 |
市場調查報告書
商品編碼
1630340
資料竊取:市場佔有率分析、產業趨勢與統計、成長預測(2025-2030)Data Exfiltration - Market Share Analysis, Industry Trends & Statistics, Growth Forecasts (2025 - 2030) |
||||||
※ 本網頁內容可能與最新版本有所差異。詳細情況請與我們聯繫。
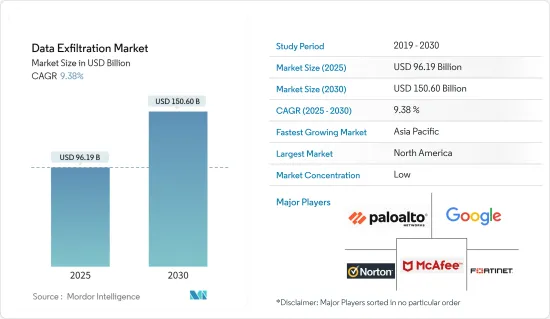
資料竊取市場規模預計到 2025 年為 961.9 億美元,預計到 2030 年將達到 1506 億美元,預測期內(2025-2030 年)複合年成長率為 9.38%。
資料竊取是一種安全漏洞,當組織的敏感資訊未經授權從伺服器或電腦傳輸或複製到威脅行為者控制的位置時,就會發生這種情況。這主要是一種有針對性的攻擊,駭客的主要目標是從資料中複製和提取特定資訊。駭客透過遠端程式或安裝可攜式媒體設備直接存取目標系統。個人健康資訊、公司智慧財產權和商業機密、個人識別資訊以及信用卡和銀行詳細資訊等財務資訊都屬於大規模資料外洩。
主要亮點
- 不斷成長的企業資料通常包括有價值的資產,例如客戶資訊、智慧財產權、商業機密、財務記錄和其他敏感資料。這使得企業很容易成為資料竊取攻擊的目標。保護這些寶貴的資產推動了對先進預防解決方案的需求。
- 嚴格的資料保護監管要求在推動資料防盜需求方面發揮關鍵作用。各種資料保護法規,例如通用資料保護法規 (GDPR)、加州消費者隱私法案 (CCPA) 以及其他區域或特定產業保護條例,都要求採取措施保護敏感資料未授權存取,包括資料竊取是組織的要求。遵守這些法規對於避免法律處罰、聲譽損害和失去客戶信任極為重要。
- 本地環境中資料遺失事件的增加增加了預防資料竊取的需求。在本地環境中,IT 系統可以複雜地互連,從而存在潛在的漏洞。惡意行為者可能會利用這些漏洞來獲得未授權存取並洩露敏感資料。本地環境中資料遺失事件的增加突顯需要強大的資料防盜解決方案來防範此類威脅。
- 本地應用程式和雲端環境之間的相容性問題將是一個挑戰,並可能限制資料防盜市場。在本地應用程式與雲端服務互動的混合環境中,確保全面的資料可見性和監控非常困難。資料防盜解決方案通常依賴監控網路流量、使用者行為和資料存取模式來偵測和防止詐欺的資料傳輸。然而,相容性問題可能會妨礙本地和雲端環境之間的無縫監控,並限制資料竊取預防措施的有效性。
- COVID-19 大流行對網路安全的各個方面產生了重大影響,包括資料竊取市場。疫情期間,遠距工作的採用有所增加,組織迅速調整了IT基礎設施和安全措施。這種快速的變化帶來了新的漏洞和挑戰,因為遠距工作環境預計將具有與傳統本地環境不同的安全控制。攻擊者利用這些漏洞來攻擊遠端工作人員並獲得對敏感資料的未授權存取,從而增加了資料被盜的風險。
資料竊取市場趨勢
醫療保健和生命科學最終用戶領域預計將佔據主要市場佔有率
- 由於所涉及資料(包括患者醫療記錄、臨床試驗資料、知識產權和專有研究)的敏感性,資料盜竊是醫療保健和生命科學行業的一個主要問題。未授權存取此類資料可能會產生嚴重後果,包括侵犯患者隱私、聲譽受損、不合規以及研究和開發工作受損。
- 在醫療保健產業,保護病患資料是重中之重。個人健康資訊 (PHI) 和電子健康記錄(EHR) 包含高度敏感的訊息,是網路犯罪分子的有吸引力的目標。醫療保健領域的資料外洩可能會給患者帶來嚴重後果,包括身分盜竊和保險詐騙。
- 勒索軟體攻擊的增加可能對資料竊取事件的發生率和規模產生直接影響。根據 IC3 和 FBI 的數據,2022 年,美國網路犯罪申訴中心 (IC3) 收到 210 起申訴,顯示全球醫療機構遭到勒索軟體攻擊。
- 醫療保健產業受到各種法規和資料保護標準的約束,例如美國的 HIPAA(健康保險流通與責任法案)和歐盟的 GDPR(一般資料保護規範)。這些法規要求嚴格的控制和通訊協定來保護患者資料,包括防止資料外洩的措施。
- 醫療保健和生命科學產業面臨各種網路威脅。這包括勒索軟體攻擊、網路釣魚嘗試、社會工程、惡意軟體感染、內部威脅等等。威脅行為者可以針對醫療保健組織竊取有價值的資料、擾亂業務或強制支付贖金。
預計北美將佔據較大市場佔有率
- 資料竊取是北美的一個主要問題。北美是各行各業眾多組織的所在地,這使其成為網路犯罪分子的一個有吸引力的目標,這些網路犯罪分子試圖竊取敏感資料以獲取經濟利益、間諜活動或其他邪惡目的。
- 北美出現了許多在國內和國際上進行資料竊取活動的網路犯罪集團。這些團體的動機各不相同,包括經濟利益、政治議程和國家間諜活動。他們使用複雜的技術、工具和策略來突破安全防禦並竊取資料。
- 美國和加拿大等北美國家已經建立了保護敏感資料的法律規範。例如,在美國,組織必須遵守各種特定於行業的法規,例如針對醫療保健的 HIPAA(健康保險互通性與課責法案)和針對金融機構的 GLBA(美國金融服務業現代化法)。遵守這些法規允許組織實施安全措施以降低資料被盜的風險。
- 北美的組織實施了各種安全措施來防止資料被盜。這包括強大的防火牆、入侵偵測和預防系統、端點保護、加密技術、存取控制、員工培訓、意識提升計劃、事件回應計劃以及早期偵測滲透嘗試的持續努力,其中包括引入全面的監控。
資料竊取產業概述
資料竊取市場高度分散,主要參與者包括 Norton LifeLock、McAfee LLC、Palo Alto Networks、Google LLC 和 Fortinet。市場參與者正在採取聯盟和收購等策略來增強其產品供應並獲得永續的競爭優勢。
2022 年 10 月,Fortinet 為遠端使用者提供網路和安全融合。 FortiSASE 現在具有下一代雙模式 CASB,可實現對 SaaS 應用程式的廣泛可見性和控制。 FortiSASE 透過採用內聯和基於 API 的功能來解決影子 IT 和資料竊取挑戰,提供對已通過核准和核准的應用程式的全面可見性。
2022 年 9 月,全球線上保護領域的先驅之一麥克菲 (McAfee Corp.) 宣佈在澳洲推出 McAfee+。這是一條新產品線,包括全新的隱私和身分保護措施,使用戶能夠安全可靠地過著線上生活。
其他好處
- Excel 格式的市場預測 (ME) 表
- 3 個月分析師支持
目錄
第1章簡介
- 研究假設和市場定義
- 調查範圍
第2章調查方法
第3章執行摘要
第4章市場洞察
- 市場概況
- 產業價值鏈分析
- 產業吸引力-波特五力分析
- 買家/消費者的議價能力
- 供應商的議價能力
- 新進入者的威脅
- 替代品的威脅
- 競爭公司之間敵對關係的強度
- 評估 COVID-19 對產業的影響
第5章市場動態
- 市場促進因素
- 企業資料量快速成長,對資料防盜解決方案的需求
- 嚴格的資料保護監管要求
- 本地環境中的資料遺失增加
- 市場限制因素
- 本機應用程式和雲端環境之間的相容性問題
第6章 市場細分
- 按組織規模
- 中小企業 (SME)
- 主要企業
- 按成分
- 解決方案(加密、防毒、防火牆、入侵偵測系統、預防資料外泄等解決方案)
- 服務(穿透測試服務、支援與維護、整合服務、支援與維護、諮詢服務)
- 按行業分類
- 銀行、金融服務和保險 (BFSI)
- 資訊科技和電訊
- 醫療保健/生命科學
- 政府/國防
- 零售/電子商務
- 製造業
- 其他最終用戶產業
- 按地區
- 北美洲
- 美國
- 加拿大
- 歐洲
- 德國
- 英國
- 法國
- 其他歐洲國家
- 亞太地區
- 印度
- 中國
- 日本
- 其他亞太地區
- 拉丁美洲
- 巴西
- 阿根廷
- 其他拉丁美洲
- 中東/非洲
- 阿拉伯聯合大公國
- 沙烏地阿拉伯
- 其他中東和非洲
- 北美洲
第7章 競爭格局
- 公司簡介
- NortonLifeLock
- McAfee LLC
- Palo Alto Networks
- Google LLC
- Fortinet
- HP Inc
- Cisco Systems inc.
- GTB Technologies
- Check Point Software Technologies
- Juniper Networks
- Hackerone Inc
- Barracuda Networks
- Sophos Group plc
- Zscaler
- 投資分析
第8章 市場機會及未來趨勢
The Data Exfiltration Market size is estimated at USD 96.19 billion in 2025, and is expected to reach USD 150.60 billion by 2030, at a CAGR of 9.38% during the forecast period (2025-2030).

Data exfiltration is a security breach that occurs when sensitive information from an organization is transferred or copied without authorization from a server or a computer to a location controlled by a threat actor. It is primarily a targeted attack in which the hacker's primary goal is to copy and extract specific information from the data. Hackers directly access the targeted system via remote programs or by installing a portable media device. Personal health information, intellectual property or trade secrets of a firm, personally identifiable information, and financial information, such as credit card or bank details, are all large data breaches.
Key Highlights
- The increasing volumes of enterprise data often contain valuable assets such as customer information, intellectual property, trade secrets, financial records, and other sensitive data. This makes organizations attractive targets for data exfiltration attacks. Protecting these valuable assets drives the demand for advanced prevention solutions.
- Strict regulatory requirements for data protection play a crucial role in driving the need for data exfiltration prevention. Various data protection regulations, such as the General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and other regional or industry-specific regulations, mandate organizations to implement measures to protect sensitive data from unauthorized access, including data exfiltration. Compliance with these regulations is crucial to avoid legal penalties, reputational damage, and loss of customer trust.
- Increasing data loss incidents in the on-premises environment can drive the need for data exfiltration prevention. On-premises environments may have complex and interconnected IT systems, which can introduce vulnerabilities. Malicious actors can exploit these vulnerabilities to gain unauthorized access and exfiltrate sensitive data. The increasing data loss incidents in on-premises environments highlight the need for robust data exfiltration prevention solutions to protect against such threats.
- Compatibility issues between on-premises applications and the cloud environment can pose challenges and restrain the data exfiltration prevention market. Ensuring comprehensive data visibility and monitoring in a hybrid environment where on-premises applications interact with cloud services can be challenging. Data exfiltration prevention solutions often rely on monitoring network traffic, user behavior, and data access patterns to detect and prevent unauthorized data transfers. However, compatibility issues may hinder seamless monitoring across on-premises and cloud environments, limiting the effectiveness of data exfiltration prevention measures.
- The COVID-19 pandemic significantly impacted various aspects of the cybersecurity landscape, including the data exfiltration market. With the increased adoption of remote work during the pandemic, organizations rapidly adjusted their IT infrastructure and security measures. This sudden shift introduced new vulnerabilities and challenges, as remote work environments were expected to have different security controls than traditional on-premises setups. Attackers exploited these vulnerabilities to target remote workers and gain unauthorized access to sensitive data, increasing the risk of data exfiltration.
Data Exfiltration Market Trends
Healthcare and Life Sciences End User Segment is Expected to Hold Significant Market Share
- Data exfiltration is a significant concern in the healthcare and life sciences industry due to the sensitive nature of the data involved, such as patient medical records, clinical trial data, intellectual property, and proprietary research. Unauthorized access to this data can lead to severe consequences, including patient privacy breaches, reputational damage, regulatory non-compliance, and compromised research and development efforts.
- Protecting patient data is a top priority in the healthcare industry. Personal health information (PHI) and electronic health records (EHRs) contain highly sensitive information and are attractive targets for cybercriminals. Data breaches in healthcare can result in identity theft, insurance fraud, and other serious consequences for patients.
- Increasing ransomware attacks can directly impact the prevalence and scale of data exfiltration incidents. According to IC3 and FBI, In 2022, the U.S. Internet Crime Complaint Center (IC3) received 210 complaints indicating ransomware attacks on healthcare organizations globally.
- The healthcare industry is subject to various regulations and data protection standards, including the Health Insurance Portability and Accountability Act (HIPAA) in the United States and the General Data Protection Regulation (GDPR) in the European Union. These regulations mandate strict controls and protocols for safeguarding patient data, including measures to prevent data exfiltration.
- The healthcare and life sciences industry faces a diverse range of cyber threats. These include ransomware attacks, phishing attempts, social engineering, malware infections, and insider threats. Threat actors may target healthcare organizations to steal valuable data, disrupt operations, or extort ransom payments.
North America is Expected to Hold Significant Market Share
- Data exfiltration is a significant concern in North America. North America houses many organizations across various industries, making it an attractive target for cybercriminals seeking to steal sensitive data for financial gain, espionage, or other malicious purposes.
- North America has seen the emergence of numerous cybercriminal groups, both domestic and international, engaged in data exfiltration activities. These groups may have different motivations, such as financial gain, political agendas, or state-sponsored espionage. They use sophisticated techniques, tools, and tactics to defy security defenses and steal data.
- North American countries like the United States and Canada have established regulatory frameworks to protect sensitive data. For instance, in the United States, organizations are subject to various industry-specific regulations, including HIPAA (Health Insurance Portability and Accountability Act) for healthcare and the Gramm-Leach-Bliley Act (GLBA) for financial institutions. Compliance with these regulations helps organizations implement security measures to mitigate data exfiltration risks.
- Organizations in North America implement a range of security measures to protect against data exfiltration. These include implementing robust firewalls, intrusion detection and prevention systems, endpoint protection, encryption technologies, access controls, employee training, awareness programs, incident response plans, and continuous monitoring for early detection of exfiltration attempts.
Data Exfiltration Industry Overview
The Data Exfiltration Market is highly fragmented, with major players like Norton LifeLock, McAfee LLC, Palo Alto Networks, Google LLC, and Fortinet. Players in the market are adopting strategies such as partnerships and acquisitions to enhance their product offerings and gain sustainable competitive advantage.
In October 2022, Fortinet offered networking and security convergence to remote users. FortiSASE now includes a next-generation dual-mode CASB, providing extensive visibility and control for SaaS applications. FortiSASE provides comprehensive visibility into sanctioned and unsanctioned apps by employing inline and API-based capabilities to handle shadow IT and data exfiltration challenges.
In September 2022, McAfee Corp., one of the global pioneers in online protection, announced the launch of McAfee+ in Australia, a new product line including all-new privacy and identity safeguards that enabled users to live their lives online safely and securely.
Additional Benefits:
- The market estimate (ME) sheet in Excel format
- 3 months of analyst support
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 Study Assumptions and Market Definition
- 1.2 Scope of the Study
2 RESEARCH METHODOLOGY
3 EXECUTIVE SUMMARY
4 MARKET INSIGHTS
- 4.1 Market Overview
- 4.2 Industry Value Chain Analysis
- 4.3 Industry Attractiveness - Porter's Five Forces Analysis
- 4.3.1 Bargaining Power of Buyers/Consumers
- 4.3.2 Bargaining Power of Suppliers
- 4.3.3 Threat of New Entrants
- 4.3.4 Threat of Substitute Products
- 4.3.5 Intensity of Competitive Rivalry
- 4.4 Assessment of the COVID-19 Impact on the Industry
5 MARKET DYNAMICS
- 5.1 Market Drivers
- 5.1.1 Exponential Growth in the Volumes of Enterprise Data and the Need for Data Exfiltration Prevention Solutions
- 5.1.2 Strict Regulatory Requirements for Data Protection
- 5.1.3 Increasing Incidents of Data Loss in the On-Premises Environment
- 5.2 Market Restraints
- 5.2.1 Compatibility Issues Between On-premises Application and the Cloud Environment
6 MARKET SEGMENTATION
- 6.1 By Organization Size
- 6.1.1 Small- and Medium-sized Enterprises (SMEs)
- 6.1.2 Large Enterprise
- 6.2 By Component
- 6.2.1 Solutions (Encryption, Antivirus, Firewall, Intrusion Detection System, Data Loss Prevention and Other Solutions)
- 6.2.2 Services (Penetration Testing Services, Support and Maintenance, Integration Services, Support and Maintenance, and Consulting Services)
- 6.3 By End-user Vertical
- 6.3.1 Banking, Financial Services, and Insurance (BFSI)
- 6.3.2 IT and Telecom
- 6.3.3 Healthcare and Life Sciences
- 6.3.4 Government and Defense
- 6.3.5 Retail and E-commerce
- 6.3.6 Manufacturing
- 6.3.7 Other End-user Verticals
- 6.4 By Geography
- 6.4.1 North America
- 6.4.1.1 United States
- 6.4.1.2 Canada
- 6.4.2 Europe
- 6.4.2.1 Germany
- 6.4.2.2 United Kingdom
- 6.4.2.3 France
- 6.4.2.4 Rest of Europe
- 6.4.3 Asia-Pacific
- 6.4.3.1 India
- 6.4.3.2 China
- 6.4.3.3 Japan
- 6.4.3.4 Rest of Asia-Pacific
- 6.4.4 Latin America
- 6.4.4.1 Brazil
- 6.4.4.2 Argentina
- 6.4.4.3 Rest of Latin America
- 6.4.5 Middle-East and Africa
- 6.4.5.1 United Arab Emirates
- 6.4.5.2 Saudi Arabia
- 6.4.5.3 Rest of Middle-East and Africa
- 6.4.1 North America
7 COMPETITIVE LANDSCAPE
- 7.1 Company Profiles
- 7.1.1 NortonLifeLock
- 7.1.2 McAfee LLC
- 7.1.3 Palo Alto Networks
- 7.1.4 Google LLC
- 7.1.5 Fortinet
- 7.1.6 HP Inc
- 7.1.7 Cisco Systems inc.
- 7.1.8 GTB Technologies
- 7.1.9 Check Point Software Technologies
- 7.1.10 Juniper Networks
- 7.1.11 Hackerone Inc
- 7.1.12 Barracuda Networks
- 7.1.13 Sophos Group plc
- 7.1.14 Zscaler
- 7.2 Investment Analysis







