券交易委員會 (SEC) 和歐盟《數位營運彈性法案》等監管機構要求及時記錄事件揭露,因此需求也在成長。
全球網路取證市場趨勢與洞察
雲端和混合式 IT 流量可見度的需求快速成長
隨著雲端遷移速度超越傳統監控,73% 的企業已無法從現有工具集中獲取實際的洞察。臨時工作負載之間的東西向流量通常在傳統收集器捕獲之前就消失了,這推動了對雲端原生捕獲引擎的需求,這些引擎可跨多個 IaaS 和 PaaS 域自動收集證據。新產品將資料包擷取、工件保存和時間軸重建整合到單一工作流程中,從而提高了調查效率,並支援在本地、公共雲端和混合環境中實施一致的策略。提供者開始整合智慧儲存分層,實現長期保留而無需線性成本上升,並使監管機構能夠按需審核取證證據。
網路攻擊的頻率和複雜度不斷增加
2024年,全球資料外洩成本將達到488萬美元,憑證竊盜事件將激增84%,這促使人們採用網路分析技術來發現異常身分驗證峰值和橫向行動信標。醫療保健機構仍面臨重重挑戰,93%的機構在三年內遭遇過資料洩露,這促使人們採用持續資料包擷取技術來精確定位攻擊駐留時間和攻擊來源。企業目前正在將豐富的網路遙測技術整合到威脅搜尋例程中,這些例程可以交叉引用端點、身分和雲端日誌,從而提高對抗對手的門檻,並加快法律、監管和保險相關人員的事件後取證工作。
缺乏熟練的資料包級調查員
預計2022年至2032年間,資訊安全分析師的需求將成長32%,但大學和培訓管道卻落後,導致54%的雇主無法填補資料包分析職缺。為此,各組織正在將常規分析任務遷移至AI輔助策略,將一級監控外包給託管服務合作夥伴,並優先考慮工具的易用性,以便非專業人士也能以最小的推出完成資料包時間線。
報告中分析的其他促進因素和限制因素
- 透過 5G 獨立部署擴大東西向流量捕獲
- 需要資料包級證據的網路保險政策
- 超過 40Gbps 的捕獲設備資本支出較高
細分分析
受高速資料包擷取、行為分析和加密流量可視性需求的推動,到2024年,解決方案將貢獻網路取證市場62%的收益。供應商整合機器學習演算法,可在數秒內建立基準流量設定檔並發現偏差。由於企業需要整合、調優和持續的調查支持,而人才短缺,目前規模較小的服務領域正以18%的複合年成長率擴張。供應商正在捆綁評估、事件回應預付費和託管偵測服務,將一次性許可證轉化為經常性收益來源。在預測期內,硬體供應商和全球系統整合商的聯合上市計劃將推動其進一步應用,尤其是在需要全天候證據搜尋的受監管行業。
投資模式表明,自動化解決方案將主導資本預算,而諮詢服務將作為策略覆蓋,以最大化工具價值。支援從部署到事件事後分析的生命週期管理的混合模式,將確保網路取證市場對不同的買家群體保持強大的吸引力。
由於許多金融、政府和國防組織需要現場證據存儲,本地部署將在2024年佔據網路取證市場規模的53%。然而,隨著流量轉向SaaS、IaaS和容器化堆疊,雲端原生部署將以22.5%的複合年成長率激增。雲端收集器可以跨區域編配證據收集,在高容量事件期間自動擴展,並透過將儲存與運算分開來降低前期成本。混合架構將出現,將敏感資料保存在現場,同時利用雲端收集器來處理突發性工作負載和監管較少的領域。
平台供應商目前正在推出可部署在 Kubernetes 叢集中或作為 Sidecar 的輕量級感測器,以確保虛擬網路和實體交換器跨度之間的遙測一致性。合規團隊重視雲端對象儲存所帶來的不可變審核線索,而財務團隊則重視基於營運支出的消費,以便根據季節性流量波動調整支出。這些動態共同推動了更廣泛的網路取證市場持續轉向分散式收集拓撲。
區域分析
受美國證券交易委員會(SEC)揭露規則(要求在四天內報告違規行為)以及將保險範圍與證據品質掛鉤的漸進式網路保險生態系統的推動,北美將在2024年佔據40%的市場佔有率。美國公司正在採用人工智慧分析技術來克服技能短缺,並為潛在的訴訟和監管調查維護全面的日誌。受強制性隱私外洩通知和關鍵基礎設施營運商集中部署的推動,加拿大也處於類似的發展軌跡。
受惠於《一般資料保護規範》(GDPR)的實施以及2025年1月推出的資料處理與分析(DORA)標準,歐洲將在2024年佔據網路取證市場28%的收益。英國、德國和法國的銀行中心已將其資料包捕獲預算翻倍,以實現24小時事件通知。專注於5G走廊的公共部門計劃正在投入8.65億歐元(9.31億美元)用於網路建設,推動新安全監控層的建置。歐盟的跨國資料共用架構也刺激了符合跨司法管轄區證據可採性標準的標準化取證工作流程的需求。
亞太地區是成長最快的地區,2025年至2030年的複合年成長率為17.9%。中國的數位金融擴張、印度的5G競標以及澳洲的關鍵基礎設施改革正在創造持續的機會。預計到2025年,光是韓國的數位鑑識產業規模就將達到35.2億美元,這反映了公共和私營部門對該國網路韌性的大力投資。儘管技能短缺仍然嚴重,但託管安全服務正在抵消地區差異,並加速中型企業採用該技術。該地區對民族國家主導的宣傳活動的接觸進一步提升了能夠重建高級多階段入侵的網路取證市場工具的重要性。
其他福利:
- Excel 格式的市場預測 (ME) 表
- 3個月的分析師支持
目錄
第1章 引言
- 調查結果
- 調查範圍
- 調查前提
第2章調查方法
第3章執行摘要
第4章 市場狀況
- 市場概況
- 市場促進因素
- 雲端和混合式 IT 流量可見度的需求快速成長
- 網路攻擊的頻率和複雜程度迅速增加
- 嚴格的違規通報義務(GDPR、SEC、DORA)
- 結合 NDR 和取證技術可減少工具蔓延
- 透過 5G 獨立部署擴展東西向流量捕獲
- 需要資料包級證據的網路保險政策
- 市場限制
- 缺乏熟練的資料包級調查員
- 40 Gbps 以上捕獲設備的資本支出較高
- 多重雲端內嵌監控的效能開銷
- 跨境資料包儲存的資料主權限制
- 價值/供應鏈分析
- 監管狀況
- 技術展望(基於AI的資料包分析、TLS1.3解密)
- 五力分析
- 新進入者的威脅
- 買方的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭對手之間的競爭
- 投資與資金籌措分析
第5章市場規模及成長預測(金額)
- 按組件
- 解決方案
- 按服務
- 依實施類型
- 本地部署
- 雲端基礎
- 按組織規模
- 中小企業
- 主要企業
- 按用途
- 端點安全
- 資料中心安全
- 網路安全
- 應用程式安全
- 按最終用戶產業
- 資訊科技/通訊
- BFSI
- 零售與電子商務
- 政府和國防
- 醫療保健和生命科學
- 製造業
- 其他(能源、教育)
- 按地區
- 北美洲
- 美國
- 加拿大
- 墨西哥
- 南美洲
- 巴西
- 其他南美
- 歐洲
- 英國
- 德國
- 法國
- 其他歐洲國家
- APAC
- 中國
- 印度
- 日本
- 澳洲
- 亞太地區其他國家
- 中東和非洲
- 中東
- 沙烏地阿拉伯
- 阿拉伯聯合大公國
- 土耳其
- 其他中東地區
- 非洲
- 南非
- 其他非洲國家
- 北美洲
第6章 競爭態勢
- 市場集中度
- 策略趨勢
- 市佔率分析
- 公司簡介
- Broadcom(Symantec)
- Cisco Systems
- IBM Corporation
- Netscout Systems
- Trellix(FireEye)
- RSA Security
- AccessData(OpenText)
- LogRhythm
- LiveAction
- NIKSUN
- Rapid7
- Palo Alto Networks
- Darktrace PLC
- ExtraHop Networks
- Vectra AI
- CrowdStrike Holdings
- Fortinet Inc.
- Check Point Software Tech.
- Sophos Group
- Gigamon
第7章 市場機會與未來展望
The network forensics market size is valued at USD 2.59 billion in 2025 and is forecast to reach USD 5.07 billion by 2030, advancing at a 14.41% CAGR.

The adoption curve is steep because packet-level visibility has become indispensable for rapid breach diagnosis, regulatory reporting and cyber-insurance compliance. Spending momentum is especially strong where hybrid-cloud traffic, 5G roll-outs and encrypted east-west flows expose blind spots that traditional perimeter tools overlook. Vendors are therefore embedding forensic functionality into Network Detection and Response (NDR) platforms, shrinking tool sprawl and lowering mean-time-to-respond. Demand is also lifted by insurers that now require packet evidence for claims validation and by regulators such as the SEC and the EU's Digital Operational Resilience Act, which mandate timely, well-documented incident disclosure.
Global Network Forensics Market Trends and Insights
Proliferation of Cloud & Hybrid IT Traffic Visibility Needs
Cloud migration has outpaced traditional monitoring, leaving 73% of enterprises unable to derive actionable insight from existing toolsets. East-west traffic among ephemeral workloads often vanishes before legacy collectors capture it, prompting demand for cloud-native capture engines that automate evidence gathering across multiple IaaS and PaaS domains. Emerging offerings integrate packet capture, artifact preservation and timeline reconstruction in a single workflow, improving investigative efficiency and supporting consistent policy enforcement across on-premises, public cloud and hybrid environments. Providers have begun to embed smart storage tiering, enabling long-term retention without linear cost escalation and ensuring regulators can audit forensic evidence on demand.
Escalating Frequency & Sophistication of Cyber-Attacks
Global breach costs climbed to USD 4.88 million in 2024, while credential-theft incidents surged 84%, fueling adoption of network analytics that surface anomalous authentication spikes and lateral-movement beacons. Healthcare institutions remain under siege as 93% encountered a breach within three years, pushing them to deploy continuous packet capture that pinpoints dwell time and attack provenance. Enterprises now integrate enriched network telemetry into threat-hunting routines that cross-reference endpoint, identity and cloud logs, raising the bar for adversaries and accelerating post-incident forensics for legal, regulatory and insurance stakeholders.
Shortage of Skilled Packet-Level Investigators
Demand for information-security analysts is projected to expand 32% between 2022-2032, yet universities and training pipelines lag, leaving 54% of employers unable to fill packet-analysis roles.The deficit inflates salary baselines beyond USD 119,000 and amplifies operational risk when alerts outstrip triage capacity. Organizations respond by shifting routine parsing to AI-assisted playbooks, outsourcing level-1 monitoring to managed service partners and prioritizing tool usability so non-specialists can navigate packet timelines with minimal ramp-up.
Other drivers and restraints analyzed in the detailed report include:
- 5G Standalone Roll-outs Expanding East-West Traffic Capture
- Cyber-Insurance Policies Mandating Packet-Level Evidence
- High CAPEX of >40 Gbps Capture Appliances
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Solutions generated 62% of network forensics market revenue in 2024, a position powered by demand for high-speed packet capture, behavioural analytics and encrypted-traffic visibility. Feature velocity is brisk, with vendors embedding machine-learning algorithms that establish baseline traffic profiles and surface deviations in seconds. The services segment is smaller today yet expands at an 18% CAGR because organizations need integration, tuning and continuous investigation support while talent remains scarce. Providers bundle assessment, incident-response retainers and managed detection to convert one-time licences into recurring revenue streams. Over the forecast horizon, joint go-to-market programs between hardware vendors and global system integrators will further amplify adoption, especially in regulated industries that require 24-hour evidence retrieval.
Investment patterns suggest that automation-ready solutions will dominate capital budgets, while advisory services grow as strategic overlays that maximize tooling value. The blended model supports life-cycle management from deployment to incident post-mortems, ensuring the network forensics market retains strong pull across diverse buyer personas.
On-premise deployments maintained 53% share of network forensics market size in 2024 because many financial, government and defense entities require local custody of evidence. Nevertheless, cloud-native deployments soar at a 22.5% CAGR as traffic migrates to SaaS, IaaS and containerised stacks. Cloud collectors orchestrate evidence gathering across regions, auto-scale during volumetric events and decouple storage from compute, slashing upfront expense. Hybrid architectures emerge where sensitive data stays on site, yet burst workloads and less regulated segments leverage cloud collectors.
Platform providers now ship lightweight sensors deployable in Kubernetes clusters or as side-cars, ensuring parity of telemetry between virtual networks and physical switch spans. Compliance teams value the immutable audit trails that cloud object stores enable, while finance teams appreciate opex-based consumption that aligns spend with seasonal traffic variance. Together these dynamics reinforce an enduring pivot toward distributed collection topologies within the broader network forensics market.
Network Forensic Market is Segmented by Component (Solution and Services), by Deployment Model (On-Premise, Cloud), by Organization Size (Small and Medium Enterprises (SMEs) and Large Enterprises), by Application (Endpoint Security, Data Center Security, Network Security, and More), by End-User Industry (IT and Telecom, BFSI, and More), and by Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America held 40% share in 2024, driven by SEC disclosure rules that enforce four-day breach reporting and by an advanced cyber-insurance ecosystem that ties coverage to evidence quality. U.S. enterprises deploy AI-enabled analysis to overcome skills shortages and maintain comprehensive logs for potential litigation or regulatory inquiry. Canada follows a comparable trajectory, underpinned by mandatory privacy breach notifications and concentrated presence of critical infrastructure operators.
Europe captured 28% of network forensics market revenue in 2024, benefiting from GDPR enforcement and the January 2025 start of DORA. Banking hubs in the United Kingdom, Germany and France doubled packet-capture budgets to achieve 24-hour incident notification. Public-sector projects focused on 5G corridors channel EUR 865 million (USD 931 million) into network build-outs, prompting new security monitoring layers. Cross-border data-sharing frameworks inside the EU also stimulate demand for standardized forensic workflows that meet multi-jurisdictional evidence admissibility criteria.
Asia-Pacific is the fastest-growing theatre with a 17.9% 2025-2030 CAGR. China's digital-finance expansion, India's 5G auctions and Australia's critical-infrastructure reforms create sustained opportunities. South Korea's digital forensics sector alone is projected at USD 3.52 billion by 2025, reflecting public-private investment in national cyber-resilience. While skills shortages remain acute, managed security services offset local gaps and accelerate uptake among medium-sized enterprises. The region's exposure to state-sponsored campaigns further elevates the relevance of network forensics market tools that can reconstruct sophisticated, multi-stage intrusions.
- Broadcom (Symantec)
- Cisco Systems
- IBM Corporation
- Netscout Systems
- Trellix (FireEye)
- RSA Security
- AccessData (OpenText)
- LogRhythm
- LiveAction
- NIKSUN
- Rapid7
- Palo Alto Networks
- Darktrace PLC
- ExtraHop Networks
- Vectra AI
- CrowdStrike Holdings
- Fortinet Inc.
- Check Point Software Tech.
- Sophos Group
- Gigamon
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Deliverables
- 1.2 Scope of the Study
- 1.3 Study Assumptions
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Proliferation of cloud and hybrid IT traffic visibility needs
- 4.2.2 Escalating frequency and sophistication of cyber-attacks
- 4.2.3 Stringent breach-reporting mandates (GDPR, SEC, DORA)
- 4.2.4 Convergence of NDR and forensics reducing tool sprawl
- 4.2.5 5G standalone roll-outs expanding east-west traffic capture
- 4.2.6 Cyber-insurance policies mandating packet-level evidence
- 4.3 Market Restraints
- 4.3.1 Shortage of skilled packet-level investigators
- 4.3.2 High CAPEX of >40 Gbps capture appliances
- 4.3.3 Performance overhead in multi-cloud inline monitoring
- 4.3.4 Data-sovereignty limits on cross-border packet storage
- 4.4 Value / Supply-Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook (AI-driven packet analytics, TLS1.3 decryption)
- 4.7 Porter's Five Forces
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Investment and Funding Analysis
5 MARKET SIZE AND GROWTH FORECASTS (VALUE)
- 5.1 By Component
- 5.1.1 Solutions
- 5.1.2 Services
- 5.2 By Deployment Mode
- 5.2.1 On-premise
- 5.2.2 Cloud-based
- 5.3 By Organization Size
- 5.3.1 Small and Medium Enterprises (SMEs)
- 5.3.2 Large Enterprises
- 5.4 By Application
- 5.4.1 Endpoint Security
- 5.4.2 Data-Center Security
- 5.4.3 Network Security
- 5.4.4 Application Security
- 5.5 By End-user Industry
- 5.5.1 IT and Telecom
- 5.5.2 BFSI
- 5.5.3 Retail and E-commerce
- 5.5.4 Government and Defense
- 5.5.5 Healthcare and Life Sciences
- 5.5.6 Manufacturing
- 5.5.7 Others (Energy, Education)
- 5.6 By Geography
- 5.6.1 North America
- 5.6.1.1 United States
- 5.6.1.2 Canada
- 5.6.1.3 Mexico
- 5.6.2 South America
- 5.6.2.1 Brazil
- 5.6.2.2 Rest of South America
- 5.6.3 Europe
- 5.6.3.1 United Kingdom
- 5.6.3.2 Germany
- 5.6.3.3 France
- 5.6.3.4 Rest of Europe
- 5.6.4 APAC
- 5.6.4.1 China
- 5.6.4.2 India
- 5.6.4.3 Japan
- 5.6.4.4 Australia
- 5.6.4.5 Rest of APAC
- 5.6.5 Middle East and Africa
- 5.6.5.1 Middle East
- 5.6.5.1.1 Saudi Arabia
- 5.6.5.1.2 United Arab Emirates
- 5.6.5.1.3 Turkey
- 5.6.5.1.4 Rest of Middle East
- 5.6.5.2 Africa
- 5.6.5.2.1 South Africa
- 5.6.5.2.2 Rest of Africa
- 5.6.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles
- 6.4.1 Broadcom (Symantec)
- 6.4.2 Cisco Systems
- 6.4.3 IBM Corporation
- 6.4.4 Netscout Systems
- 6.4.5 Trellix (FireEye)
- 6.4.6 RSA Security
- 6.4.7 AccessData (OpenText)
- 6.4.8 LogRhythm
- 6.4.9 LiveAction
- 6.4.10 NIKSUN
- 6.4.11 Rapid7
- 6.4.12 Palo Alto Networks
- 6.4.13 Darktrace PLC
- 6.4.14 ExtraHop Networks
- 6.4.15 Vectra AI
- 6.4.16 CrowdStrike Holdings
- 6.4.17 Fortinet Inc.
- 6.4.18 Check Point Software Tech.
- 6.4.19 Sophos Group
- 6.4.20 Gigamon
7 MARKET OPPORTUNITIES AND FUTURE OUTLOOK
- 7.1 White-space and Unmet-need Assessment











