 |
市場調查報告書
商品編碼
1836651
銀行雲端安全:市場佔有率分析、產業趨勢、統計數據和成長預測(2025-2030 年)Cloud Security In Banking - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
預計到 2025 年銀行雲端安全市場規模將達到 361.7 億美元,到 2030 年將達到 806.6 億美元。
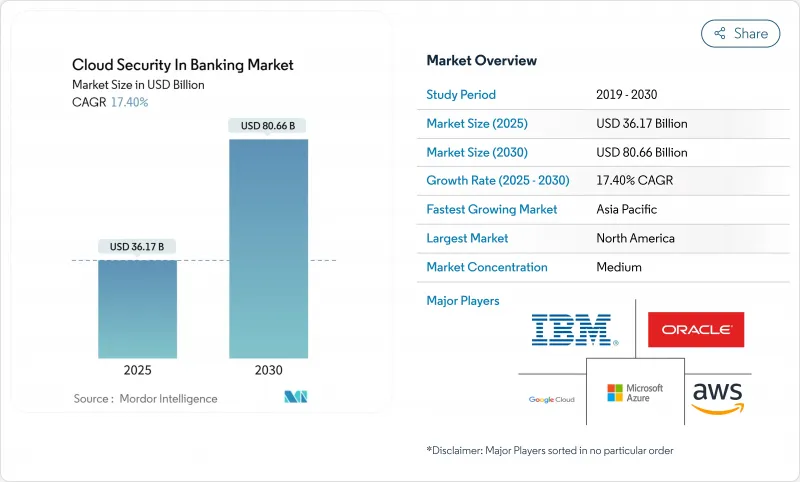
這項擴張反映了銀行轉向雲端原生架構以降低營運成本、提高敏捷性並滿足監管機構對成熟營運彈性的要求。到 2024 年,針對金融機構工作負載的勒索軟體事件將成長到 78%,因此對雲端原生架構的需求也在成長,這促使資訊安全領導者加快採用零信任並加強第三方風險監控。安全供應商之間的整合使銀行能夠存取結合了 API 保護、身分管治和人工智慧驅動的詐欺分析的廣泛平台。同時,公有雲供應商正在整合預先建置的合規工具,以簡化根據歐盟數位營運彈性法案 (DORA) 等措施進行的審核,該法案於 2025 年 1 月生效。到 2024 年,北美將保持 37.2% 的市場佔有率,而亞太公共雲端將出現最快的成長,到 2030 年,區域複合年成長率將達到 17.8%,這主要得益於各國數據本地化法規和行動優先的消費者銀行業務趨勢。
全球銀行雲端安全市場趨勢與洞察
針對銀行的網路攻擊增加且更加複雜
2024年,金融機構將面臨78%的勒索軟體受害率。攻擊者目前正在利用API濫用、容器配置錯誤和第三方軟體漏洞,其中包括一次雲端配置錯誤,該漏洞使約50萬摩根大通客戶面臨風險。由於每次違規的平均成本高達1000萬美元,迫切需要過渡到行為分析主導的零信任管理,以檢驗每個會話和資產。大型銀行正在將持續的合規性掃描和威脅搜尋納入其DevSecOps管道,將暴露窗口從幾天縮短到幾小時。全球支付管道SWIFT正在與Google雲端試行一種聯邦學習模型,該模型可以在不移動敏感資料的情況下標記異常交易,展示了人工智慧如何在保護隱私的同時檢測詐欺行為。隨著組織犯罪者透過在暗網市場上取得被盜銀行憑證收益,主動雲端隔離和最低權限IAM已成為董事會層面的優先事項。
即時合規自動化要求(巴塞爾協議 III、DORA 等)
歐盟的數據和行動韌性計劃 (DORA) 要求 22,000 家金融機構在 24 小時內報告嚴重網路事件,並測試關鍵雲供應商的退出計劃,敦促銀行實施自動證據收集引擎,向監管機構提供近乎即時的資訊。美國監管機構也朝著同一方向發展。美國財政部的《2025 年雲端韌性報告》敦促對系統性金融機構進行持續控制監控。雲端供應商現在將巴塞爾協定 III、PCI DSS 和 GDPR 映射範本捆綁到儀表板中,從而將人工審核工作減少了 40%。對於全球營運的銀行來說,在統一的合規結構上進行標準化使它們能夠使用一套政策來滿足重疊的司法管轄區的要求,這在客戶資料跨越歐盟、美國和亞洲流動時尤其有價值。早期採用者報告產品推出更快,因為嵌入式管治消除了冗長的安全審查週期,將合規性從收益抑制因素轉變為推動因素。
與多租戶公有雲的資料居住競爭
GDPR、中國的《網路安全法》和印度的《資料保護條例》(DPDP) 都要求銀行資料在地化,這與全球多租戶架構相反。超大規模雲端服務供應商提供的主權雲端承諾元資料隔離和本地金鑰存儲,但未能達到某些監管機構要求的精細化部署控制。在規模較小的亞太地區市場,通常適用「一國資料中心」規則,這削弱了規模經濟,並迫使銀行轉向混合拓撲結構,將敏感資料集置於本地或本地私有區域中。由此產生的架構複雜性推高了成本,增加了配置錯誤的風險,並延緩了雲端採用計畫。政策制定者正在與業界討論,以完善居住規定,確保網路彈性優勢大於司法管轄權方面的擔憂,但2020年之前不太可能達成解決方案。
報告中分析的其他促進因素和限制因素
- 透過無伺服器和容器原生安全控制避免成本
- 擴展開放銀行 API 推動零信任採用
- 銀行SOC團隊缺乏雲端安全技能
細分分析
這反映了銀行從邊界控制轉向以身分為中心的防護措施,能夠在幾毫秒內對使用者、服務和 API 進行身分驗證。隨著分散式營運模式的持續發展,IAM 整合了單一登入、特權存取管理和設備狀態檢查,構成了零信任計畫的支柱。供應商現在正在整合持續的風險評分和無密碼流程,以減少登入阻力。
雲端加密是成長最快的領域,到2030年,複合年成長率將達到18.2%。量子威脅意識和日益嚴格的資料保護法規正在推動銀行採用硬體安全模組和集中式金鑰編配。隨著量子安全演算法在支付管道上的試點,以加密為重點的雲端安全產品市場規模預計將持續成長,這使得加密技術既成為合規的必要條件,也成為競爭優勢。多方運算和格式保留加密的興起,使金融機構能夠在無需解密的情況下分析數據,從而推動跨境詐欺分析和人工智慧模型訓練方面的突破。
到2024年,公共雲端部署將佔銀行雲端安全市場規模的62.4%,進一步印證了人們對超大規模防禦、專用金融服務區域和共享責任藍圖的信心。 AWS和微軟等供應商報告稱,銀行工作負載實現了兩位數成長,這得益於PCI DSS按需審核包等縮短評估時間的工具。然而,主權雲和區域雲的變體表明,單一模式並不適合所有司法管轄區,而英國監管機構要求的退出策略測試凸顯了仍然存在的集中風險。
混合雲的採用率正以 20.1% 的複合年成長率成長,因為銀行可以利用公共架構來擴展分析能力,同時滿足資料駐留要求。容器和服務網格提供了工作負載的可移植性,並支援壓力退出演練,可在數小時內將流量從高風險提供者轉移出去。隨著監管機構對單一供應商依賴關係的審查,多重雲端工具鏈正成為衡量營運韌性的更廣泛指標,從而加速了用於跨提供者保護和編配的抽象層的採購。
區域分析
2024年,北美以37.2%的佔有率佔據銀行雲端安全市場的主導地位。多年的監管和供應商對話、成熟的公私威脅共用以及摩根大通每年170億美元的技術支出,凸顯了當地市場需求的深度。美國財政部發布的《2025年雲端彈性研究》正式鼓勵關鍵機構在部署即時監控管道的同時採用多重雲端,從而加速跨提供者整合安全堆疊的訂購。加拿大監管機構目前在其開放銀行指南中明確提及零信任和安全API規範,預示著進一步的投資動能。
隨著監管機構在數據在地化和創新之間取得平衡,到2030年,亞太地區的複合年成長率將達到17.8%,位居榜首。日本的一個地區性銀行聯盟採用了運作IBM和Kyndryl基礎設施的共用混合平台,展示了一種協作式的、經濟高效且合規的安全方案。新加坡在全國推廣的數位身分認證和馬來西亞的RMiT標準也分別推動了身分存取管理(IAM)和即時監控的採用。中國的等級保護制度(MLPS 2.0)要求加密、持續監控和在岸金鑰存儲,這促使提供者推出具有硬體身份驗證的本地區域。
在歐洲,DORA 和 PSD2/PSD3 正在加速發展。義大利銀行 Credem Banca 已遷移至以安全為中心的雲端平台,該平台整合了加密和即時事件通知功能,將監管報告速度提高了 20%。泰雷茲 2024 年的一項調查發現,65% 的歐洲公司將雲端安全列為其第二大網路安全優先事項,凸顯了董事會層面對雲端安全的重視。多重雲端彈性演練和主權雲端試點現已成為合約要求,這刺激了對編配層的需求,該編排層可在亞馬遜、微軟和谷歌環境中強制執行策略,而無需手動複製規則。
其他福利
- Excel 格式的市場預測 (ME) 表
- 3個月的分析師支持
目錄
第1章 引言
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章 市場狀況
- 市場概況
- 市場促進因素
- 針對銀行工作負載的網路攻擊日益增加且愈發複雜
- 即時合規自動化要求(巴塞爾協議 III、DORA 等)
- 透過無伺服器和容器原生安全管理避免成本
- 擴展開放銀行 API 推動零信任採用
- 人工智慧詐欺偵測與雲端安全套件捆綁在一起
- 市場限制
- 與多租戶公有雲的資料居住競爭
- 銀行 SOC 團隊缺乏精通雲端安全的人才
- 第三方金融科技整合中隱藏的依賴風險
- 產業價值鏈分析
- 監管狀況
- 技術展望
- 產業吸引力-波特五力分析
- 新進入者的威脅
- 買方的議價能力
- 供應商的議價能力
- 替代品的威脅
- 競爭對手之間的競爭
- 宏觀經濟因素如何影響市場
第5章市場規模及成長預測(金額)
- 依軟體類型
- 雲端身分和存取管理 (IAM)
- 雲端電子郵件安全
- 雲入侵偵測與預防(IDPS)
- 雲端加密
- 雲端網路安全
- 按部署模型
- 公共雲端
- 私有雲端
- 混合雲端
- 保全服務
- 資料安全
- 應用程式安全
- 網路安全
- 安全監控與編配(SIEM/SOAR)
- 身份、身份驗證和詐欺分析
- 按銀行類型
- 零售/消費者銀行業務
- 企業及投資銀行業務
- 卡和支付服務供應商
- 純數位銀行/新銀行
- 按地區
- 北美洲
- 美國
- 加拿大
- 墨西哥
- 南美洲
- 巴西
- 阿根廷
- 智利
- 其他南美
- 歐洲
- 德國
- 英國
- 法國
- 義大利
- 西班牙
- 俄羅斯
- 其他歐洲國家
- 亞太地區
- 中國
- 印度
- 日本
- 韓國
- 馬來西亞
- 新加坡
- 澳洲
- 其他亞太地區
- 中東和非洲
- 中東
- 阿拉伯聯合大公國
- 沙烏地阿拉伯
- 土耳其
- 其他中東地區
- 非洲
- 南非
- 奈及利亞
- 埃及
- 其他非洲國家
- 北美洲
第6章 競爭態勢
- 市場集中度
- 策略趨勢
- 市佔率分析
- 公司簡介
- AWS(Amazon.com, Inc.)
- Google Cloud Platform(Alphabet Inc.)
- Microsoft Azure(Microsoft Corporation)
- IBM Cloud Security(IBM Corporation)
- Oracle Cloud(Oracle Corporation)
- Salesforce, Inc.
- Palo Alto Networks, Inc.
- Fortinet Inc.
- Check Point Software Technologies Ltd.
- Trend Micro Inc.
- CrowdStrike Holdings, Inc.
- Zscaler, Inc.
- Proofpoint Inc.
- Okta, Inc.
- Ping Identity Corporation
- SailPoint Technologies Holdings Inc.
- Netskope, Inc.
- Imperva, Inc.
- Qualys, Inc.
- Rapid7, Inc.
- Sophos Ltd.
- Illumio Inc.
- Akamai Technologies Inc.
- Thales Group(Vormetric)
- Temenos AG
- nCino, Inc.
第7章 市場機會與未來趨勢
The cloud security in banking market stood at USD 36.17 billion in 2025 and is forecast to reach USD 80.66 billion by 2030, reflecting a 17.4% CAGR.

This expansion mirrors banks' pivot toward cloud-native architectures that cut operating costs, improve agility, and satisfy regulators demanding proven operational resilience. Demand is also rising because ransomware incidents targeting financial workloads climbed to 78% in 2024, pushing chief information security officers to accelerate zero-trust adoption and deeper third-party risk oversight. Consolidation among security vendors is giving banks access to broad platforms that combine API protection, identity governance, and AI-powered fraud analytics. In parallel, public cloud providers are embedding pre-configured compliance tooling that simplifies audits under measures such as the EU's Digital Operational Resilience Act (DORA), which came into force in January 2025. Although North America retained a 37.2% share in 2024, Asia-Pacific is advancing the fastest on the back of national data-localization rules and mobile-first consumer banking, contributing a 17.8% regional CAGR to 2030.
Global Cloud Security In Banking Market Trends and Insights
Growing Volume and Sophistication of Cyber-Attacks on Banking Workloads
Financial institutions faced 78% ransomware hit rates in 2024, double the prior year. Attackers are now exploiting API abuse, container misconfigurations, and third-party software flaws-in 1 incident, a cloud misconfiguration exposed nearly 500,000 JPMorgan Chase customers, underlining the new perimeter-free threat surface. Average breach costs reach USD 10 million per incident, prompting urgent migration to behavior analytics-driven zero-trust controls that verify every session and asset. Major banks are embedding continuous compliance scanning and threat-hunting into DevSecOps pipelines to shrink exposure windows from days to hours. Global payments rail SWIFT is piloting federated-learning models with Google Cloud that flag anomalous transactions without moving sensitive data, showing how AI can detect fraud while protecting privacy. As organized crime monetizes access to stolen banking credentials on dark-net markets, proactive cloud segmentation and least-privilege IAM have become board-level priorities.
Real-Time Compliance Automation Requirements (Basel III, DORA, etc.)
The EU's DORA obliges 22,000 financial entities to report severe cyber incidents within 24 hours and test exit plans for critical cloud suppliers, pushing banks to deploy automated evidence-collection engines that feed regulators in near real time. U.S. regulators are moving in the same direction: the Treasury's 2025 cloud resilience report urges continuous control monitoring for systemic institutions. Cloud vendors now bundle mapping templates for Basel III, PCI DSS, and GDPR into dashboards, cutting manual audit workloads by 40%. Banks with global footprints are standardizing on unified compliance fabrics so a single policy set satisfies overlapping jurisdictions-particularly valuable when customer data flows span EU, U.S. and Asia. Early adopters report faster product launches because embedded governance eliminates lengthy security-review cycles, turning compliance from a blocker into a revenue enabler.
Data Residency Conflicts with Multi-Tenant Public Clouds
GDPR, China's CSL, and India's DPDP Act oblige banks to localize data, conflicting with global multi-tenant setups. Sovereign-cloud variants from hyperscalers promise metadata isolation and local key custody, yet still lack the granular placement controls some regulators demand. Smaller APAC markets often enforce data-center-in-country rules that erode economies of scale, nudging banks toward hybrid topologies where sensitive datasets stay on-prem or in local private regions. Resulting architectural complexity inflates cost and elevates configuration-error risk, adding drag to widespread cloud adoption plans. Policymakers are consulting with industry to refine residency stipulations so cyber resilience benefits outweigh jurisdictional concerns, but resolution is unlikely before the end of the decade.
Other drivers and restraints analyzed in the detailed report include:
- Cost Avoidance Through Serverless and Container-Native Security Controls
- Expansion of Open-Banking APIs Driving Zero-Trust Adoption
- Shortage of Cloud-Security-Skilled Talent in Banks' SOC Teams
For complete list of drivers and restraints, kindly check the Table Of Contents.
Segment Analysis
Cloud Identity and Access Management accounted for 29.2% of the cloud security in the banking market share in 2024, reflecting banks' shift from perimeter controls to identity-centric guardrails that authenticate users, services, and APIs at a millisecond scale. As distributed work models persist, IAM consolidates single sign-on, privileged access management, and device posture checks, forming the backbone of zero-trust programs. Vendors are now embedding continuous risk scoring and passwordless flows that trim login friction-a critical user-experience factor in consumer banking.
Cloud Encryption is the fastest segment, posting an 18.2% CAGR through 2030. Quantum-threat awareness and stricter data-protection statutes are pushing banks to deploy hardware security modules and centralized key orchestration. The cloud security in the banking market size for encryption-focused products is forecast to rise alongside pilots of quantum-safe algorithms across payment rails, positioning cryptography as both a compliance must-have and a competitive differentiator. Multi-party computation and format-preserving encryption are gaining traction, letting institutions analyze data without decrypting it, a breakthrough for cross-border fraud analytics and AI model training.
Public-cloud implementations captured 62.4% of the cloud security in the banking market size in 2024, underscoring confidence in hyperscaler defenses, dedicated financial-services regions, and shared-responsibility blueprints. Providers such as AWS and Microsoft report double-digit growth in bank workloads, aided by artifacts like PCI DSS on-demand audit packs that slice assessment times. However, sovereign-cloud and regional-cloud variants illustrate that one model will not fit every jurisdiction, and exit-strategy testing demanded by U.K. supervisors underscores residual concentration risk.
Hybrid-cloud installations are expanding at a 20.1% CAGR because they let banks meet data residency mandates while still bursting to public fabric for analytics surges. Containers and service meshes deliver workload portability, enabling stress-exit drills that shift traffic off a compromised provider within hours. As regulators scrutinize single-vendor dependencies, multi-cloud toolchains are becoming broad metrics for operational resilience, accelerating procurement of abstraction layers that secure and orchestrate across providers.
Cloud Security in Banking Market is Segmented by Software Type (Cloud Identity and Access Management, Cloud Email Security, and More), Deployment Model (Public Cloud, Private Cloud, and Hybrid Cloud), Security Service (Data Security, Application Security, and More), Banking Type (Retail/Consumer Banking, Corporate and Investment Banking, and More), and Geography. The Market Forecasts are Provided in Terms of Value (USD).
Geography Analysis
North America dominated the cloud security in the banking market with a 37.2% share in 2024. Long-standing regulator-vendor dialog, mature private-public threat-sharing, and USD 17 billion in annual tech spending at JPMorgan Chase underline the depth of local demand. The U.S. Treasury's 2025 cloud-resilience study formally encourages critical institutions to adopt multi-cloud while implementing real-time monitoring pipelines, accelerating orders for unified security stacks that can span providers. Canadian regulators now reference zero-trust and secure-API norms explicitly in open-banking guidance, signaling further investment momentum.
Asia-Pacific delivers the fastest CAGR at 17.8% to 2030 as regulators balance data-localization with innovation. Japan's consortium of regional banks adopted a shared hybrid platform running on IBM and Kyndryl infrastructure, illustrating collaborative approaches to cost-effective yet compliant security. Singapore's national digital ID roll-out and Malaysia's RMiT standard also drive the adoption of IAM and real-time monitoring, respectively. China's multi-level protection scheme (MLPS 2.0) compels encryption, continuous monitoring, and onshore key custody, prompting providers to launch local-only regions with hardware attestation.
Europe is accelerating due to DORA and PSD2/PSD3. Italian bank Credem Banca migrated to a specialist security cloud that embeds encryption and real-time incident notification, achieving 20% faster regulatory reporting. The Thales 2024 study notes that 65% of European firms rank cloud security as their second-largest cyber priority, evidencing board-level focus. Multi-cloud resilience drills and sovereign-cloud pilots are now contractual requirements, spurring demand for orchestration layers that enforce policies across Amazon, Microsoft, and Google environments without manual rule duplication.
List of Companies Covered in this Report:
- AWS (Amazon.com, Inc.)
- Google Cloud Platform (Alphabet Inc.)
- Microsoft Azure (Microsoft Corporation)
- IBM Cloud Security (IBM Corporation)
- Oracle Cloud (Oracle Corporation)
- Salesforce, Inc.
- Palo Alto Networks, Inc.
- Fortinet Inc.
- Check Point Software Technologies Ltd.
- Trend Micro Inc.
- CrowdStrike Holdings, Inc.
- Zscaler, Inc.
- Proofpoint Inc.
- Okta, Inc.
- Ping Identity Corporation
- SailPoint Technologies Holdings Inc.
- Netskope, Inc.
- Imperva, Inc.
- Qualys, Inc.
- Rapid7, Inc.
- Sophos Ltd.
- Illumio Inc.
- Akamai Technologies Inc.
- Thales Group (Vormetric)
- Temenos AG
- nCino, Inc.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET LANDSCAPE
- 4.1 Market Overview
- 4.2 Market Drivers
- 4.2.1 Growing volume and sophistication of cyber-attacks on banking workloads
- 4.2.2 Real-time compliance automation requirements (Basel III, DORA, etc.)
- 4.2.3 Cost avoidance through serverless and container-native security controls
- 4.2.4 Expansion of open-banking APIs driving zero-trust adoption
- 4.2.5 AI-powered fraud detection bundled with cloud security suites
- 4.3 Market Restraints
- 4.3.1 Data residency conflicts with multi-tenant public clouds
- 4.3.2 Shortage of cloud-security-skilled talent in banks' SOC teams
- 4.3.3 Hidden dependency risk in third-party fintech integrations
- 4.4 Industry Value Chain Analysis
- 4.5 Regulatory Landscape
- 4.6 Technological Outlook
- 4.7 Industry Attractiveness - Porter's Five Forces Analysis
- 4.7.1 Threat of New Entrants
- 4.7.2 Bargaining Power of Buyers
- 4.7.3 Bargaining Power of Suppliers
- 4.7.4 Threat of Substitutes
- 4.7.5 Intensity of Competitive Rivalry
- 4.8 Impact of Macroeconomic Factors on the Market
5 MARKET SIZE AND GROWTH FORECASTS (VALUES)
- 5.1 By Software Type
- 5.1.1 Cloud Identity and Access Management (IAM)
- 5.1.2 Cloud Email Security
- 5.1.3 Cloud Intrusion Detection and Prevention (IDPS)
- 5.1.4 Cloud Encryption
- 5.1.5 Cloud Network Security
- 5.2 By Deployment Model
- 5.2.1 Public Cloud
- 5.2.2 Private Cloud
- 5.2.3 Hybrid Cloud
- 5.3 By Security Service
- 5.3.1 Data Security
- 5.3.2 Application Security
- 5.3.3 Network Security
- 5.3.4 Security Monitoring and Orchestration (SIEM/SOAR)
- 5.3.5 Identity, Authentication and Fraud Analytics
- 5.4 By Banking Type
- 5.4.1 Retail/Consumer Banking
- 5.4.2 Corporate and Investment Banking
- 5.4.3 Card and Payment Service Providers
- 5.4.4 Digital-Only/Neobanks
- 5.5 By Geography
- 5.5.1 North America
- 5.5.1.1 United States
- 5.5.1.2 Canada
- 5.5.1.3 Mexico
- 5.5.2 South America
- 5.5.2.1 Brazil
- 5.5.2.2 Argentina
- 5.5.2.3 Chile
- 5.5.2.4 Rest of South America
- 5.5.3 Europe
- 5.5.3.1 Germany
- 5.5.3.2 United Kingdom
- 5.5.3.3 France
- 5.5.3.4 Italy
- 5.5.3.5 Spain
- 5.5.3.6 Russia
- 5.5.3.7 Rest of Europe
- 5.5.4 Asia-Pacific
- 5.5.4.1 China
- 5.5.4.2 India
- 5.5.4.3 Japan
- 5.5.4.4 South Korea
- 5.5.4.5 Malaysia
- 5.5.4.6 Singapore
- 5.5.4.7 Australia
- 5.5.4.8 Rest of Asia-Pacific
- 5.5.5 Middle East and Africa
- 5.5.5.1 Middle East
- 5.5.5.1.1 United Arab Emirates
- 5.5.5.1.2 Saudi Arabia
- 5.5.5.1.3 Turkey
- 5.5.5.1.4 Rest of Middle East
- 5.5.5.2 Africa
- 5.5.5.2.1 South Africa
- 5.5.5.2.2 Nigeria
- 5.5.5.2.3 Egypt
- 5.5.5.2.4 Rest of Africa
- 5.5.1 North America
6 COMPETITIVE LANDSCAPE
- 6.1 Market Concentration
- 6.2 Strategic Moves
- 6.3 Market Share Analysis
- 6.4 Company Profiles (includes Global level Overview, Market level overview, Core Segments, Financials as available, Strategic Information, Market Rank/Share for key companies, Products and Services, and Recent Developments)
- 6.4.1 AWS (Amazon.com, Inc.)
- 6.4.2 Google Cloud Platform (Alphabet Inc.)
- 6.4.3 Microsoft Azure (Microsoft Corporation)
- 6.4.4 IBM Cloud Security (IBM Corporation)
- 6.4.5 Oracle Cloud (Oracle Corporation)
- 6.4.6 Salesforce, Inc.
- 6.4.7 Palo Alto Networks, Inc.
- 6.4.8 Fortinet Inc.
- 6.4.9 Check Point Software Technologies Ltd.
- 6.4.10 Trend Micro Inc.
- 6.4.11 CrowdStrike Holdings, Inc.
- 6.4.12 Zscaler, Inc.
- 6.4.13 Proofpoint Inc.
- 6.4.14 Okta, Inc.
- 6.4.15 Ping Identity Corporation
- 6.4.16 SailPoint Technologies Holdings Inc.
- 6.4.17 Netskope, Inc.
- 6.4.18 Imperva, Inc.
- 6.4.19 Qualys, Inc.
- 6.4.20 Rapid7, Inc.
- 6.4.21 Sophos Ltd.
- 6.4.22 Illumio Inc.
- 6.4.23 Akamai Technologies Inc.
- 6.4.24 Thales Group (Vormetric)
- 6.4.25 Temenos AG
- 6.4.26 nCino, Inc.
7 MARKET OPPORTUNITIES AND FUTURE TRENDS
- 7.1 White-Space and Unmet-Need Assessment








