 |
市場調查報告書
商品編碼
1901403
全球身分和存取管理市場按產品、技術、類型、身分類型、部署類型、垂直產業和地區分類-預測至2030年Identity and Access Management Market by Technology (Access Management, Identity Governance & Administration, Privileged Access Management ), Type, Identity Type, Deployment Mode, Vertical - Global Forecast to 2030 |
||||||
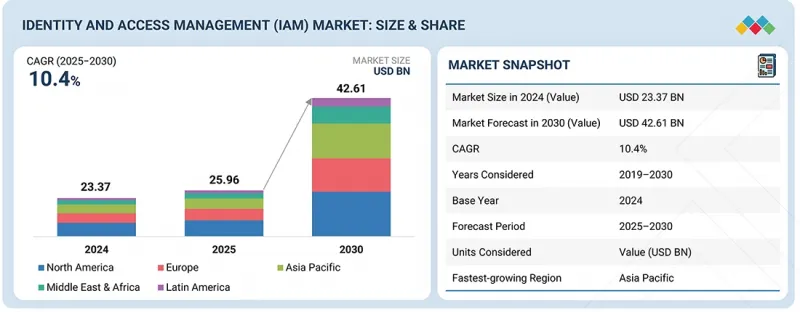
預計身分和存取管理 (IAM) 市場規模將從 2025 年的 259.6 億美元成長到 2030 年的 426.1 億美元,預測期內複合年成長率為 10.4%。
雲端運算、零信任框架和人工智慧驅動的存取控制的日益普及,正透過自適應身份驗證、即時威脅偵測和無縫用戶配置,變革身分與存取管理 (IAM)。人工智慧驅動的異常檢測和基於風險的存取控制,已將未授權存取事件減少了 85% 以上,從而幫助企業提升安全性和合規性。
| 調查範圍 | |
|---|---|
| 調查期 | 2019-2030 |
| 基準年 | 2024 |
| 預測期 | 2025-2030 |
| 目標單元 | 金額(百萬美元/十億美元) |
| 部分 | 依產品/服務、技術、類型、身分類型、部署類型、產業垂直領域、地區 |
| 目標區域 | 北美、歐洲、亞太地區、中東和非洲以及拉丁美洲 |
同時,多因子身分驗證 (MFA)、單一登入 (SSO) 和特權存取管理 (PAM) 解決方案的日益普及,正在加強存取管治,促進安全入職,並推動企業數位轉型。然而,人們對資料隱私、內部威脅和存取策略配置錯誤的擔憂日益加劇,導致企業在更廣泛地採用這些解決方案方面猶豫不決。複雜的監管要求以及員工對身分和存取管理 (IAM) 最佳實踐缺乏了解,進一步限制了這些解決方案的大規模應用。
在身分與存取管理 (IAM) 市場中,零售和電子商務行業正經歷最快的成長,這主要受帳戶盜用、撞庫人員編制和內部威脅日益猖獗以及客戶和員工對無縫存取體驗的需求不斷成長的推動。例如,預計到 2024 年,電子商務平台平均將有 2.1% 的交易受到未授權存取的影響,是行業平均水平的 20 倍以上。這主要是由於未經授權的登入試驗和憑證洩漏事件的急劇增加所致。同時,超過 60% 的北美零售商表示,與存取相關的安全事件逐年增加,這促使他們採用多因素身份驗證 (MFA)、單一登入 (SSO) 和人工智慧驅動的存取分析技術。此外,消費者和員工對流暢的登入體驗和安全的遠端存取的需求,也迫使零售商投資於自適應身份驗證、行為生物識別和集中式存取管治解決方案。
在身分與存取管理 (IAM) 市場,混合部署模式正迅速普及,因為企業希望兼顧本地控制的柔軟性和雲端的可擴展性及成本效益。混合 IAM 解決方案使企業能夠集中管理舊有系統和現代 SaaS 應用程式的存取權限,從而確保安全策略的一致性和集中管治。近期的行業報告顯示,超過 78% 的企業在實施混合 IAM 架構後,存取管理效率得到了提升。與純本地部署或純雲端部署相比,混合 IAM 解決方案更加靈活,因為它們不僅能夠無縫採用自適應身份驗證、多因素身份驗證 (MFA) 和單點登入 (SSO),還支援逐步遷移到雲端環境。
預計到2025年,北美將佔據身分與存取管理(IAM)市場最大的佔有率,這主要得益於其成熟的法規環境、對高階存取控制的早期採用以及對網路安全的大力投入。聯邦和州政府層級的各項舉措,例如推廣零信任框架、與NIST和GDPR合規標準接軌,以及在銀行、醫療保健、零售和政府部門推廣企業級IAM,都在增強安全存取、互通性和風險緩解能力。此外,廣泛的雲端技術應用、成熟的IAM供應商生態系統以及公私合營模式,正在確保組織和用戶網路擁有強大的身份管治、安全的遠端存取和可擴展的身份驗證基礎設施。
同時,亞太地區預計將迎來快速成長,這得益於加速的數位轉型、不斷提高的網路和行動網路普及率,以及政府主導的強力的數位身分舉措。印度、日本、中國和新加坡等國家正優先採用生物識別、身分聯合和大規模數位身分框架,以加強安全並改善公民和客戶體驗。混合辦公環境下對安全存取日益成長的需求、雲端技術的廣泛應用,以及對人工智慧驅動的身份驗證和詐欺預防的投資,正在推動身分和存取管理(IAM)在銀行、金融和保險(BFSI)、零售、醫療保健、政府以及資訊科技和資訊科技及相關服務(IT/ITeS)等行業的快速發展。
主要調查主題細分
IAM市場的主要供應商包括:微軟(美國)、Ping Identity(美國)、IBM(美國)、Okta(美國)、Oracle(美國)、SailPoint(美國)、Saviynt(美國)、CyberArk(美國)、泰雷茲(美國)、Akamai Technologies(美國)、OpenText(美國)、美國)、Entr) Global(美國)、Evidian(法國)、RSA Security(美國)、Avatier(美國)、ManageEngine(美國)、SecureAuth(美國)、EmpowerID(美國)、Simeio(美國)、One Identity(美國)、FusionAuth(美國)、Auth0(美國)、IDnow(德國)、Zona 它(美國)、美國)、Auth0(美國)。 Identity(美國)、Delinea(美國)、Optimal IdM(美國)、Netwrix(美國)、Aquera(美國)、Cerby(美國)。 Traxion(荷蘭)和 Radiant 其中包括 Logic(美國)、Elimity(比利時)、Oleria(美國)、Veza(美國)、Bravura Security(加拿大)、Fischer Identity(美國)、Lumos(美國)、Omada(丹麥)、OpenIAM(美國)、Pathlock(美國)、Tuebora(美國)、美國)。
該研究包括對 IAM 市場主要參與企業的詳細競爭分析、公司簡介、最新發展和關鍵市場策略。
調查範圍
本報告根據產品(解決方案和服務)、技術(存取管理、身分管治和管理 (IGA)、特權存取管理 (PAM) 等)、類型(員工 IAM、消費者 IAM、B2B IAM)、身分類型(人類身分和非人類身分)、部署模式(雲端、本地部署、混合部署)和產業垂直領域(銀行、金融和保險 (BFSI)、零售、政府和金融服務與運輸市場進行細分,並預測市場規模。
該研究還涵蓋了對市場主要參與企業的詳細競爭分析、公司簡介、有關產品和業務供應的關鍵觀察、近期發展和關鍵市場策略。
購買本報告的主要好處
本報告為市場領導和新參與企業提供關於身分與存取管理 (IAM) 市場及其細分市場整體收入規模的最準確估計值。它幫助相關人員了解競爭格局,並提供有價值的見解,以幫助他們加強市場定位並制定合適的打入市場策略。此外,本報告還深入分析了市場趨勢,並提供了關鍵市場促進因素、限制、挑戰和機會的資訊。
目錄
第1章 引言
第2章執行摘要
第3章重要考察
第4章 市場概覽
- 市場動態
- 未滿足的需求和差距
- 相互關聯的市場與跨產業機遇
- 1/2/3級參與企業的策略舉措
第5章 產業趨勢
- 波特五力分析
- 總體經濟指標
- 價值鏈分析
- 生態系分析
- 定價分析
- 貿易分析
- 大型會議和活動
- 影響客戶業務的趨勢與干擾因素
- 投資和資金籌措方案
- 身分和存取管理市場框架
- 身分和存取管理的發展
- 案例研究分析
- 2025年美國關稅的影響-身分和存取管理解決方案市場
第6章:技術進步、人工智慧的影響、專利、創新與未來應用
- 關鍵新興技術
- 互補技術
- 技術/產品藍圖
- 專利分析
- 未來應用
- 人工智慧/生成式人工智慧對身分和存取管理市場的影響
- 成功案例和實際應用
第7章 監理環境
- 地方法規和合規性
- 監管機構、政府機構和其他組織
- 業界標準
第8章:消費者趨勢與購買行為
- 決策流程
- 買方相關人員和採購評估標準
- 招募障礙和內部挑戰
- 各個終端用戶產業中尚未滿足的需求
- 市場盈利
9. 身份和訪問管理市場(按產品/服務分類)
- 解決方案
- 服務
10. 按技術分類的身份和訪問管理市場
- 存取管理
- 身分管治與管理(IGA)
- 特權存取管理 (PAM)
- 其他
11. 按類型分類的身份和訪問管理市場
- 員工身分和存取管理
- 消費者身分與存取管理
- B2B IAM
12. 身分和存取管理市場(按身分類型分類)
- 人類身分
- 非人類身分
13. 按部署類型分類的身份和存取管理市場
- 雲
- 本地部署
- 混合
14. 身份和訪問管理市場(按垂直行業分類)
- BFSI
- 旅遊、觀光和酒店
- 衛生保健
- 零售與電子商務
- 資訊科技與資訊科技服務
- 教育
- 政府和國防部
- 其他
15. 按地區分類的身份和訪問管理市場
- 北美洲
- 北美:身分和存取管理市場促進因素
- 美國
- 加拿大
- 歐洲
- 歐洲:身分和存取管理市場促進因素
- 英國
- 德國
- 法國
- 義大利
- 其他
- 亞太地區
- 亞太地區身分和存取管理市場促進因素
- 中國
- 日本
- 印度
- 其他
- 中東和非洲
- 中東和非洲:身分和存取管理市場促進因素
- GCC
- 南非
- 其他
- 拉丁美洲
- 拉丁美洲:身份和訪問管理市場促進因素
- 巴西
- 墨西哥
- 其他
第16章 競爭格局
- 概述
- 主要參與企業的策略/優勢
- 收入分析
- 市佔率分析
- 品牌對比
- 估值和財務指標
- 公司估值矩陣:主要參與企業,2024 年
- 公司估值矩陣:Start-Ups/中小企業,2024 年
- 競爭格局和趨勢
第17章:公司簡介
- 主要參與企業
- MICROSOFT
- PING IDENTITY
- IBM
- OKTA
- ORACLE
- SAILPOINT
- SAVIYNT
- CYBERARK
- THALES
- AKAMAI TECHNOLOGIES
- OPENTEXT
- ENTRUST
- DUO SECURITY
- HID GLOBAL
- EVIDIAN
- 其他主要企業
- RSA SECURITY
- AVATIER
- MANAGEENGINE
- SECUREAUTH
- EMPOWERID
- SIMEIO
- ONE IDENTITY
- FUSIONAUTH
- AUTH0
- IDNOW
- ZUORA
- SIGNZY
- CIVIC TECHNOLOGIES
- TRUSONA
- BEYOND IDENTITY
- DELINEA
- OPTIMAL IDM
- NETWRIX
- AQUERA
- CERBY
- TRAXION
- RADIANT LOGIC
- ELIMITY
- OLERIA
- VEZA
- BRAVURA SECURITY
- FISCHER IDENTITY
- LUMOS
- OMADA
- OPENIAM
- PATHLOCK
- TUEBORA
- RIPPLING
第18章調查方法
第19章附錄
The identity and access management (IAM) market is projected to grow from USD 25.96 billion in 2025 to USD 42.61 billion by 2030 at a compound annual growth rate (CAGR) of 10.4% during the forecast period. The increasing adoption of cloud computing, zero-trust frameworks, and AI-powered access controls is transforming IAM by enabling adaptive authentication, real-time threat detection, and seamless user provisioning. AI-driven anomaly detection and risk-based access controls are helping reduce unauthorized access incidents by over 85%, thus enhancing organizational security and compliance.
| Scope of the Report | |
|---|---|
| Years Considered for the Study | 2019-2030 |
| Base Year | 2024 |
| Forecast Period | 2025-2030 |
| Units Considered | Value (USD Million/USD Billion) |
| Segments | Offering, Technology, Type, Identity Type, Deployment Mode, Vertical, and Region |
| Regions covered | North America, Europe, Asia Pacific, Middle East & Africa, and Latin America |
Simultaneously, the growing implementation of multi-factor authentication (MFA), single sign-on (SSO), and privileged access management (PAM) solutions is strengthening access governance, facilitating secure onboarding, and driving digital transformation across enterprises. However, rising concerns over data privacy, insider threats, and misconfigured access policies are creating hesitation in broader adoption. Complex regulatory requirements and a lack of employee awareness about IAM best practices further constrain large-scale deployment.

"By vertical, the retail & e-commerce segment is projected to register the highest CAGR during the forecast period"
The retail and e-commerce sector is experiencing the fastest growth within the IAM market due to rising instances of account takeovers, credential stuffing, and insider threats, alongside growing demands for seamless customer and employee access. For example, e-commerce platforms reported an average of 2.1% of transactions impacted by unauthorized access in 2024, over twenty times the industry benchmark, with fraudulent login attempts and compromised credentials surging. Meanwhile, over 60% of retailers in North America noted year-on-year increases in access-related security incidents, driving adoption of MFA, SSO, and AI-powered access analytics. Simultaneously, consumers and employees demand frictionless login experiences and secure remote access, prompting retailers to invest in adaptive authentication, behavioral biometrics, and centralized access governance solutions.
"By deployment mode, the hybrid segment is projected to exhibit the highest CAGR during the forecast period"
The IAM market's hybrid deployment mode is experiencing rapid adoption as organizations seek the flexibility of combining on-premises control with cloud scalability and cost efficiency. Hybrid IAM solutions allow enterprises to manage access across both legacy systems and modern SaaS applications, ensuring consistent security policies and centralized governance. According to a recent industry report, over 78% of organizations observed improved access management efficiency after implementing hybrid IAM architectures. These solutions also enable the seamless adoption of adaptive authentication, MFA, and SSO, while supporting a gradual migration to cloud environments, making them more versatile than purely on-premises or cloud-only deployments.
"North America is estimated to have the largest market share in 2025, and Asia Pacific is expected to witness the fastest growth rate during the forecast period"
North America is estimated to hold the largest share of the IAM market in 2025, driven by a mature regulatory environment, early adoption of advanced access controls, and strong cybersecurity investment. Federal and state initiatives promoting zero-trust frameworks, compliance with NIST and GDPR-aligned standards, and enterprise-grade IAM deployments across banking, healthcare, retail, and government sectors have strengthened secure access, interoperability, and risk mitigation. Additionally, widespread cloud adoption, established IAM vendor ecosystems, and coordinated public-private collaborations ensure robust identity governance, secure remote access, and scalable authentication infrastructure across organizations and user networks.
Meanwhile, the Asia Pacific region is expected to witness rapid growth, driven by accelerated digital transformation, expanding internet and mobile penetration, and strong government-led digital identity initiatives. Countries such as India, Japan, China, and Singapore are prioritizing biometric authentication, identity federation, and large-scale digital ID frameworks to strengthen security and improve citizen and customer experiences. Rising demand for secure access in hybrid work environments, increasing cloud adoption, and investments in AI-powered identity verification and fraud prevention are fueling IAM expansion across BFSI, retail, healthcare, government, and IT & ITeS sectors.
Breakdown of Primaries
The study draws insights from various industry experts, including component suppliers, Tier 1 companies, and OEMs. The break-up of the primaries is as follows:
- By Company Type: Tier 1 - 40%, Tier 2 - 35%, and Tier 3 - 25%
- By Designation: C-Level Executives - 35%, Managerial and Other Levels - 65%
- By Region: North America - 15%, Europe - 25%, Asia Pacific - 30%, Middle East & Africa - 20%, Latin America - 10%
Major vendors in the IAM market include Microsoft (US), Ping Identity (US), IBM (US), Okta (US), Oracle (US), SailPoint (US), Saviynt (US), CyberArk (US), Thales (France), Akamai Technologies (US), OpenText (Canada), Entrust (US), Duo Security (US), HID Global (US), Evidian (France), RSA Security (US), Avatier (US), ManageEngine (US), SecureAuth (US), EmpowerID (US), Simeio (US), One Identity (US), FusionAuth (US), Auth0 (US), IDnow (Germany), Zuora (US), Signzy (India), Civic Technologies (US), Trusona (US), Beyond Identity (US), Delinea (US), Optimal IdM (US), Netwrix (US), Aquera (US), Cerby (US), Traxion (Netherlands), Radiant Logic (US), Elimity (Belgium), Oleria(US), Veza (US), Bravura Security (Canada), Fischer Identity (US), Lumos (US), Omada (Denmark), OpenIAM (US), Pathlock (US), Tuebora (US), and Rippling (US).
The study includes an in-depth competitive analysis of the key players in the IAM market, their company profiles, recent developments, and key market strategies.
Research Coverage
The report segments the IAM market and forecasts its size based on offering (solutions and services), technology (access management, identity governance and administration (IGA), privileged access management (PAM), and others), type (workforce IAM, consumer IAM, and B2B IAM), identity type (human identity and non-human identity), deployment mode (cloud, on-premises, and hybrid), and vertical (BFSI, travel, tourism and hospitality, healthcare, retail and e-commerce, IT & ITeS, education, government & defense, and others).
The study also includes an in-depth competitive analysis of the market's key players, their company profiles, key observations related to product and business offerings, recent developments, and key market strategies.
Key Benefits of Buying the Report
The report will help market leaders/new entrants with information on the closest approximations of revenue numbers for the overall IAM market and its subsegments. This report will help stakeholders understand the competitive landscape and gain valuable insights to better position their businesses and plan suitable go-to-market strategies. The report also helps stakeholders understand the market pulse and provides information on key market drivers, restraints, challenges, and opportunities.
The report provides insights into the following pointers:
- Analysis of key drivers (rising instances of security breaches and identity-related fraud; growing awareness about compliance management; cloud-centric transformation fuels need for unified access; increasing need for identity access management solutions for IoT; growing adoption of IAM solutions by SMEs), restraints (lack of identity standards and budgetary constraints in deploying IAM solutions; privacy concerns in IAM adoption; complexity in integrating IAM with legacy systems), opportunities (cultural shift from traditional IAM to CIAM; proliferation of cloud-based IAM solutions and services and growing adoption of hybrid cloud model; increasing integration of technologies into IAM; rising demand for AI-driven and adaptive authentication solutions), and challenges (scarcity of skilled cybersecurity professionals among enterprises; difficulties addressing complexity of advanced threats; interoperability and integration issues across diverse IT environments)
- Product Development/Innovation: Detailed insights into upcoming technologies, research & development activities, and new product & service launches in the IAM market
- Market Development: Comprehensive information about lucrative markets - analysis of the IAM market across varied regions
- Market Diversification: Exhaustive information about new products & services, untapped geographies, recent developments, and investments in the IAM market
- Competitive Assessment: In-depth assessment of market shares, growth strategies, and service offerings of leading players in the IAM market, including Microsoft (US), Ping Identity (US), IBM (US), Okta (US), and Oracle (US).
TABLE OF CONTENTS
1 INTRODUCTION
- 1.1 STUDY OBJECTIVES
- 1.2 MARKET DEFINITION
- 1.3 STUDY SCOPE AND SEGMENTATION
- 1.3.1 MARKET SEGMENTATION
- 1.3.2 INCLUSIONS & EXCLUSIONS
- 1.3.3 YEARS CONSIDERED
- 1.3.4 CURRENCY CONSIDERED
- 1.3.5 STAKEHOLDERS
- 1.3.6 SUMMARY OF CHANGES
2 EXECUTIVE SUMMARY
- 2.1 MARKET HIGHLIGHTS AND KEY INSIGHTS
- 2.2 KEY MARKET PARTICIPANTS: MAPPING OF STRATEGIC DEVELOPMENTS
- 2.3 DISRUPTIVE TRENDS SHAPING MARKET
- 2.4 HIGH-GROWTH SEGMENTS
- 2.5 SNAPSHOT: GLOBAL MARKET SIZE, GROWTH RATE, AND FORECAST
3 PREMIUM INSIGHTS
- 3.1 ATTRACTIVE OPPORTUNITIES FOR PLAYERS IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 3.2 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING
- 3.3 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE
- 3.4 IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE
- 3.5 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY
- 3.6 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE
- 3.7 IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE
- 3.8 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE
- 3.9 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL
- 3.10 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION
4 MARKET OVERVIEW
- 4.1 INTRODUCTION
- 4.2 MARKET DYNAMICS
- 4.2.1 DRIVERS
- 4.2.1.1 Rising instances of security breaches and identity-related fraud
- 4.2.1.2 Growth in awareness about compliance management
- 4.2.1.3 Cloud-centric transformation fuels need for unified access control
- 4.2.1.4 Increase in need for identity access management solutions for IoT
- 4.2.1.5 Growing adoption of IAM solutions by SMEs
- 4.2.2 RESTRAINTS
- 4.2.2.1 Lack of identity standards and budgetary constraints in deploying IAM solutions
- 4.2.2.2 Privacy concerns in IAM adoption
- 4.2.2.3 Complexity in integrating IAM with legacy systems
- 4.2.3 OPPORTUNITIES
- 4.2.3.1 Cultural shift from traditional IAM to customer identity and access management
- 4.2.3.2 Proliferation of cloud-based IAM solutions and services and growing adoption of hybrid cloud model
- 4.2.3.3 Increase in integration of technologies into IAM
- 4.2.3.4 Rise in demand for AI-driven and adaptive authentication solutions
- 4.2.4 CHALLENGES
- 4.2.4.1 Scarcity of skilled cybersecurity professionals among enterprises
- 4.2.4.2 Difficulties addressing complexity of advanced threats
- 4.2.4.3 Interoperability and integration issues across diverse IT environments
- 4.2.1 DRIVERS
- 4.3 UNMET NEEDS AND WHITE SPACES
- 4.4 INTERCONNECTED MARKETS AND CROSS-SECTOR OPPORTUNITIES
- 4.4.1 INTERCONNECTED MARKETS
- 4.4.2 CROSS SECTOR OPPORTUNITIES
- 4.5 STRATEGIC MOVES BY TIER -1/2/3 PLAYERS
- 4.5.1 TIER 1 PLAYERS (MARKET LEADERS)
- 4.5.1.1 Palo Alto Networks
- 4.5.1.2 Ping Identity
- 4.5.1.3 SailPoint
- 4.5.1.4 CyberArk
- 4.5.2 TIER 2 PLAYERS (STRONG CHALLENGERS)
- 4.5.2.1 Saviynt
- 4.5.2.2 Delinea (Thycotic + Centrify Merger)
- 4.5.2.3 Okta
- 4.5.3 TIER 3 PLAYERS (SPECIALISTS & EMERGING ENTRANTS)
- 4.5.3.1 Zilla
- 4.5.3.2 Princeps
- 4.5.4 CROSS-TIER STRATEGIC PATTERNS
- 4.5.5 MARKET IMPLICATIONS
- 4.5.5.1 Consolidation Pressure on Tier-3 Vendors
- 4.5.5.2 Acceleration Imperative for Tier-2 Challengers
- 4.5.5.3 Increased Complexity for Customers
- 4.5.5.4 Integration Burden Driving Platform Adoption
- 4.5.6 STRATEGIC TRENDS
- 4.5.6.1 Cloud-native and SaaS-first IAM solutions
- 4.5.6.2 Zero trust and adaptive security adoption
- 4.5.6.3 Integration of identity governance and PAM
- 4.5.1 TIER 1 PLAYERS (MARKET LEADERS)
5 INDUSTRY TRENDS
- 5.1 PORTER'S FIVE FORCES ANALYSIS
- 5.1.1 THREAT OF NEW ENTRANTS
- 5.1.2 BARGAINING POWER OF SUPPLIERS
- 5.1.3 BARGAINING POWER OF BUYERS
- 5.1.4 THREAT OF SUBSTITUTES
- 5.1.5 INTENSITY OF COMPETITIVE RIVALRY
- 5.2 MACROECONOMIC INDICATORS
- 5.2.1 INTRODUCTION
- 5.2.2 GDP TRENDS AND FORECAST
- 5.2.3 TRENDS IN GLOBAL ICT INDUSTRY
- 5.2.4 TRENDS IN GLOBAL CYBERSECURITY INDUSTRY
- 5.3 VALUE CHAIN ANALYSIS
- 5.3.1 OFFERINGS
- 5.3.2 PLANNING & DESIGNING
- 5.3.3 INFRASTRUCTURE DEPLOYMENT
- 5.3.4 SYSTEM INTEGRATION
- 5.3.5 CONSULTATION
- 5.3.6 END USERS
- 5.4 ECOSYSTEM ANALYSIS
- 5.5 PRICING ANALYSIS
- 5.5.1 AVERAGE SELLING PRICE OF KEY PLAYERS, BY OFFERING
- 5.5.2 INDICATIVE PRICING ANALYSIS, BY KEY PLAYERS
- 5.6 TRADE ANALYSIS
- 5.6.1 IMPORT SCENARIO (HS CODE 8471)
- 5.6.1.1 Overview of import values
- 5.6.1.2 Country-specific trends
- 5.6.1.3 Implications and conclusion
- 5.6.2 EXPORT SCENARIO (HS CODE 8471)
- 5.6.2.1 Overview of export values
- 5.6.2.2 Country-specific trends
- 5.6.2.3 Implications and conclusion
- 5.6.1 IMPORT SCENARIO (HS CODE 8471)
- 5.7 KEY CONFERENCES & EVENTS
- 5.8 TRENDS AND DISRUPTIONS IMPACTING CUSTOMER BUSINESS
- 5.9 INVESTMENT AND FUNDING SCENARIO
- 5.10 IDENTITY AND ACCESS MANAGEMENT MARKET FRAMEWORK
- 5.10.1 AUTHENTICATION SERVICES
- 5.10.2 USER MANAGEMENT SERVICES
- 5.10.3 AUTHORIZATION SERVICES
- 5.10.4 DIRECTORY SERVICES
- 5.10.5 GOVERNANCE FRAMEWORK
- 5.10.6 REPORTING & ANALYTICS
- 5.11 EVOLUTION OF IDENTITY AND ACCESS MANAGEMENT
- 5.11.1 EARLY BEGINNINGS
- 5.11.2 20TH CENTURY DEVELOPMENTS
- 5.11.3 DIGITAL IDENTITY EMERGENCE
- 5.11.4 INTERNET AND DIGITAL REVOLUTION
- 5.11.5 CLOUD AND MANAGED SERVICES
- 5.11.6 DECENTRALIZATION AND ADVANCED TECHNOLOGIES
- 5.11.7 MODERN DEVELOPMENTS AND FUTURE OUTLOOK
- 5.12 CASE STUDY ANALYSIS
- 5.12.1 PAMEIJER ADOPTED PING IDENTITY PLATFORM TO ACHIEVE SINGLE SIGN-ON (SSO) AND MULTI-FACTOR AUTHENTICATION (MFA) FOR EMPLOYEES AND CLIENTS
- 5.12.2 T-MOBILE ADOPTED OKTA IDENTITY CLOUD TO CONCENTRATE ON STRATEGIC GOALS SUCH AS CUTTING COSTS AND IMPROVING CUSTOMER SERVICE
- 5.12.3 WWK ESTABLISHED FORGEROCK-BASED SINGLE SIGN-ON FOR IMPROVED SERVICE AND SECURITY
- 5.12.4 AVANCER HELPED COMMUNITY HOSPITAL WITH SELF-SERVICE ADMINISTRATIVE IT FEATURES TO HELP AUTOMATE ACCESS GOVERNANCE
- 5.12.5 CAREPOINT HEALTH ENHANCES SECURITY AND BOOSTS PRODUCTIVITY WITH MICROSOFT AZURE AD
- 5.12.6 HORIZON REGIONAL HOSPITAL STRENGTHENS CYBERSECURITY AND ENSURES HIPAA COMPLIANCE WITH PALO ALTO NETWORKS
- 5.13 IMPACT OF 2025 US TARIFF - IDENTITY AND ACCESS MANAGEMENT SOLUTIONS MARKET
- 5.13.1 INTRODUCTION
- 5.13.2 KEY TARIFF RATES
- 5.13.3 PRICE IMPACT ANALYSIS
- 5.13.4 IMPACT ON COUNTRY/REGION
- 5.13.4.1 North America
- 5.13.4.2 Europe
- 5.13.4.3 Asia Pacific
- 5.13.5 IMPACT ON END-USE INDUSTRIES
6 TECHNOLOGICAL ADVANCEMENTS, AI-DRIVEN IMPACT, PATENTS, INNOVATIONS, AND FUTURE APPLICATIONS
- 6.1 KEY EMERGING TECHNOLOGIES
- 6.1.1 BIOMETRIC AUTHENTICATION
- 6.1.1.1 Facial recognition
- 6.1.1.2 Finger-vein recognition
- 6.1.1.3 Voice recognition
- 6.1.2 SINGLE SIGN-ON (SSO)
- 6.1.3 MULTI-FACTOR AUTHENTICATION (MFA)
- 6.1.4 IOT AUTHENTICATION
- 6.1.5 DECENTRALIZED IDENTITY (DID) AND SELF-SOVEREIGN IDENTITY (SSI)
- 6.1.1 BIOMETRIC AUTHENTICATION
- 6.2 COMPLEMENTARY TECHNOLOGIES
- 6.2.1 USER AND ENTITY BEHAVIOR ANALYTICS (UEBA)
- 6.2.2 ZERO TRUST SECURITY FRAMEWORK
- 6.2.3 ARTIFICIAL INTELLIGENCE AND MACHINE LEARNING (AI/ML) IN IAM
- 6.3 TECHNOLOGY/PRODUCT ROADMAP
- 6.3.1 SHORT-TERM (2025-2027) | FOUNDATION & EARLY COMMERCIALIZATION
- 6.3.2 MID-TERM (2027-2030) | SCALING, INTEGRATION & INTELLIGENT AUTOMATION
- 6.3.3 LONG-TERM (2030-2035+) | HYPER-AUTOMATION, QUANTUM READINESS & IDENTITY CONVERGENCE
- 6.4 PATENT ANALYSIS
- 6.5 FUTURE APPLICATIONS
- 6.5.1 AI-POWERED CONTEXTUAL ACCESS INTELLIGENCE
- 6.5.2 NEXT-GENERATION PASSWORDLESS & BIOMETRIC AUTHENTICATION
- 6.5.3 ZERO TRUST & CONTINUOUS AUTHENTICATION
- 6.5.4 DECENTRALIZED IDENTITY & BLOCKCHAIN IAM
- 6.5.5 IDENTITY GOVERNANCE FOR HYBRID/CLOUD ENVIRONMENTS
- 6.6 IMPACT OF AI/GEN AI ON IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.6.1 BEST PRACTICES IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.6.2 CASE STUDIES OF AI IMPLEMENTATION IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.6.3 INTERCONNECTED ADJACENT ECOSYSTEM AND IMPACT ON MARKET PLAYERS
- 6.6.4 CLIENTS' READINESS TO ADOPT GENERATIVE AI IN IDENTITY AND ACCESS MANAGEMENT MARKET
- 6.7 SUCCESS STORIES AND REAL-WORLD APPLICATIONS
- 6.7.1 OKTA: ADAPTIVE ACCESS & MFA DEPLOYMENT
- 6.7.2 MICROSOFT: ENTRA VERIFIED ID AT CONDATIS
7 REGULATORY LANDSCAPE
- 7.1 REGIONAL REGULATIONS AND COMPLIANCE
- 7.1.1 REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- 7.1.2 INDUSTRY STANDARDS
8 CONSUMER LANDSCAPE & BUYER BEHAVIOR
- 8.1 DECISION-MAKING PROCESS
- 8.2 BUYER STAKEHOLDERS AND BUYING EVALUATION CRITERIA
- 8.2.1 KEY STAKEHOLDERS IN BUYING PROCESS
- 8.2.2 BUYING CRITERIA
- 8.3 ADOPTION BARRIERS & INTERNAL CHALLENGES
- 8.4 UNMET NEEDS IN VARIOUS END-USE INDUSTRIES
- 8.5 MARKET PROFITABILITY
- 8.5.1 REVENUE POTENTIAL
- 8.5.2 COST DYNAMICS
- 8.5.3 MARGIN OPPORTUNITIES IN KEY APPLICATIONS
9 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING
- 9.1 INTRODUCTION
- 9.1.1 OFFERING: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 9.2 SOLUTIONS
- 9.2.1 RISING ADOPTION OF UNIFIED IDENTITY GOVERNANCE AND ZERO-TRUST FRAMEWORKS FUELS IAM MARKET EXPANSION
- 9.3 SERVICES
- 9.3.1 GROWING ENTERPRISE NEED FOR EXPERTISE AND CONTINUOUS IDENTITY OPERATIONS PROPEL MARKET GROWTH
- 9.3.2 PROFESSIONAL SERVICES
- 9.3.2.1 Surging demand for specialized IAM consulting to bolster market growth
- 9.3.2.1.1 Integration & deployment
- 9.3.2.1.2 Support & Maintenance
- 9.3.2.1.3 Consulting
- 9.3.2.1 Surging demand for specialized IAM consulting to bolster market growth
- 9.3.3 MANAGED IAM SERVICES
- 9.3.3.1 Rising need for 24/7 identity oversight and zero-trust enforcement to fuel market expansion
10 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY
- 10.1 INTRODUCTION
- 10.1.1 TECHNOLOGY: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 10.2 ACCESS MANAGEMENT
- 10.2.1 RISING NEED FOR SECURE AND SEAMLESS ACCESS CONTROLS TO DRIVE MARKET EXPANSION
- 10.2.1.1 Authentication & Access Control
- 10.2.1.2 Credential & Directory Services
- 10.2.1.3 Authorization
- 10.2.1.4 Session & Identity Federation
- 10.2.1 RISING NEED FOR SECURE AND SEAMLESS ACCESS CONTROLS TO DRIVE MARKET EXPANSION
- 10.3 IDENTITY GOVERNANCE & ADMINISTRATION (IGA)
- 10.3.1 INCREASING DIGITAL THREATS CATALYZING SECURE AND ADAPTIVE AUTHENTICATION SOLUTIONS
- 10.3.1.1 Identity Lifecycle Management
- 10.3.1.2 Governance & Compliance
- 10.3.1.3 Role & Entitlement Management
- 10.3.1.4 Analytics & Reporting
- 10.3.1 INCREASING DIGITAL THREATS CATALYZING SECURE AND ADAPTIVE AUTHENTICATION SOLUTIONS
- 10.4 PRIVILEGED ACCESS MANAGEMENT (PAM)
- 10.4.1 INCREASING THREATS FROM PRIVILEGED MISUSE TO DRIVE MARKET GROWTH
- 10.4.1.1 Credential Vaulting
- 10.4.1.2 Session Management & Recording
- 10.4.1.3 Just-In-Time (JIT) Privileged Access
- 10.4.1.4 Endpoint Privilege Management (EPM)
- 10.4.1.5 Privilege Analytics & Threat Detection
- 10.4.1 INCREASING THREATS FROM PRIVILEGED MISUSE TO DRIVE MARKET GROWTH
- 10.5 OTHER TECHNOLOGIES
11 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE
- 11.1 INTRODUCTION
- 11.1.1 TYPE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 11.2 WORKFORCE IAM
- 11.2.1 AI-DRIVEN WORKFORCE IDENTITY SECURITY TO STRENGTHEN ENTERPRISE RESILIENCE DRIVES MARKET
- 11.3 CONSUMER IAM
- 11.3.1 FRICTIONLESS, PRIVACY-FIRST CUSTOMER IDENTITY MANAGEMENT TO FUEL MARKET GROWTH
- 11.4 B2B IAM
- 11.4.1 FEDERATED B2B IDENTITY CONTROL TO STRENGTHEN ECOSYSTEM SECURITY
12 IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE
- 12.1 INTRODUCTION
- 12.1.1 IDENTITY TYPE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 12.2 HUMAN IDENTITY
- 12.2.1 FRICTIONLESS, ZERO-TRUST IDENTITY CONTROL FOR MODERN WORKFORCE AND CUSTOMERS
- 12.3 NON-HUMAN IDENTITY
- 12.3.1 ZERO-TRUST IDENTITY MANAGEMENT FOR WORKLOADS, DEVICES, AND AUTOMATED SYSTEMS
13 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT TYPE
- 13.1 INTRODUCTION
- 13.1.1 DEPLOYMENT MODE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 13.2 CLOUD
- 13.2.1 FLEXIBLE, COST-EFFICIENT CLOUD IAM ADOPTION ACROSS ENTERPRISES TO DRIVE MARKET
- 13.3 ON-PREMISES
- 13.3.1 SECURE, CUSTOMIZABLE ON-PREMISES IDENTITY INFRASTRUCTURE ADOPTION TO PROPEL MARKET GROWTH
- 13.4 HYBRID
- 13.4.1 HYBRID IDENTITY MODERNIZATION AND CROSS-ENVIRONMENT ACCESS CONTROL TO DRIVE MARKET
14 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL
- 14.1 INTRODUCTION
- 14.1.1 VERTICAL: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 14.2 BFSI
- 14.2.1 ELEVATING IDENTITY RESILIENCE TO ENSURE COMPLIANCE AND DRIVE SEAMLESS BANKING ADOPTION
- 14.3 TRAVEL, TOURISM, AND HOSPITALITY
- 14.3.1 SECURE, FRICTIONLESS IDENTITY EXPERIENCES TO TRANSFORM GLOBAL TRAVEL AND HOSPITALITY
- 14.4 HEALTHCARE
- 14.4.1 ENABLING SECURE, INTEROPERABLE, AND DIGITIZED CARE EXPERIENCES TO DRIVE MARKET
- 14.5 RETAIL & E-COMMERCE
- 14.5.1 ADVANCING OMNICHANNEL COMMERCE WITH TRUSTED, PERSONALIZED DIGITAL IDENTITY JOURNEYS
- 14.6 IT & ITES
- 14.6.1 DIGITAL-FIRST IT OPERATIONS REQUIRE STRONG IDENTITY GOVERNANCE TO FUEL GROWTH
- 14.7 EDUCATION
- 14.7.1 EVOLVING LEARNING ECOSYSTEMS DEMAND STRONG, SEAMLESS IDENTITY EXPERIENCES
- 14.8 GOVERNMENT & DEFENSE
- 14.8.1 DEFENSE-GRADE IDENTITY SECURITY TO SAFEGUARD NATIONAL SYSTEMS AND DRIVE MARKET
- 14.9 OTHER VERTICALS
15 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION
- 15.1 INTRODUCTION
- 15.2 NORTH AMERICA
- 15.2.1 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.2.2 US
- 15.2.2.1 Technology advancement and presence of key players to fuel market growth
- 15.2.3 CANADA
- 15.2.3.1 Rapid adoption of advanced AI- and ML-based identity verification solutions to boost growth
- 15.3 EUROPE
- 15.3.1 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.3.2 UK
- 15.3.2.1 Advancing IAM adoption through regulatory alignment and zero-trust transformation
- 15.3.3 GERMANY
- 15.3.3.1 Strong regulatory framework and industrial digitalization driving IAM market growth
- 15.3.4 FRANCE
- 15.3.4.1 Government digital identity initiatives and cybersecurity reforms accelerating IAM adoption
- 15.3.5 ITALY
- 15.3.5.1 Expansion of digital public services and regulatory modernization fueling IAM market growth
- 15.3.6 REST OF EUROPE
- 15.4 ASIA PACIFIC
- 15.4.1 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.4.2 CHINA
- 15.4.2.1 Expanding digital economy and national cybersecurity framework accelerating IAM adoption
- 15.4.3 JAPAN
- 15.4.3.1 Government digital initiatives and enterprise modernization driving IAM market growth
- 15.4.4 INDIA
- 15.4.4.1 National digital identity programs and enterprise adoption driving IAM growth
- 15.4.5 REST OF ASIA PACIFIC
- 15.5 MIDDLE EAST & AFRICA
- 15.5.1 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.5.2 GCC
- 15.5.2.1 Spike in demand for secure IAM solutions to support market growth
- 15.5.2.2 KSA
- 15.5.2.3 UAE
- 15.5.2.4 Rest of GCC countries
- 15.5.3 SOUTH AFRICA
- 15.5.3.1 Rising demand for advanced identity and access management solutions
- 15.5.4 REST OF MIDDLE EAST & AFRICA
- 15.6 LATIN AMERICA
- 15.6.1 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET DRIVERS
- 15.6.2 BRAZIL
- 15.6.2.1 Advancing identity and access management for secure, interoperable services
- 15.6.3 MEXICO
- 15.6.3.1 Expanding identity and access management for secure digital service
- 15.6.4 REST OF LATIN AMERICA
16 COMPETITIVE LANDSCAPE
- 16.1 OVERVIEW
- 16.2 KEY PLAYER STRATEGIES/RIGHT TO WIN
- 16.3 REVENUE ANALYSIS
- 16.4 MARKET SHARE ANALYSIS
- 16.5 BRAND COMPARISON
- 16.5.1 MICROSOFT
- 16.5.2 OKTA
- 16.5.3 PING IDENTITY
- 16.5.4 IBM
- 16.5.5 ORACLE
- 16.6 COMPANY VALUATION AND FINANCIAL METRICS
- 16.6.1 COMPANY VALUATION
- 16.6.2 FINANCIAL METRICS
- 16.7 COMPANY EVALUATION MATRIX: KEY PLAYERS, 2024
- 16.7.1 STARS
- 16.7.2 EMERGING LEADERS
- 16.7.3 PERVASIVE PLAYERS
- 16.7.4 PARTICIPANTS
- 16.7.5 COMPANY FOOTPRINT: KEY PLAYERS
- 16.7.5.1 Company footprint
- 16.7.5.2 Regional footprint
- 16.7.5.3 Deployment mode footprint
- 16.7.5.4 Technology footprint
- 16.7.5.5 Vertical footprint
- 16.8 COMPANY EVALUATION MATRIX: STARTUPS/SMES, 2024
- 16.8.1 PROGRESSIVE COMPANIES
- 16.8.2 RESPONSIVE COMPANIES
- 16.8.3 DYNAMIC COMPANIES
- 16.8.4 STARTING BLOCKS
- 16.8.5 COMPETITIVE BENCHMARKING: STARTUPS/SMES
- 16.8.5.1 Detailed list of key startups/SMEs
- 16.8.5.2 Competitive benchmarking of key startups/SMEs
- 16.8.5.2.1 Regional footprint
- 16.8.5.2.2 Deployment mode footprint
- 16.8.5.2.3 Technology footprint
- 16.8.5.2.4 Vertical footprint
- 16.9 COMPETITIVE SCENARIO AND TRENDS
- 16.9.1 PRODUCT LAUNCHES/ENHANCEMENTS
- 16.9.2 DEALS
17 COMPANY PROFILES
- 17.1 KEY PLAYERS
- 17.1.1 MICROSOFT
- 17.1.1.1 Business overview
- 17.1.1.2 Products/Solutions/Services offered
- 17.1.1.3 Recent developments
- 17.1.1.3.1 Product launches/enhancements
- 17.1.1.3.2 Deals
- 17.1.1.4 MnM view
- 17.1.1.4.1 Key strengths
- 17.1.1.4.2 Strategic choices
- 17.1.1.4.3 Weaknesses and competitive threats
- 17.1.2 PING IDENTITY
- 17.1.2.1 Business overview
- 17.1.2.2 Products/Solutions/Services offered
- 17.1.2.3 Recent developments
- 17.1.2.3.1 Product launches/enhancements
- 17.1.2.3.2 Deals
- 17.1.2.3.3 Expansions
- 17.1.2.4 MnM view
- 17.1.2.4.1 Key strengths
- 17.1.2.4.2 Strategic choices
- 17.1.2.4.3 Weaknesses and competitive threats
- 17.1.3 IBM
- 17.1.3.1 Business overview
- 17.1.3.2 Products/Solutions/Services offered
- 17.1.3.3 Recent developments
- 17.1.3.3.1 Product launches/enhancements
- 17.1.3.3.2 Deals
- 17.1.3.4 MnM view
- 17.1.3.4.1 Key strengths
- 17.1.3.4.2 Strategic choices
- 17.1.3.4.3 Weaknesses and competitive threats
- 17.1.4 OKTA
- 17.1.4.1 Business overview
- 17.1.4.2 Products/Solutions/Services offered
- 17.1.4.3 Recent developments
- 17.1.4.3.1 Product launches/enhancements
- 17.1.4.3.2 Deals
- 17.1.4.3.3 Expansions
- 17.1.4.4 MnM view
- 17.1.4.4.1 Key strengths
- 17.1.4.4.2 Strategic choices
- 17.1.4.4.3 Weaknesses and competitive threats
- 17.1.5 ORACLE
- 17.1.5.1 Business overview
- 17.1.5.2 Products/Solutions/Services offered
- 17.1.5.3 Recent developments
- 17.1.5.3.1 Product launches/enhancements
- 17.1.5.3.2 Deals
- 17.1.5.4 MnM view
- 17.1.5.4.1 Key strengths
- 17.1.5.4.2 Strategic choices
- 17.1.5.4.3 Weaknesses and competitive threats
- 17.1.6 SAILPOINT
- 17.1.6.1 Business overview
- 17.1.6.2 Products/Solutions/Services offered
- 17.1.6.3 Recent developments
- 17.1.6.3.1 Product launches/enhancements
- 17.1.6.3.2 Deals
- 17.1.6.3.3 Expansions
- 17.1.7 SAVIYNT
- 17.1.7.1 Business overview
- 17.1.7.2 Products/Solutions/Services offered
- 17.1.7.3 Recent developments
- 17.1.7.3.1 Product launches/enhancements
- 17.1.7.3.2 Deals
- 17.1.7.3.3 Expansions
- 17.1.8 CYBERARK
- 17.1.8.1 Business overview
- 17.1.8.2 Products/Solutions/Services offered
- 17.1.8.3 Recent developments
- 17.1.8.3.1 Product launches/enhancements
- 17.1.8.3.2 Deals
- 17.1.8.3.3 Expansions
- 17.1.9 THALES
- 17.1.9.1 Business overview
- 17.1.9.2 Products/Solutions/Services offered
- 17.1.9.3 Recent developments
- 17.1.9.3.1 Product launches/enhancements
- 17.1.9.3.2 Deals
- 17.1.9.3.3 Expansions
- 17.1.10 AKAMAI TECHNOLOGIES
- 17.1.10.1 Business overview
- 17.1.10.2 Products/Solutions/Services offered
- 17.1.10.3 Recent developments
- 17.1.10.3.1 Product launches/enhancements
- 17.1.10.3.2 Deals
- 17.1.10.3.3 Expansions
- 17.1.11 OPENTEXT
- 17.1.11.1 Business overview
- 17.1.11.2 Products/Solutions/Services offered
- 17.1.11.3 Recent developments
- 17.1.11.3.1 Product launches/enhancements
- 17.1.11.3.2 Deals
- 17.1.11.3.3 Expansions
- 17.1.12 ENTRUST
- 17.1.12.1 Business overview
- 17.1.12.2 Products/Solutions/Services offered
- 17.1.12.3 Recent developments
- 17.1.12.3.1 Product launches/enhancements
- 17.1.12.3.2 Deals
- 17.1.13 DUO SECURITY
- 17.1.13.1 Business overview
- 17.1.13.2 Products/Solutions/Services offered
- 17.1.13.3 Recent developments
- 17.1.13.3.1 Product launches/enhancements
- 17.1.14 HID GLOBAL
- 17.1.14.1 Business overview
- 17.1.14.2 Products/Solutions/Services offered
- 17.1.14.3 Recent developments
- 17.1.14.3.1 Product launches/enhancements
- 17.1.14.3.2 Deals
- 17.1.14.3.3 Expansions
- 17.1.15 EVIDIAN
- 17.1.15.1 Business overview
- 17.1.15.2 Products/Solutions/Services offered
- 17.1.15.3 Recent developments
- 17.1.15.3.1 Product launches/enhancements
- 17.1.15.3.2 Deals
- 17.1.1 MICROSOFT
- 17.2 OTHER KEY PLAYERS
- 17.2.1 RSA SECURITY
- 17.2.2 AVATIER
- 17.2.3 MANAGEENGINE
- 17.2.4 SECUREAUTH
- 17.2.5 EMPOWERID
- 17.2.6 SIMEIO
- 17.2.7 ONE IDENTITY
- 17.2.8 FUSIONAUTH
- 17.2.9 AUTH0
- 17.2.10 IDNOW
- 17.2.11 ZUORA
- 17.2.12 SIGNZY
- 17.2.13 CIVIC TECHNOLOGIES
- 17.2.14 TRUSONA
- 17.2.15 BEYOND IDENTITY
- 17.2.16 DELINEA
- 17.2.17 OPTIMAL IDM
- 17.2.18 NETWRIX
- 17.2.19 AQUERA
- 17.2.20 CERBY
- 17.2.21 TRAXION
- 17.2.22 RADIANT LOGIC
- 17.2.23 ELIMITY
- 17.2.24 OLERIA
- 17.2.25 VEZA
- 17.2.26 BRAVURA SECURITY
- 17.2.27 FISCHER IDENTITY
- 17.2.28 LUMOS
- 17.2.29 OMADA
- 17.2.30 OPENIAM
- 17.2.31 PATHLOCK
- 17.2.32 TUEBORA
- 17.2.33 RIPPLING
18 RESEARCH METHODOLOGY
- 18.1 RESEARCH DATA
- 18.1.1 SECONDARY DATA
- 18.1.2 PRIMARY DATA
- 18.1.2.1 Breakdown of primary profiles
- 18.1.2.2 Key industry insights
- 18.2 MARKET SIZE ESTIMATION
- 18.2.1 REVENUE ESTIMATES
- 18.3 DATA TRIANGULATION
- 18.4 FACTOR ANALYSIS
- 18.5 RESEARCH ASSUMPTIONS
- 18.6 RESEARCH LIMITATIONS
19 APPENDIX
- 19.1 DISCUSSION GUIDE
- 19.2 KNOWLEDGESTORE: MARKETSANDMARKETS' SUBSCRIPTION PORTAL
- 19.3 CUSTOMIZATION OPTIONS
- 19.4 RELATED REPORTS
- 19.5 AUTHOR DETAILS
List of Tables
- TABLE 1 INCLUSIONS & EXCLUSIONS
- TABLE 2 USD EXCHANGE RATES, 2020-2024
- TABLE 3 UNMET NEEDS AND WHITE SPACES IN IDENTITY AND ACCESS MANAGEMENT MARKET
- TABLE 4 STRATEGIC MOVES BY PLAYERS IN IDENTITY AND ACCESS MANAGEMENT MARKET
- TABLE 5 CROSS-TIER STRATEGIC PATTERNS OF VENDORS
- TABLE 6 PORTER'S FIVE FORCES' IMPACT ON IDENTITY AND ACCESS MANAGEMENT MARKET
- TABLE 7 GDP PERCENTAGE CHANGE, BY KEY COUNTRY, 2021-2030
- TABLE 8 IDENTITY AND ACCESS MANAGEMENT MARKET: ECOSYSTEM ANALYSIS
- TABLE 9 AVERAGE SELLING PRICE OF KEY PLAYERS, BY OFFERING, 2025 (USD)
- TABLE 10 INDICATIVE PRICING LEVELS OF IDENTITY AND ACCESS MANAGEMENT SOLUTIONS, BY KEY PLAYERS, 2025
- TABLE 11 IMPORT DATA FOR HS CODE 8471-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- TABLE 12 EXPORT DATA FOR HS CODE 8471-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- TABLE 13 IDENTITY AND ACCESS MANAGEMENT MARKET: DETAILED LIST OF CONFERENCES & EVENTS, 2025-2026
- TABLE 14 KEY TARIFF RATES
- TABLE 15 EXPECTED CHANGE IN PRICES AND LIKELY IMPACT ON END-USE MARKET DUE TO TARIFF IMPACT
- TABLE 16 LIST OF TOP PATENTS IN IDENTITY AND ACCESS MANAGEMENT MARKET, 2024-2025
- TABLE 17 TOP USE CASES AND MARKET POTENTIAL
- TABLE 18 BEST PRACTICES: COMPANIES IMPLEMENTING USE CASES
- TABLE 19 IDENTITY AND ACCESS MANAGEMENT SOLUTIONS MARKET: CASE STUDIES RELATED TO GEN AI IMPLEMENTATION
- TABLE 20 INTERCONNECTED ADJACENT ECOSYSTEM AND IMPACT ON MARKET PLAYERS
- TABLE 21 NORTH AMERICA: REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 22 EUROPE: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 23 ASIA PACIFIC: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 24 MIDDLE EAST & AFRICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 25 LATIN AMERICA: LIST OF REGULATORY BODIES, GOVERNMENT AGENCIES, AND OTHER ORGANIZATIONS
- TABLE 26 GLOBAL INDUSTRY STANDARDS IN IDENTITY AND ACCESS MANAGEMENT MARKET
- TABLE 27 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- TABLE 28 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- TABLE 29 UNMET NEEDS IN IDENTITY AND ACCESS MANAGEMENT MARKET BY END-USE INDUSTRY
- TABLE 30 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 31 IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 32 IDENTITY AND ACCESS MANAGEMENT SOLUTIONS MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 33 IDENTITY AND ACCESS MANAGEMENT SOLUTIONS MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 34 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 35 IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 36 IDENTITY AND ACCESS MANAGEMENT SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 37 IDENTITY AND ACCESS MANAGEMENT SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 38 IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 39 IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 40 PROFESSIONAL IAM SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 41 PROFESSIONAL IAM SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 42 IAM INTEGRATION & DEPLOYMENT SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 43 IAM INTEGRATION & DEPLOYMENT SERVICES, BY REGION, 2025-2030 (USD MILLION)
- TABLE 44 IAM SUPPORT & MAINTENANCE SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 45 IAM SUPPORT & MAINTENANCE SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 46 CONSULTING IAM SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 47 CONSULTING IAM SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 48 MANAGED IAM SERVICES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 49 MANAGED IAM SERVICES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 50 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 51 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 52 ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 53 ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 54 ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 55 ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 56 IDENTITY GOVERNANCE & ADMINISTRATION (IGA) MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 57 IDENTITY GOVERNANCE & ADMINISTRATION (IGA) MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 58 IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 59 IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 60 PRIVILEGED ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 61 PRIVILEGED ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 62 PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 63 PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 64 OTHER IDENTITY AND ACCESS MANAGEMENT TECHNOLOGIES MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 65 OTHER IDENTITY AND ACCESS MANAGEMENT TECHNOLOGIES MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 66 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 67 IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 68 WORKFORCE IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 69 WORKFORCE IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 70 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 71 CONSUMER IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 72 B2B IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 73 B2B IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 74 IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 75 IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 76 HUMAN IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 77 HUMAN IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 78 NON-HUMAN IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 79 NON-HUMAN IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 80 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 81 IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 82 CLOUD-BASED IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 83 CLOUD-BASED IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 84 ON-PREMISE IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 85 ON-PREMISE IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 86 HYBRID IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 87 HYBRID IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 88 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 89 IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 90 IDENTITY AND ACCESS MANAGEMENT MARKET IN BFSI, BY REGION, 2019-2024 (USD MILLION)
- TABLE 91 IDENTITY AND ACCESS MANAGEMENT MARKET IN BFSI, BY REGION, 2025-2030 (USD MILLION)
- TABLE 92 IDENTITY AND ACCESS MANAGEMENT MARKET IN TRAVEL, TOURISM, AND HOSPITALITY, BY REGION, 2019-2024 (USD MILLION)
- TABLE 93 IDENTITY AND ACCESS MANAGEMENT MARKET IN TRAVEL, TOURISM, AND HOSPITALITY, BY REGION, 2025-2030 (USD MILLION)
- TABLE 94 IDENTITY AND ACCESS MANAGEMENT MARKET IN HEALTHCARE, BY REGION, 2019-2024 (USD MILLION)
- TABLE 95 IDENTITY AND ACCESS MANAGEMENT MARKET IN HEALTHCARE, BY REGION, 2025-2030 (USD MILLION)
- TABLE 96 IDENTITY AND ACCESS MANAGEMENT MARKET IN RETAIL & ECOMMERCE, BY REGION, 2019-2024 (USD MILLION)
- TABLE 97 IDENTITY AND ACCESS MANAGEMENT MARKET IN RETAIL & ECOMMERCE, BY REGION, 2025-2030 (USD MILLION)
- TABLE 98 IDENTITY AND ACCESS MANAGEMENT IN IT & ITES, BY REGION, 2019-2024 (USD MILLION)
- TABLE 99 IDENTITY AND ACCESS MANAGEMENT IN IT & ITES, BY REGION, 2025-2030 (USD MILLION)
- TABLE 100 IDENTITY AND ACCESS MANAGEMENT MARKET IN EDUCATION, BY REGION, 2019-2024 (USD MILLION)
- TABLE 101 IDENTITY AND ACCESS MANAGEMENT MARKET IN EDUCATION, BY REGION, 2025-2030 (USD MILLION)
- TABLE 102 IDENTITY AND ACCESS MANAGEMENT MARKET IN GOVERNMENT & DEFENSE, BY REGION, 2019-2024 (USD MILLION)
- TABLE 103 IDENTITY AND ACCESS MANAGEMENT MARKET IN GOVERNMENT & DEFENSE, BY REGION, 2025-2030 (USD MILLION)
- TABLE 104 IDENTITY AND ACCESS MANAGEMENT MARKET IN OTHER VERTICALS, BY REGION, 2019-2024 (USD MILLION)
- TABLE 105 IDENTITY AND ACCESS MANAGEMENT MARKET IN OTHER VERTICALS, BY REGION, 2025-2030 (USD MILLION)
- TABLE 106 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2019-2024 (USD MILLION)
- TABLE 107 IDENTITY AND ACCESS MANAGEMENT MARKET, BY REGION, 2025-2030 (USD MILLION)
- TABLE 108 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 109 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 110 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 111 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 112 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 113 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 114 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 115 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 116 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 117 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 118 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 119 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 120 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 121 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 122 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 123 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 124 NORTH AMERICA: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 125 NORTH AMERICA: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 126 NORTH AMERICA: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 127 NORTH AMERICA: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 128 NORTH AMERICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 129 NORTH AMERICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 130 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 131 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 132 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 133 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 134 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 135 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 136 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 137 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 138 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 139 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 140 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 141 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 142 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 143 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 144 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 145 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 146 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 147 US: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 148 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 149 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 150 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 151 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 152 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 153 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 154 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 155 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 156 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 157 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 158 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 159 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 160 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 161 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 162 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 163 CANADA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 164 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 165 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 166 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 167 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 168 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 169 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 170 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 171 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 172 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 173 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 174 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 175 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 176 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 177 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 178 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 179 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 180 EUROPE: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 181 EUROPE: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 182 EUROPE: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 183 EUROPE: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 184 EUROPE: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 185 EUROPE: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 186 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 187 EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 188 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 189 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 190 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 191 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 192 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 193 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 194 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 195 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 196 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 197 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 198 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 199 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 200 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 201 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 202 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 203 UK: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 204 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 205 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 206 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 207 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 208 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 209 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 210 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 211 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 212 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 213 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 214 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 215 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 216 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 217 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 218 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 219 GERMANY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 220 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 221 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 222 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 223 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICES, 2025-2030 (USD MILLION)
- TABLE 224 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 225 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 226 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 227 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 228 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 229 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 230 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 231 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 232 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 233 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 234 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 235 FRANCE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 236 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 237 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 238 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 239 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 240 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 241 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 242 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 243 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 244 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 245 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 246 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 247 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 248 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 249 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 250 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 251 ITALY: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 252 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 253 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 254 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 255 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 256 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 257 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 258 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 259 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 260 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 261 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 262 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 263 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 264 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 265 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 266 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 267 REST OF EUROPE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 268 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 269 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 270 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 271 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 272 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 273 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 274 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 275 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 276 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 277 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 278 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 279 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 280 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 281 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 282 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 283 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 284 ASIA PACIFIC: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 285 ASIA PACIFIC: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 286 ASIA PACIFIC: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 287 ASIA PACIFIC: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 288 ASIA PACIFIC: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 289 ASIA PACIFIC: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 290 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 291 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 292 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 293 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 294 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 295 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 296 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 297 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 298 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 299 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 300 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 301 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 302 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 303 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 304 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 305 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 306 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 307 CHINA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 308 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 309 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 310 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 311 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 312 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 313 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 314 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 315 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 316 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 317 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 318 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 319 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 320 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 321 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 322 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 323 JAPAN: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 324 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 325 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 326 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 327 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 328 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 329 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 330 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 331 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 332 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 333 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 334 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 335 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 336 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 337 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 338 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 339 INDIA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 340 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 341 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 342 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 343 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 344 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 345 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 346 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 347 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 348 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 349 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 350 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 351 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 352 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 353 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 354 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 355 REST OF ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 356 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 357 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 358 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 359 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 360 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 361 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 362 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 363 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 364 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 365 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 366 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 367 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 368 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 369 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 370 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 371 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 372 MIDDLE EAST & AFRICA: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 373 MIDDLE EAST & AFRICA: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 374 MIDDLE EAST & AFRICA: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 375 MIDDLE EAST & AFRICA: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 376 MIDDLE EAST & AFRICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 377 MIDDLE EAST & AFRICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 378 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY/REGION, 2019-2024 (USD MILLION)
- TABLE 379 MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY/REGION, 2025-2030 (USD MILLION)
- TABLE 380 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 381 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 382 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 383 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 384 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 385 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 386 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 387 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 388 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 389 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 390 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 391 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 392 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 393 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 394 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 395 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 396 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 397 GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 398 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 399 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 400 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 401 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 402 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 403 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 404 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 405 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 406 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 407 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 408 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 409 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 410 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 411 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 412 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 413 KSA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 414 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 415 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 416 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 417 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 418 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 419 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 420 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 421 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 422 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 423 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 424 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 425 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 426 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 427 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 428 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 429 UAE: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 430 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 431 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 432 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 433 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 434 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 435 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 436 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 437 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 438 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 439 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 440 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 441 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 442 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 443 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 444 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 445 REST OF GCC: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 446 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 447 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 448 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 449 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICES, 2025-2030 (USD MILLION)
- TABLE 450 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICES, 2019-2024 (USD MILLION)
- TABLE 451 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 452 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 453 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 454 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 455 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 456 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 457 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 458 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 459 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 460 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 461 SOUTH AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 462 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 463 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 464 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 465 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 466 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 467 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICES, 2025-2030 (USD MILLION)
- TABLE 468 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 469 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 470 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 471 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 472 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 473 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 474 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 475 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 476 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 477 REST OF MIDDLE EAST & AFRICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 478 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 479 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 480 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 481 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 482 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 483 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 484 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 485 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 486 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 487 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 488 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 489 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 490 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 491 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 492 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 493 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 494 LATIN AMERICA: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 495 LATIN AMERICA: ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 496 LATIN AMERICA: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 497 LATIN AMERICA: IDENTITY GOVERNANCE & ADMINISTRATION MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 498 LATIN AMERICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 499 LATIN AMERICA: PRIVILEGED ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 500 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2019-2024 (USD MILLION)
- TABLE 501 LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY COUNTRY, 2025-2030 (USD MILLION)
- TABLE 502 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 503 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 504 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 505 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 506 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 507 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 508 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 509 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 510 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 511 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 512 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 513 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 514 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 515 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 516 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 517 BRAZIL: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 518 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 519 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 520 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 521 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 522 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 523 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 524 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 525 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 526 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 527 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 528 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 529 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 530 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 531 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 532 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 533 MEXICO: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 534 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2019-2024 (USD MILLION)
- TABLE 535 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY OFFERING, 2025-2030 (USD MILLION)
- TABLE 536 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2019-2024 (USD MILLION)
- TABLE 537 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY SERVICE, 2025-2030 (USD MILLION)
- TABLE 538 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2019-2024 (USD MILLION)
- TABLE 539 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY PROFESSIONAL SERVICE, 2025-2030 (USD MILLION)
- TABLE 540 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2019-2024 (USD MILLION)
- TABLE 541 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TECHNOLOGY, 2025-2030 (USD MILLION)
- TABLE 542 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2019-2024 (USD MILLION)
- TABLE 543 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY TYPE, 2025-2030 (USD MILLION)
- TABLE 544 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2019-2024 (USD MILLION)
- TABLE 545 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY IDENTITY TYPE, 2025-2030 (USD MILLION)
- TABLE 546 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2019-2024 (USD MILLION)
- TABLE 547 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY DEPLOYMENT MODE, 2025-2030 (USD MILLION)
- TABLE 548 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2019-2024 (USD MILLION)
- TABLE 549 REST OF LATIN AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET, BY VERTICAL, 2025-2030 (USD MILLION)
- TABLE 550 IDENTITY AND ACCESS MANAGEMENT MARKET: DEGREE OF COMPETITION
- TABLE 551 IDENTITY AND ACCESS MANAGEMENT MARKET: REGIONAL FOOTPRINT, 2024
- TABLE 552 IDENTITY AND ACCESS MANAGEMENT MARKET: DEPLOYMENT MODE FOOTPRINT, 2024
- TABLE 553 IDENTITY AND ACCESS MANAGEMENT MARKET: TECHNOLOGY FOOTPRINT, 2024
- TABLE 554 IDENTITY AND ACCESS MANAGEMENT MARKET: VERTICAL FOOTPRINT, 2024
- TABLE 555 IDENTITY AND ACCESS MANAGEMENT: KEY STARTUPS/SMES
- TABLE 556 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY REGION, 2024
- TABLE 557 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY DEPLOYMENT MODE, 2024
- TABLE 558 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY TECHNOLOGY, 2024
- TABLE 559 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPETITIVE BENCHMARKING OF KEY STARTUPS/SMES, BY VERTICAL
- TABLE 560 IDENTITY AND ACCESS MANAGEMENT MARKET: PRODUCT LAUNCHES/ENHANCEMENTS, JANUARY 2023-NOVEMBER 2025
- TABLE 561 IDENTITY AND ACCESS MANAGEMENT MARKET: DEALS, JANUARY 2023-NOVEMBER 2025
- TABLE 562 MICROSOFT: COMPANY OVERVIEW
- TABLE 563 MICROSOFT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 564 MICROSOFT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 565 MICROSOFT: DEALS
- TABLE 566 PING IDENTITY: COMPANY OVERVIEW
- TABLE 567 PING IDENTITY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 568 PING IDENTITY: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 569 PING IDENTITY: DEALS
- TABLE 570 PING IDENTITY: EXPANSIONS
- TABLE 571 IBM: COMPANY OVERVIEW
- TABLE 572 IBM: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 573 IBM: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 574 IBM: DEALS
- TABLE 575 OKTA: COMPANY OVERVIEW
- TABLE 576 OKTA: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 577 OKTA: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 578 OKTA: DEALS
- TABLE 579 OKTA: EXPANSIONS
- TABLE 580 ORACLE: COMPANY OVERVIEW
- TABLE 581 ORACLE: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 582 ORACLE: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 583 ORACLE: DEALS
- TABLE 584 SAILPOINT: COMPANY OVERVIEW
- TABLE 585 SAILPOINT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 586 SAILPOINT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 587 SAILPOINT: DEALS
- TABLE 588 SAILPOINT: EXPANSIONS
- TABLE 589 SAVIYNT: COMPANY OVERVIEW
- TABLE 590 SAVIYNT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 591 SAVIYNT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 592 SAVIYNT: DEALS
- TABLE 593 SAVIYNT: EXPANSIONS
- TABLE 594 CYBERARK: COMPANY OVERVIEW
- TABLE 595 CYBERARK: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 596 CYBERARK: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 597 CYBERARK: DEALS
- TABLE 598 CYBERARK: EXPANSIONS
- TABLE 599 THALES: COMPANY OVERVIEW
- TABLE 600 THALES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 601 THALES: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 602 THALES: DEALS
- TABLE 603 THALES: EXPANSIONS
- TABLE 604 AKAMAI TECHNOLOGIES: COMPANY OVERVIEW
- TABLE 605 AKAMAI TECHNOLOGIES: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 606 AKAMAI TECHNOLOGIES: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 607 AKAMAI TECHNOLOGIES: DEALS
- TABLE 608 AKAMAI TECHNOLOGIES: EXPANSIONS
- TABLE 609 OPENTEXT: COMPANY OVERVIEW
- TABLE 610 OPENTEXT: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 611 OPENTEXT: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 612 OPENTEXT: DEALS
- TABLE 613 OPENTEXT: EXPANSIONS
- TABLE 614 ENTRUST: COMPANY OVERVIEW
- TABLE 615 ENTRUST: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 616 ENTRUST: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 617 ENTRUST: DEALS
- TABLE 618 DUO SECURITY: COMPANY OVERVIEW
- TABLE 619 DUO SECURITY: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 620 DUO SECURITY: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 621 HID GLOBAL: COMPANY OVERVIEW
- TABLE 622 HID GLOBAL: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 623 HID GLOBAL: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 624 HID GLOBAL: DEALS
- TABLE 625 HID GLOBAL: EXPANSIONS
- TABLE 626 EVIDIAN: COMPANY OVERVIEW
- TABLE 627 EVIDIAN: PRODUCTS/SOLUTIONS/SERVICES OFFERED
- TABLE 628 EVIDIAN: PRODUCT LAUNCHES/ENHANCEMENTS
- TABLE 629 EVIDIAN: DEALS
- TABLE 630 FACTOR ANALYSIS
List of Figures
- FIGURE 1 IDENTITY AND ACCESS MANAGEMENT MARKET SEGMENTATION
- FIGURE 2 STUDY YEARS CONSIDERED
- FIGURE 3 MARKET SCENARIO
- FIGURE 4 GLOBAL IDENTITY AND ACCESS MANAGEMENT MARKET, 2019-2030 (USD MILLION)
- FIGURE 5 MAJOR STRATEGIES ADOPTED BY KEY PLAYERS IN IDENTITY AND ACCESS MANAGEMENT MARKET, 2019-2025
- FIGURE 6 DISRUPTIVE TRENDS IMPACTING GROWTH OF IDENTITY AND ACCESS MANAGEMENT MARKET
- FIGURE 7 HIGH-GROWTH SEGMENTS IN IDENTITY AND ACCESS MANAGEMENT MARKET, 2025
- FIGURE 8 ASIA PACIFIC TO REGISTER HIGHEST GROWTH DURING FORECAST PERIOD
- FIGURE 9 COMPREHENSIVE ACCESS CONTROL AND AI-ENABLED AUTHENTICATION CONTINUE TO DRIVE IDENTITY AND ACCESS MANAGEMENT MARKET
- FIGURE 10 IDENTITY AND ACCESS MANAGEMENT SOLUTIONS TO ACCOUNT FOR LARGER MARKET SHARE DURING FORECAST PERIOD
- FIGURE 11 PROFESSIONAL SERVICES TO ACCOUNT FOR LARGER MARKET SHARE DURING FORECAST PERIOD
- FIGURE 12 INTEGRATION AND DEPLOYMENT TO HOLD SIGNIFICANT SHARE DURING FORECAST PERIOD
- FIGURE 13 ACCESS MANAGEMENT TO ACCOUNT FOR SIGNIFICANT SHARE DURING FORECAST PERIOD
- FIGURE 14 CONSUMER IAM SEGMENT TO ACCOUNT FOR LARGEST SHARE DURING FORECAST PERIOD
- FIGURE 15 HUMAN IDENTITY AND ACCESS MANAGEMENT TO ACCOUNT FOR SIGNIFICANT SHARE DURING FORECAST PERIOD
- FIGURE 16 CLOUD DEPLOYMENT TO ACCOUNT FOR SIGNIFICANT SHARE DURING FORECAST PERIOD
- FIGURE 17 BFSI TO HOLD SIGNIFICANT SHARE DURING FORECAST PERIOD
- FIGURE 18 NORTH AMERICA TO EMERGE AS MOST SIGNIFICANT MARKET FOR NEXT FIVE YEARS
- FIGURE 19 IDENTITY AND ACCESS MANAGEMENT MARKET: DRIVERS, RESTRAINTS, OPPORTUNITIES, AND CHALLENGES
- FIGURE 20 TOP IDENTITY THEFT REPORT CATEGORIES, 2025 (USD THOUSAND)
- FIGURE 21 IDENTITY AND ACCESS MANAGEMENT MARKET: PORTER'S FIVE FORCES ANALYSIS
- FIGURE 22 IDENTITY AND ACCESS MANAGEMENT MARKET: VALUE CHAIN
- FIGURE 23 ECOSYSTEM: IDENTITY AND ACCESS MANAGEMENT MARKET
- FIGURE 24 AVERAGE SELLING PRICE OF KEY PLAYERS, BY OFFERING, 2025 (USD)
- FIGURE 25 IMPORT DATA FOR HS CODE 8471-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- FIGURE 26 EXPORT DATA FOR HS CODE 8471-COMPLIANT PRODUCTS, BY COUNTRY, 2020-2024 (USD MILLION)
- FIGURE 27 TRENDS/DISRUPTIONS INFLUENCING CUSTOMER BUSINESS
- FIGURE 28 LEADING GLOBAL IDENTITY AND ACCESS MANAGEMENT STARTUPS AND SMES BY NUMBER OF INVESTORS AND NUMBER OF FUNDING ROUNDS
- FIGURE 29 IDENTITY AND ACCESS MANAGEMENT SERVICE COMPONENTS
- FIGURE 30 HISTORICAL KEY MILESTONES IN IDENTITY AND ACCESS MANAGEMENT
- FIGURE 31 PATENTS GRANTED IN IDENTITY AND ACCESS MANAGEMENT MARKET, 2015-2025
- FIGURE 32 REGIONAL ANALYSIS OF PATENTS GRANTED IN IDENTITY AND ACCESS MANAGEMENT MARKET
- FIGURE 33 FUTURE APPLICATIONS OF IDENTITY AND ACCESS MANAGEMENT
- FIGURE 34 IDENTITY AND ACCESS MANAGEMENT MARKET: DECISION-MAKING FACTORS
- FIGURE 35 INFLUENCE OF STAKEHOLDERS ON BUYING PROCESS FOR TOP THREE VERTICALS
- FIGURE 36 KEY BUYING CRITERIA FOR TOP THREE VERTICALS
- FIGURE 37 ADOPTION BARRIERS AND INTERNAL CHALLENGES
- FIGURE 38 SERVICES SEGMENT TO REGISTER HIGHER CAGR DURING FORECAST PERIOD
- FIGURE 39 MANAGED IAM SERVICES SEGMENT TO REGISTER HIGHER CAGR THAN PROFESSIONAL SERVICES SEGMENT DURING FORECAST PERIOD
- FIGURE 40 INTEGRATION & DEPLOYMENT SEGMENT TO ACHIEVE HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 41 ACCESS MANAGEMENT SEGMENT TO DOMINATE MARKET IN TERMS OF MARKET SIZE DURING FORECAST PERIOD
- FIGURE 42 CONSUMER IAM SEGMENT TO ACCOUNT FOR LARGER MARKET DURING FORECAST PERIOD
- FIGURE 43 HUMAN IDENTITY SEGMENT TO ACCOUNT FOR LARGER MARKET DURING FORECAST PERIOD
- FIGURE 44 HYBRID SEGMENT TO ACCOUNT FOR HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 45 BFSI SEGMENT TO ACCOUNT FOR LARGEST MARKET BY 2030
- FIGURE 46 ASIA PACIFIC TO REGISTER HIGHEST CAGR DURING FORECAST PERIOD
- FIGURE 47 NORTH AMERICA: IDENTITY AND ACCESS MANAGEMENT MARKET SNAPSHOT
- FIGURE 48 ASIA PACIFIC: IDENTITY AND ACCESS MANAGEMENT MARKET SNAPSHOT
- FIGURE 49 SEGMENTAL REVENUE ANALYSIS OF KEY MARKET PLAYERS, 2020-2024 (USD MILLION)
- FIGURE 50 SHARE OF LEADING COMPANIES IN IDENTITY AND ACCESS MANAGEMENT MARKET
- FIGURE 51 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPARISON OF VENDORS' BRANDS
- FIGURE 52 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPANY VALUATION OF KEY VENDORS, 2025 (USD BILLION)
- FIGURE 53 IDENTITY AND ACCESS MANAGEMENT MARKET: FINANCIAL METRICS, 2025
- FIGURE 54 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPANY EVALUATION MATRIX (KEY PLAYERS), 2024
- FIGURE 55 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPANY FOOTPRINT, 2024
- FIGURE 56 IDENTITY AND ACCESS MANAGEMENT MARKET: COMPANY EVALUATION MATRIX (STARTUPS/SMES), 2024
- FIGURE 57 MICROSOFT: COMPANY SNAPSHOT
- FIGURE 58 IBM: COMPANY SNAPSHOT
- FIGURE 59 OKTA: COMPANY SNAPSHOT
- FIGURE 60 ORACLE: COMPANY SNAPSHOT
- FIGURE 61 SAILPOINT: COMPANY SNAPSHOT
- FIGURE 62 CYBERARK: COMPANY SNAPSHOT
- FIGURE 63 THALES: COMPANY SNAPSHOT
- FIGURE 64 AKAMAI TECHNOLOGIES: COMPANY SNAPSHOT
- FIGURE 65 OPENTEXT: COMPANY SNAPSHOT
- FIGURE 66 IDENTITY AND ACCESS MANAGEMENT MARKET: RESEARCH DESIGN
- FIGURE 67 BREAKDOWN OF PRIMARY PROFILES, BY COMPANY TYPE, DESIGNATION, AND REGION
- FIGURE 68 KEY INDUSTRY INSIGHTS
- FIGURE 69 IDENTITY AND ACCESS MANAGEMENT MARKET: RESEARCH FLOW
- FIGURE 70 APPROACH 1 (SUPPLY-SIDE ANALYSIS): REVENUE OF SOLUTIONS AND SERVICES IN IDENTITY AND ACCESS MANAGEMENT MARKET
- FIGURE 71 APPROACH 1 (SUPPLY-SIDE ANALYSIS): MARKET SIZE ESTIMATION METHODOLOGY
- FIGURE 72 APPROACH 2 (BOTTOM-UP, SUPPLY SIDE): COLLECTIVE REVENUE FROM ALL SOLUTIONS IN IDENTITY AND ACCESS MANAGEMENT MARKET
- FIGURE 73 TOP-DOWN APPROACH (DEMAND-SIDE ANALYSIS): MARKET SIZE ESTIMATION METHODOLOGY
- FIGURE 74 DATA TRIANGULATION
- FIGURE 75 RESEARCH LIMITATIONS










